Exhibit
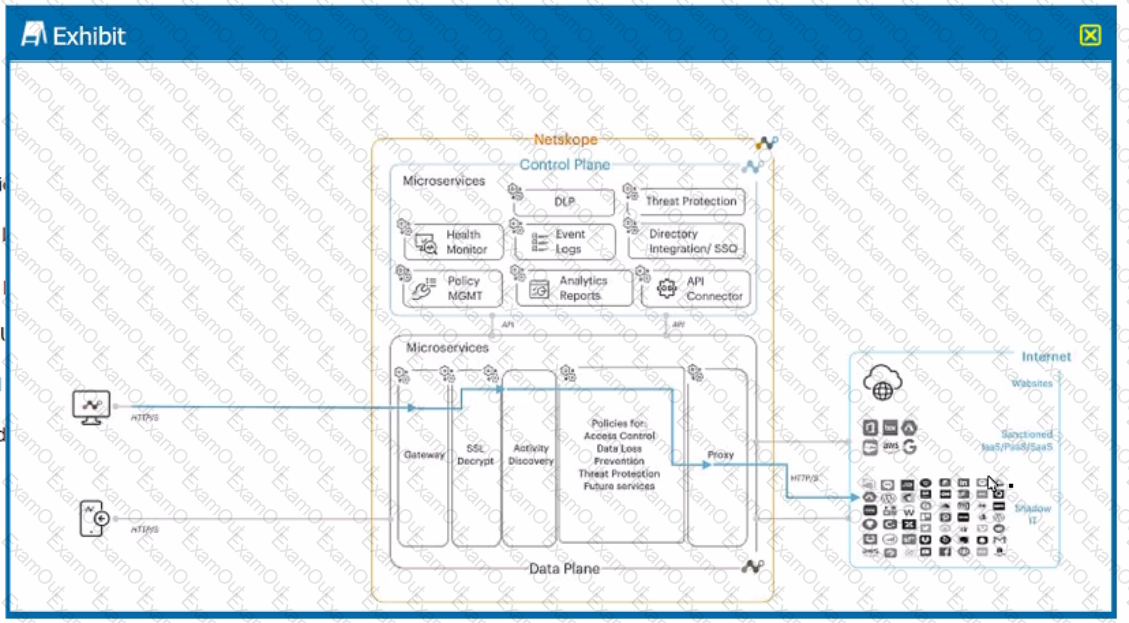
A user is connected to a cloud application through Netskope's proxy.
In this scenario, what information is available at Skope IT? (Choose three.)
When comparing data in motion with data at rest, which statement is correct?
You want to enable Netskope to gain visibility into your users' cloud application activities in an inline mode.
In this scenario, which two deployment methods would match your inline use case? (Choose two.)
In the Skope IT interface, which two event tables would be used to label a cloud application instance? (Choose two.)
You need to provide a quick view under the Skope IT Applications page showing only risky shadow IT cloud applications being used.
In this scenario, which two filter combinations would you use to accomplish this task? (Choose two.)
In the Tenant III, which two methods would an administrator use to update a File Profile with malicious file hashes? (Choose two)
What are two valid use cases for the Cloud Confidence Index (CCI)? (Choose two.)
What are two characteristics of Netskope's Private Access Solution? (Choose two.)

