When a client and server are exchanging messages during the mTLS handshake, what is being agreed on during the cipher suite exchange?
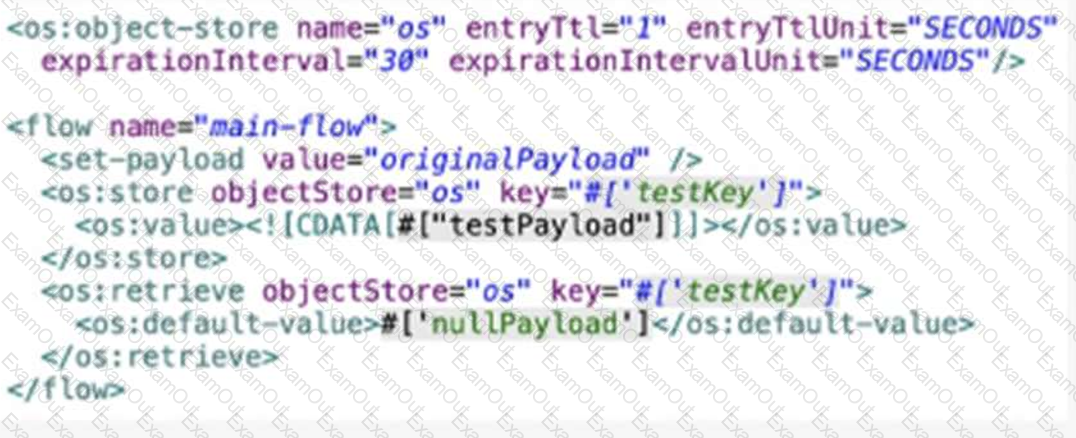
Refer to the exhibit.
A Mute Object Store is configured with an entry TTL of one second and an expiration interval of 30 seconds.
What is the result of the flow if processing between os’store and os:retrieve takes 10 seconds?
A scatter-gather router is configured with four routes:Route A, B, C and D.
Route C false.
A Mule application uses API autodiscovery to access and enforce policies for a RESTful implementation.
A Mule implementation uses a HTTP Request within an Unit Successful scope to connect to an API.
How should a permanent error response like HTTP:UNAUTHORIZED be handle inside Until Successful to reduce latency?
Mule application A is deployed to CloudHub and is using Object Store v2. Mute application B is also deployed to CloudHub.
Which approach can Mule application B use to remove values from Mule application A’S Object Store?
A heathcare customer wants to use hospital system data, which includes code that was developed using legacy tools and methods. The customer has created reusable Java libraries in order to read the data from the system.
What is the most effective way to develop an API retrieve the data from the hospital system?
A Mule application includes a subflow containing a Scatter.Gather scope. Within each log of the Scatter.Gatter. an HTTP connector calls a PUT endpoint to modify records in different upstream system. The subflow is called inside an Unit successful scope to retry if a transitory exception is raised.
A technical spike is being performed to increase reliability of the Mule application.
Which steps should be performed within the Mule flow above the ensure idempontent behavior?

