An attacker has sent malicious macro-enabled Office files. Which of the following regular expressions will return a list of macro-enabled files?
An incident responder suspects that a host behind a firewall is infected with malware. Which of the following should the responder use to find the IP address of the infected machine?
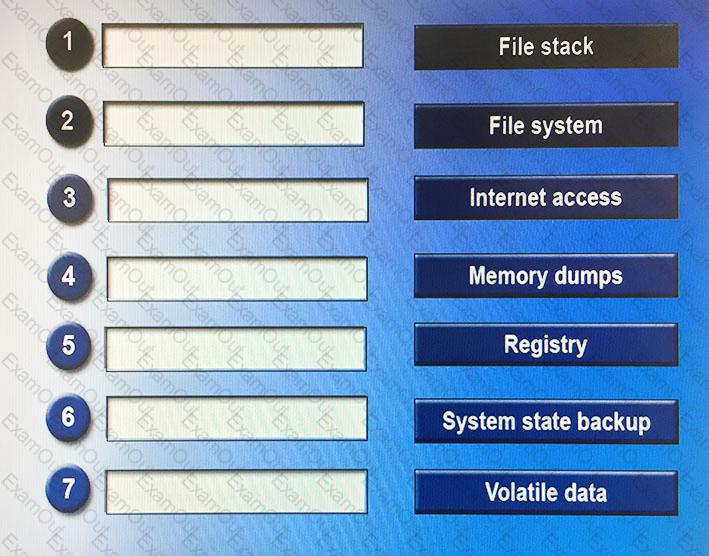
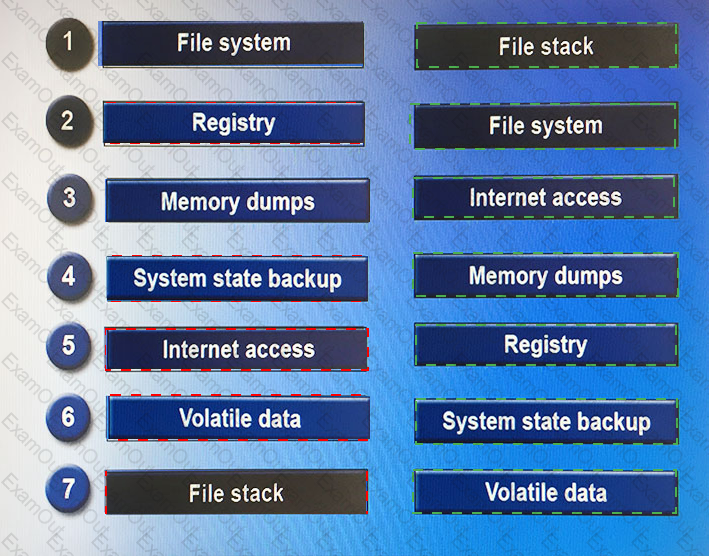
Drag and drop the following steps in the correct order from first (1) to last (7) that a forensic expert would follow based on data analysis in a Windows system.
Which of the following could an attacker use to perpetrate a social engineering attack? (Choose two.)
A security analyst for a financial services firm is monitoring blogs and reads about a zero-day vulnerability being exploited by a little-known group of hackers. The analyst wishes to independently validate and corroborate the blog’s posting. Whichof the following sources of information will provide the MOST credible supporting threat intelligence in this situation?
Why is it important to update system clocks from a single time source?
An attacker performs reconnaissance on a Chief Executive Officer (CEO) using publicity available resources to gain access to the CEO’s office. The attacker was in the CEO’s office for less than five minutes, and the attack left no traces in any logs, nor was there any readily identifiable cause for the exploit. The attacker in then able to use numerous credentials belonging to the CEO to conduct a variety of further attacks. Which of the following types of exploit is described?
While reviewing some audit logs, an analyst has identified consistent modification of the sshd_config file for an organization’s server. The analyst would like to investigate and compare contents of the current file with archived versions of files that are saved weekly. Which of the following tools will be MOST effective during the investigation?
To redact or obfuscate sensitive data, a company requires its name be changed throughout a port-incident report. Using a Linux sed command, which of the following will replace the company’s name with “Acme”?
Which of the following enables security personnel to have the BEST security incident recovery practices?