You need to meet the technical requirements for the IT department.
What should you do first?
You use a Microsoft Intune subscription to manage iOS devices.
You configure a device compliance policy that blocks jailbroken iOS devices.
You need to enable Enhanced jailbreak detection.
What should you configure?
You have computer that run Windows 10 and connect to an Azure Log Analytics workspace. The workspace is configured to collect all available events from Windows event logs.
The computers have the logged events shown in the following table.
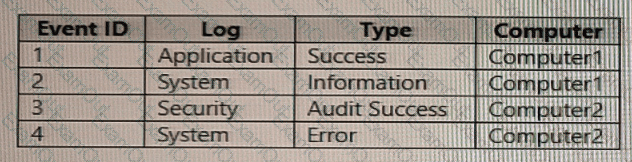
Which events are collected in the Log Analytics workspace?
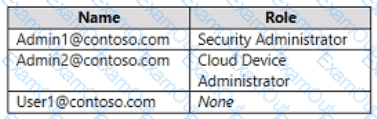
You have an Azure AD tenant named contoso.com that contains the users shown in the following table.
You have a computer named Computer1 that runs Windows 10. Computer1 is in a workgroup and has the local users shown in the following table.
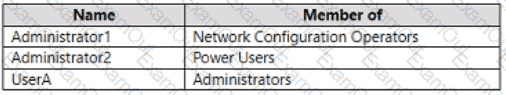
UserA joins Computer1 to Azure AD by using user1@contoso.com.
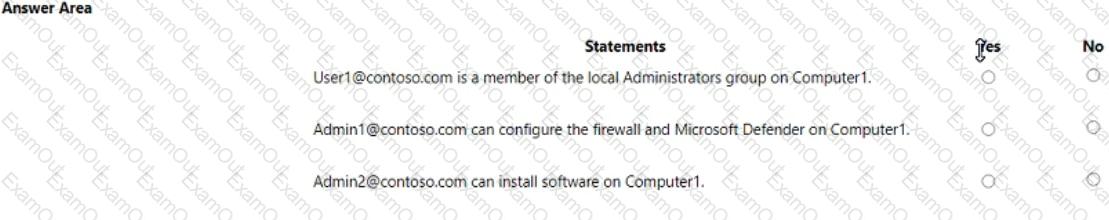
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
You have the on-premises servers shown in the following table.
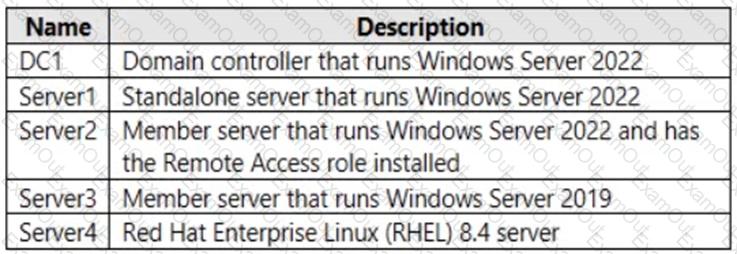
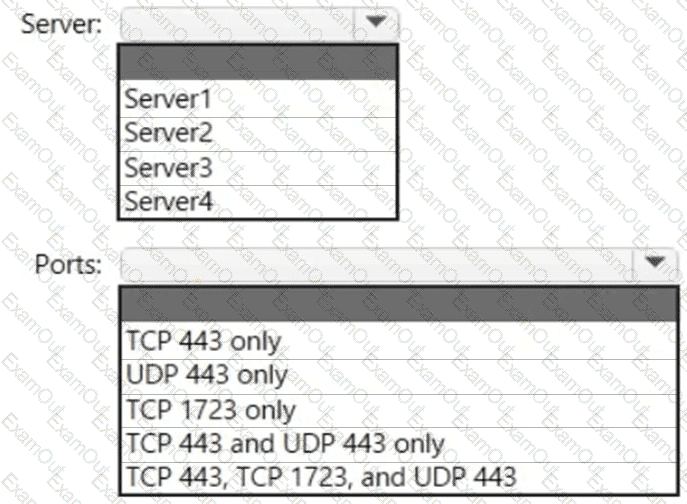
You have a Microsoft 365 E5 subscription that contains Android and iOS devices. All the devices are managed by using Microsoft Intune.
You need to implement Microsoft Tunnel for Intune. The solution must minimize the number of open firewall ports.
To which server can you deploy a Tunnel Gateway server, and which inbound ports should be allowed on the server to support Microsoft Tunnel connections? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains 100 Windows 10 devices enrolled in Microsoft Intune.
You plan to use Endpoint analytics.
You need to create baseline metrics.
What should you do first?
You have a Microsoft 365 E5 subscription that contains the devices shown in the following table.
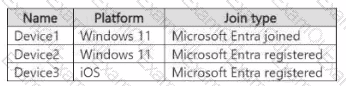
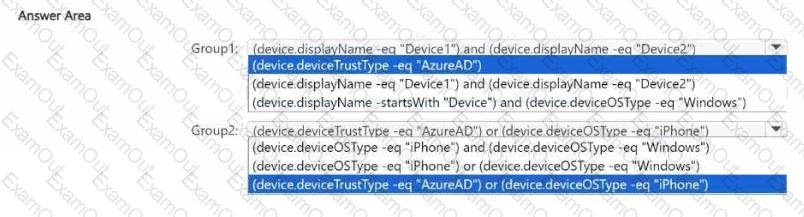
You need to create two dynamic device groups named Group1 and Group2. The solution must meet the following requirements:
• Group1 must contain Device1 and Device2 only.
• Group2 must contain Device1 and Device3 only.
Which device membership rule should you configure for each group? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure subscription.
You have an on-premises Windows 11 device named Device 1.
You plan to monitor Device1 by using Azure Monitor.
You create a data collection rule (DCR) named DCR1 in the subscription.
To what should you associate DCR1 ?
What should you configure to meet the technical requirements for the Azure AD-joined computers?
What should you use to meet the technical requirements for Azure DevOps?




