How does a cloud security solution achieve visibility into TLS/SSL-protected Web traffic?
You want to prevent Man-in-the-Middle (MITM) attacks on an encrypted website or application. In this scenario, which method would you use?
Your company has implemented Netskope's Cloud Firewall and requires that all FTP connections are blocked regardless of the ports being used.
Which two statements correctly identify how to block FTP access? (Choose two.)
What are two benefits of creating a policy group as a logical collection of Real-time Protection policies? (Choose two.)
Click the Exhibit button.
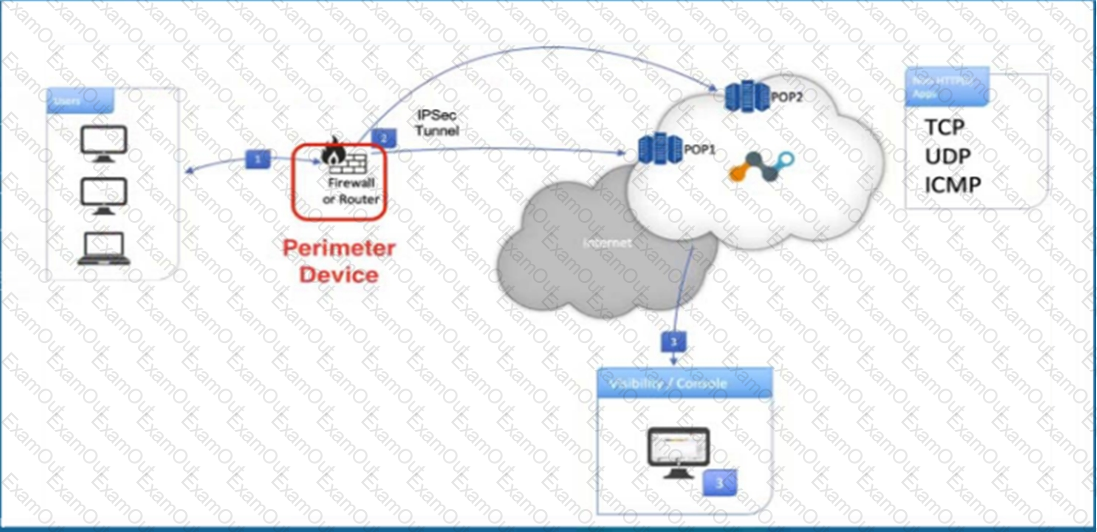
Referring to the exhibit, what are two recommended steps to be set on the perimeter device to monitor IPsec tunnels to a Netskope data plane? (Choose two.)
What are two use cases for Netskope's DLP solution? (Choose two.)
You are asked to review files affected by malware in your organization. In this scenario, which two actions are possible and would be accessible from the Netskope UI -> Incidents --> Malware? (Choose two)
Which three statements are correct about Netskope's NewEdge Security Cloud Network Infrastructure? (Choose three.)
You have an issue with the Netskope client connecting to the tenant.
In this scenario, what are two ways to collect the logs from the client machine? (Choose two.)
As an administrator, you are investigating an increase in the number of incidents related to compromised credentials. You are using the Netskope Compromised Credentials feature on your tenant to assess the situation. Which insights would you find when using this feature? (Choose two)

