An alert on user account activity outside of normal business hours returns Windows even IDs 540 and 4624. In which of the following locations will these events be found?
A zero-day vulnerability is discovered on a company’s network. The security analyst conducts a log review, schedules an immediate vulnerability scan, and quarantines the infected system, but cannot determine the root cause of the vulnerability. Which of the following is a source of information that can be used to identify the cause of the vulnerability?
A security professional has been tasked with the protection of a specific set of information essential to a corporation’s livelihood, the exposure of which could cost the company billions of dollars in long-term revenue. The professional is interested in obtaining advice for preventing the theft of this type of information. Which of the following is the BEST resource for finding this material?
Which of the following techniques allows probing firewall rule sets and finding entry points into a targeted system or network?
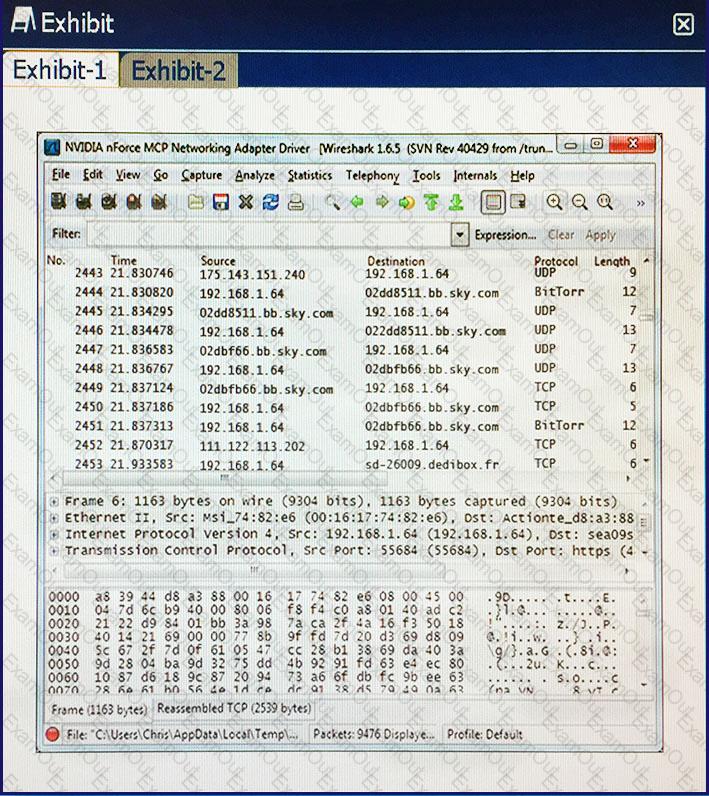
Click the exhibit button. After reviewing captured network traffic logs, a security auditor suspects a violation of the organization’s computer use policy. Which of the following is the likely indicator of the violation?
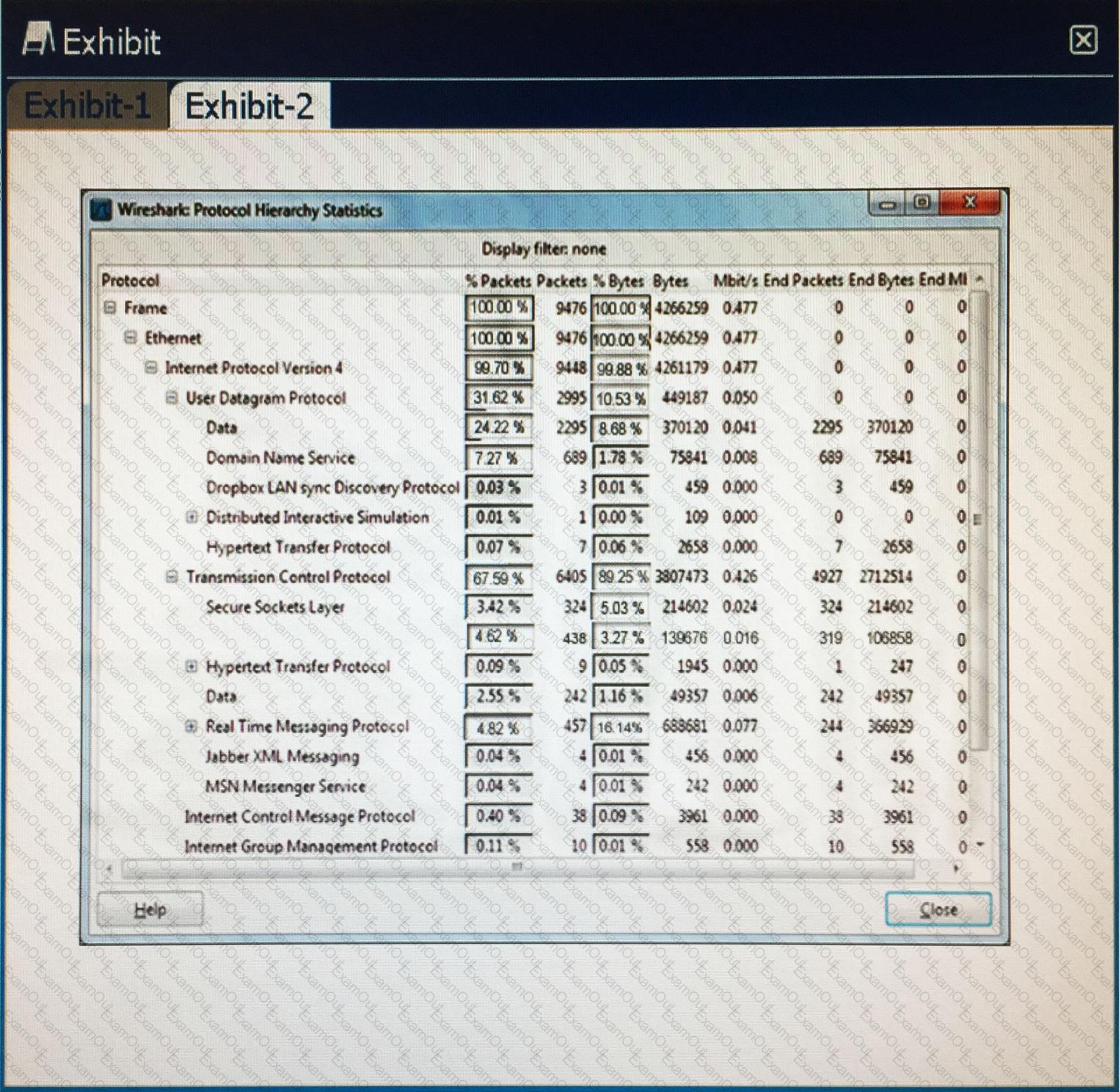
A SOC analyst reviews vendor security bulletins and security blog articles against the company’s deployed system and software base. Based on current attack patterns, three vulnerabilities, including a zero-day vulnerability, have been upgraded to high priority. Which of the following should the SOC analyst recommend? (Choose two.)
During a malware outbreak, a security analyst has been asked to capture network traffic in hourly increments for analysis by the incident response team. Which of the following tcpdump commands would generate hourly pcap files?
Which of the following tools can be used to identify open ports and services?
During an annual penetration test, several rootkit-enabled systems are found to be exfiltrating data. The penetration test team and the internal incident response team work to begin cleanup. The company’s operations team offers a new emails server to use for communications during the incident. As cleanup continues, the attackers seem to know exactly what the incident response plan is. Which of the following will prevent the attackers from compromising cleanup activities?
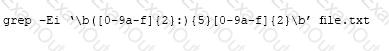
The above Linux command is used to search for:

