An ePO administrator decides to define a trusted network in the firewall policy. This will result in:
Which of the following describes the difference in functionality between Real Protect cloud-based and Real Protect client-based?
An ePO administrator needs to add exclusions for a folder. The folder has been created in several locations, including C:\Program Files\Custom\Acme or C:\Program Files\Acme, but the folder could be located in other subfolders in the Program Files folder. Which of the following is the correct way to write an exclusion for the Acme folder?
Exploit prevention content is released
When creating an exploit prevention process exclusion, at least one identifier must be specified. Which of the following is an identifier?
An engineer needs to allow a specific application to run. The engineer just finished creating an Exploit Prevention process exclusion. After applying the exclusion, the engineer notices the application is not being run. The following information is provided to the engineer:
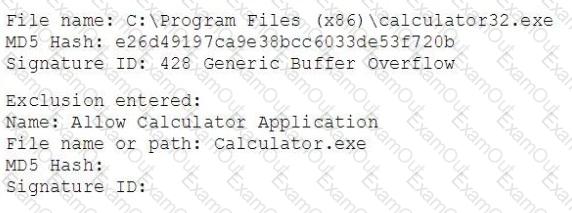
Which of the following is the error with the engineer's exclusion?
Which of the following components can the Endpoint Migration Assistant tool migrate?
A user navigates to a website and notices a small blue square around an "M" in the upper-right corner of the Chrome browser. Which of the following does the blue color indicate within the toolbar?
An ePO administrator is experiencing issues installing an ENS module on a client machine and decides to investigate by analyzing the install log. In which of the following locations will the administrator find the install log, assuming it is in its default location on the endpoint?
An administrator wants to prevent incoming packets until the system reboots fully. Which of the following features should be configured to allow this?

