From the Security & Compliance admin center, you create a content export as shown in the exhibit. (Click the Exhibit tab.)
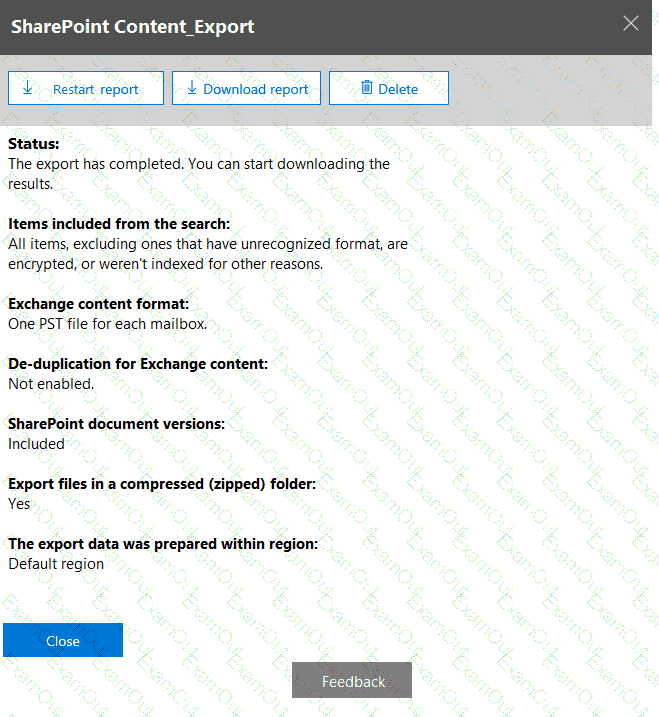
What will be excluded from the export?
HOTSPOT
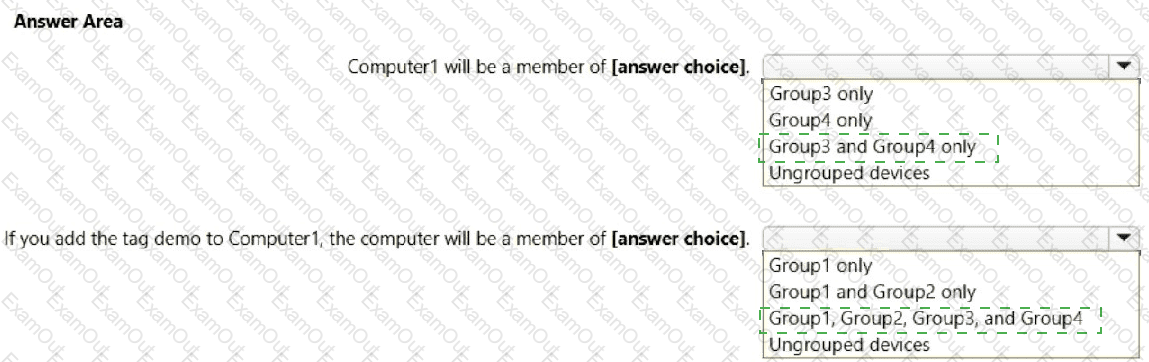
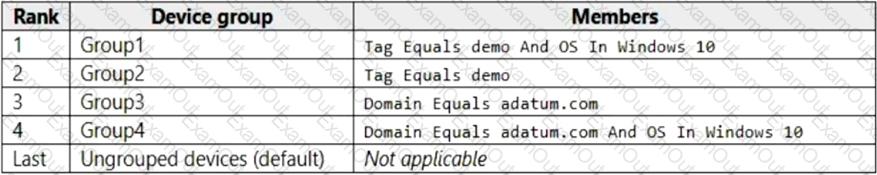
Your company uses Microsoft Defender for Endpoint. Microsoft Defender for Endpoint includes the device groups shown in the following table.
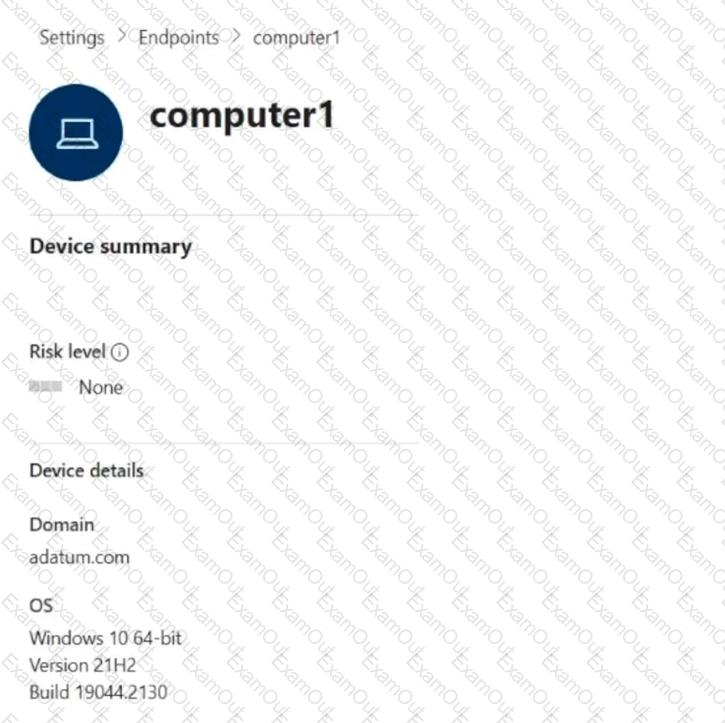
You onboard a computer named computer1 to Microsoft Defender for Endpoint as shown in the following exhibit.
Use the drop-down menus to select the answer choice that completes each statement.
NOTE: Each correct selection is worth one point.

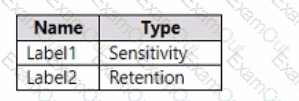
You have a Microsoft 365 E5 subscription that contains the labels shown in the following table.
You have the items shown in the following table.
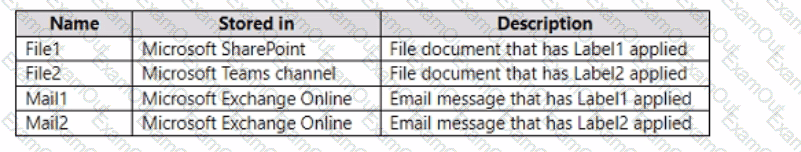
Which items can you view in Content explorer?
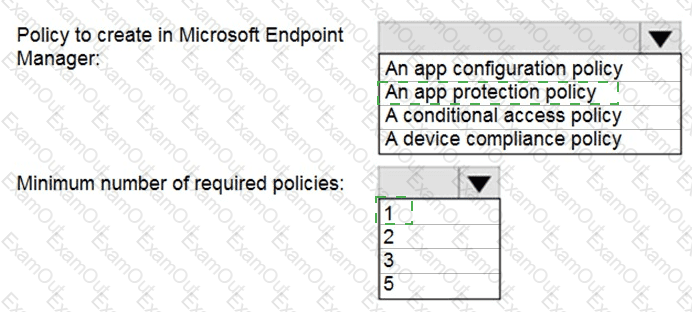
You have a Microsoft 365 E5 tenant that contains five devices enrolled in Microsoft Intune as shown in the following table.
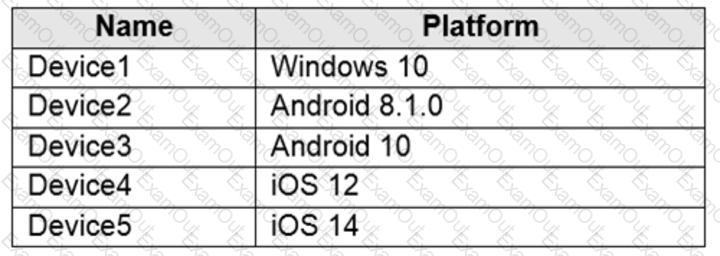
All the devices have an app named App1 installed.
You need to prevent users from copying data from App1 and pasting the data into other apps.
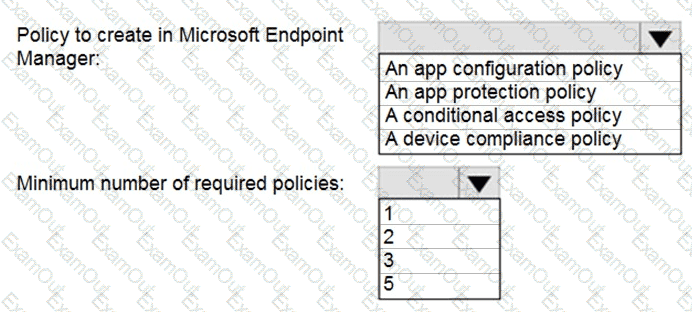
Which policy should you create in Microsoft Endpoint Manager, and what is the minimum number of required policies? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
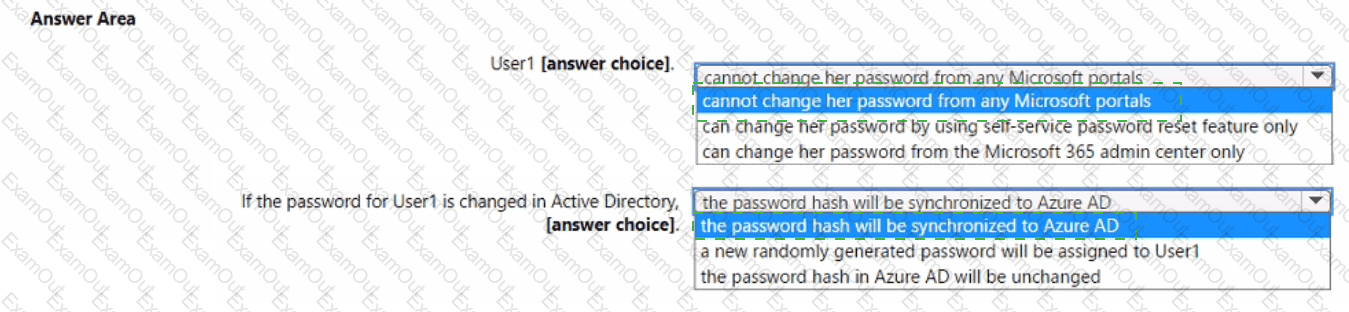
Your company has a hybrid deployment of Microsoft 365.
An on-premises user named User1 is synced to Azure AD.
Azure AD Connect is configured as shown in the following exhibit
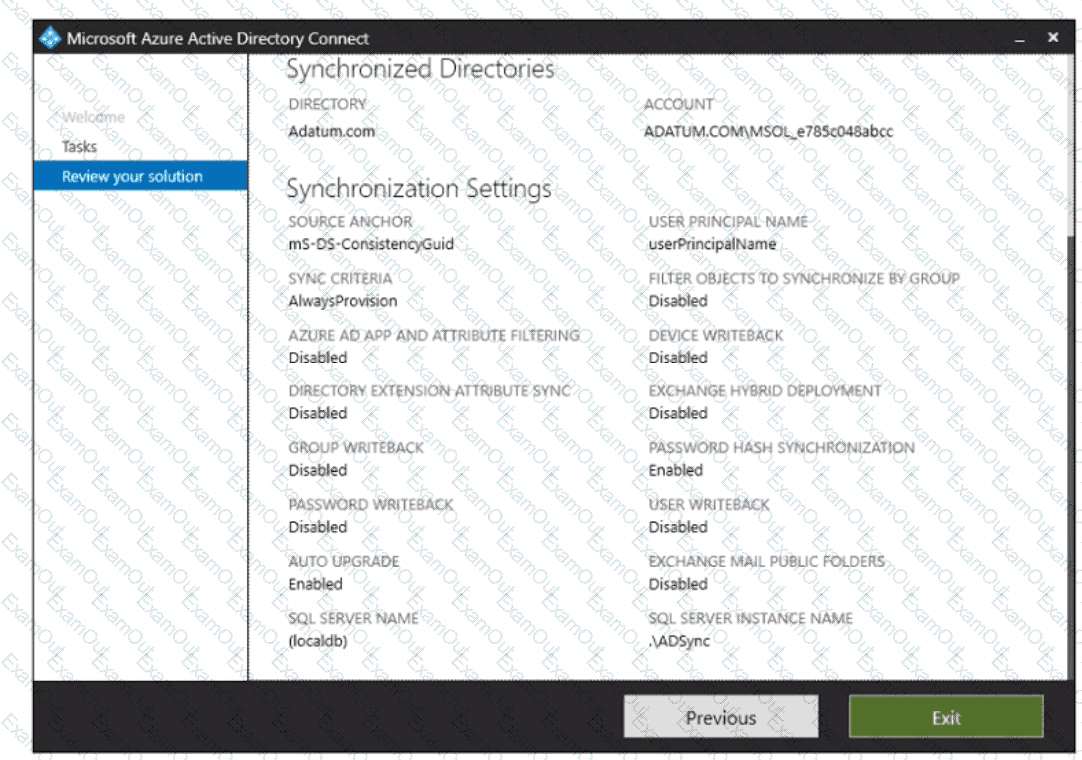
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
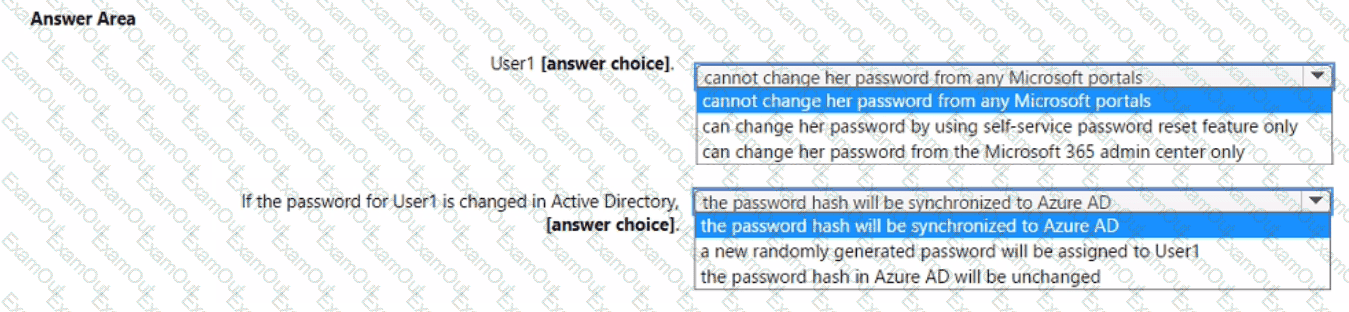
You have a Microsoft 365 tenant that has Enable Security defaults set to No in Azure Active Directory (Azure AD).
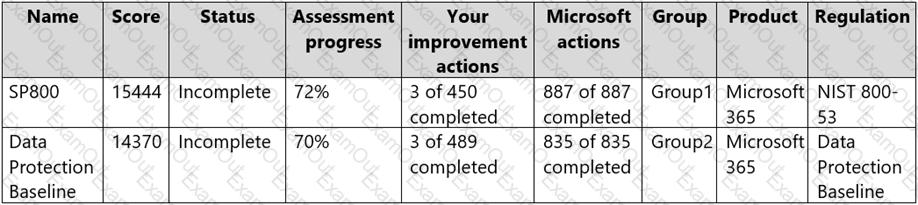
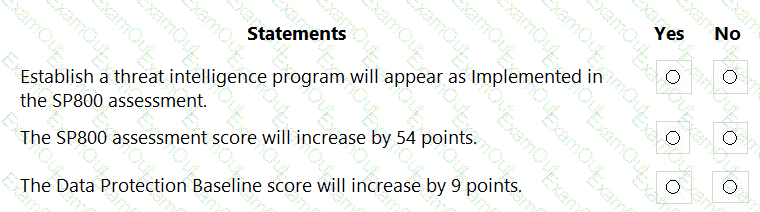
The tenant has two Compliance Manager assessments as shown in the following table.
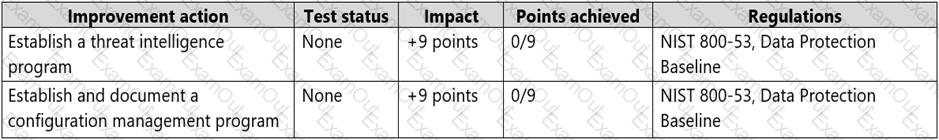
The SP800 assessment has the improvement actions shown in the following table.
You perform the following actions:
For the Data Protection Baseline assessment, change the Test status of Establish a threat intelligence program to Implemented.
Enable multi-factor authentication (MFA) for all users.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
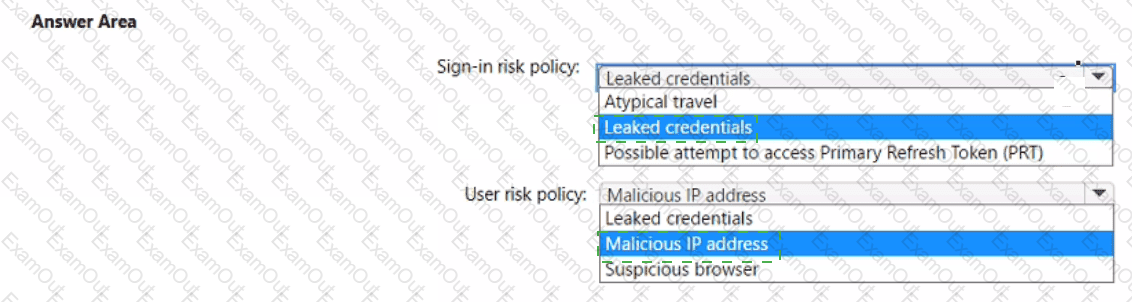
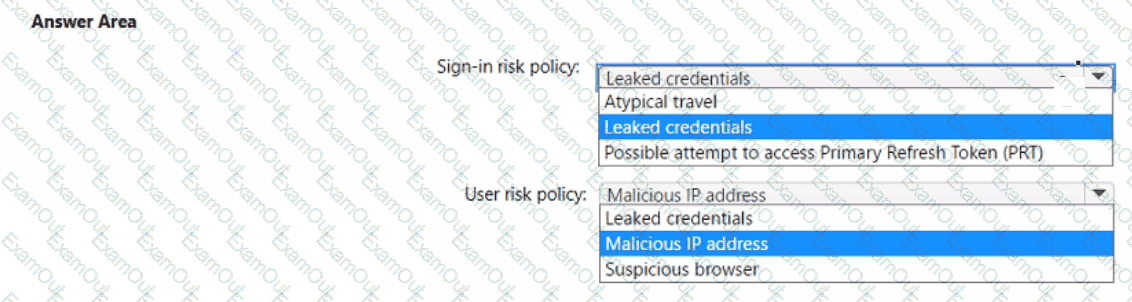
You have a Microsoft 365 E5 subscription.
You plan to implement identity protection by configuring a sign-in risk policy and a user risk policy. Which type of risk is detected by each policy? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint site named Sitel. Site! contains the files shown in the following table.

You have a data loss prevention (DLP) policy named DLP1 that has the advanced DLP rules shown in the following table.
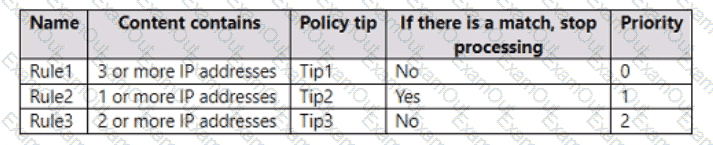
You apply DLP1 to Site1.
Which policy tip is displayed for each file? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

: 222 HOTSPOT
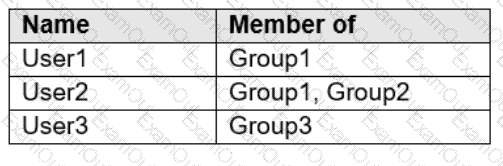
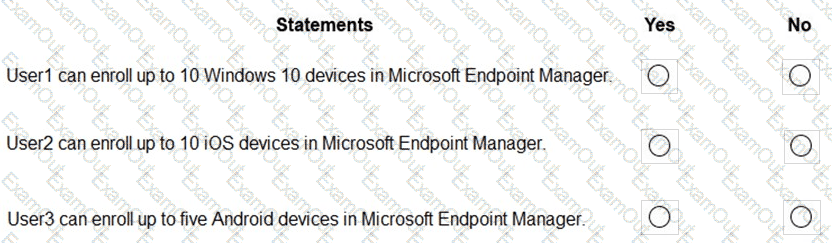
You have a Microsoft 365 subscription that contains the users in the following table.
In Microsoft Endpoint Manager, you create two device type restrictions that have the settings shown in the following table.
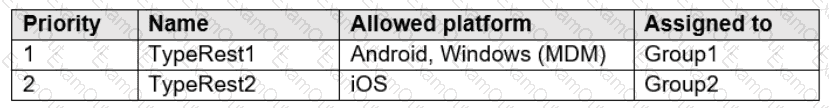
In Microsoft Endpoint Manager, you create three device limit restrictions that have the settings shown in the following table.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint and Microsoft Intune.
All devices run Windows 11 and are Microsoft Entra joined.
You are alerted to a zero-day attack.
You need to identify which devices were affected by the attack and send a request to Intune administrators to update the affected devices.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.