You want to add your NetApp StorageGRID embedded Prometheus instance as a data source to Grafana.What must be done to accomplish this task?
Your customer is running their Kafka and Spark applications inside a Kubernetes cluster. They want to create a single backup policy within Astra to automate the backup of both applications and all their related Kubernetes objects at the same time.
Which method in Kubernetes should be used to accomplish this task?
You are asked to administer your NetApp Cloud Central account settings to manage users, service accounts, workspaces, connectors, and subscriptions.
In this scenario, which REST API would you access?
You recently started at a new company where the persistent storage for Kubernetes was not provided by NetApp. You want to make sure you take full advantage of the additional annotations available from your NetApp storage.
In this scenario, which three parameters would you use to accomplish this task? (Choose three.)
You configured your NetApp Cloud Volumes ONTAP instance to protect your data against ransomware. A previously unknown ransomware file extension infects your data.
In this scenario, which two NetApp technologies will provide a writable volume of the dataset before the ransomware attack? (Choose two.)
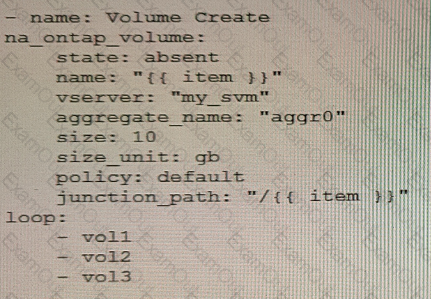
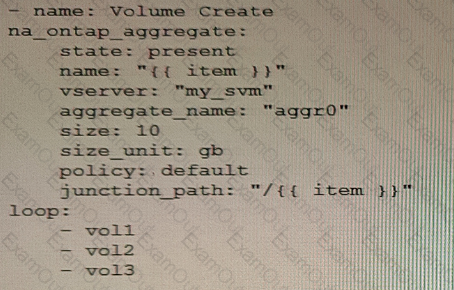
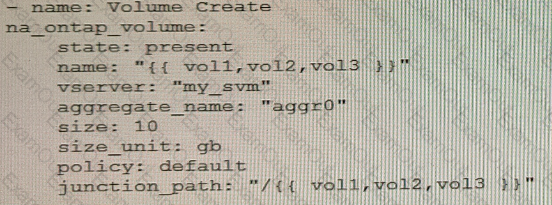
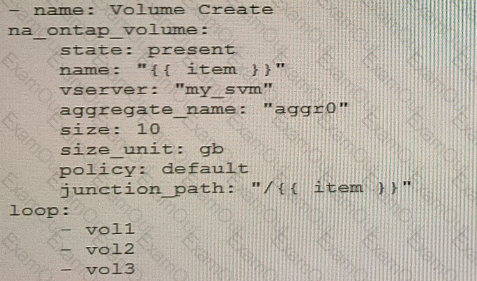
You are creating an Ansible playbook to deploy a NetApp ONTAP cluster. You want to take advantage of a loop to automate the creation of several volumes.
What would accomplish this task?
A)
B)
C)
D)
You deployed a NetApp Cloud Volumes ONTAP system in your AWS environment and you need to activate the WORM feature to secure them.
In this scenario, which two statements are correct? (Choose two.)
You are using Nvidia DeepOps to deploy Kubernetes clusters on top of NetApp ONTAP AI systems. In this scenario, which automation engine is required?

