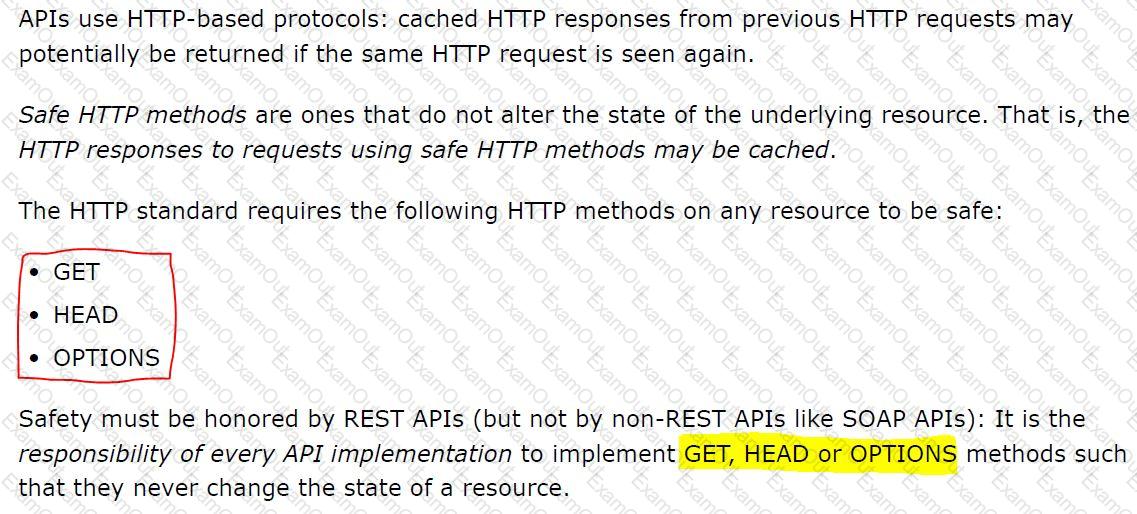
The responses to some HTTP requests can be cached depending on the HTTP verb used in the request. According to the HTTP specification, for what HTTP verbs is this safe to do?
What is typically NOT a function of the APIs created within the framework called API-led connectivity?
What is the main change to the IT operating model that MuleSoft recommends to organizations to improve innovation and clock speed?
What Mule application deployment scenario requires using Anypoint Platform Private Cloud Edition or Anypoint Platform for Pivotal Cloud Foundry?
Once an API Implementation is ready and the API is registered on API Manager, who should request the access to the API on Anypoint Exchange?
A system API is deployed to a primary environment as well as to a disaster recovery (DR) environment, with different DNS names in each environment. A process API is a client to the system API and is being rate limited by the system API, with different limits in each of the environments. The system API's DR environment provides only 20% of the rate limiting offered by the primary environment. What is the best API fault-tolerant invocation strategy to reduce overall errors in the process API, given these conditions and constraints?
What best describes the Fully Qualified Domain Names (FQDNs), also known as DNS entries, created when a Mule application is deployed to the CloudHub Shared Worker Cloud?
An API experiences a high rate of client requests (TPS) vwth small message paytoads. How can usage limits be imposed on the API based on the type of client application?
Which of the following best fits the definition of API-led connectivity?
True or False. We should always make sure that the APIs being designed and developed are self-servable even if it needs more man-day effort and resources.