How does Nokia’s Fabric Services System use a fabric intent to build the DC switch fabric?
Which of the following is NOT how prefixes are typically learned and advertised in a leaf and spine data center?
Which of the following statements about the CLI modes in Nokia’s SR Linux is FALSE?
Which of the following statements about the YANG model used in Nokia’s SR Linux is FALSE?
Which of the following statements about IP-VRFs in Nokia’s SR Linux is FALSE?
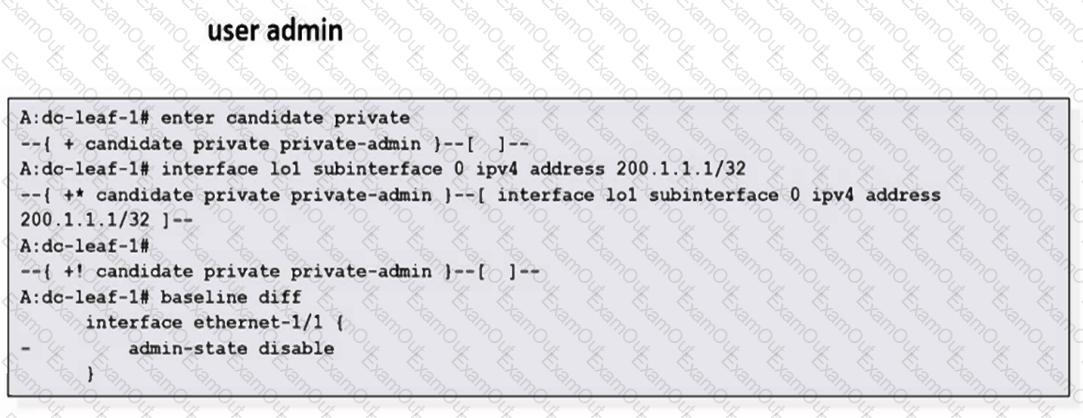
Based on the exhibit output, which of the following is NOT the reason the user runs the “baseline diff” command?
Which of the following statements about the data center’s leaf-spine topology (clos network) is FALSE?
Which of the following is NOT one of the characteristics of Nokia’s SR Linux?
Which of the following statements about SR Linux interfaces is FALSE?
Which of the following statements about a CPM-filter policer is FALSE?

