What are two prerequisites of capacity planning in a network design? (Choose two.)
Which two statements are correct about the Juniper Connected Security strategy? (Choose two.)
Which two switches should you recommend as leaf nodes for a small data center where cost is a factor? (Choose two.)
Which two statements about network management are correct? (Choose two.)
Click the Exhibit button.
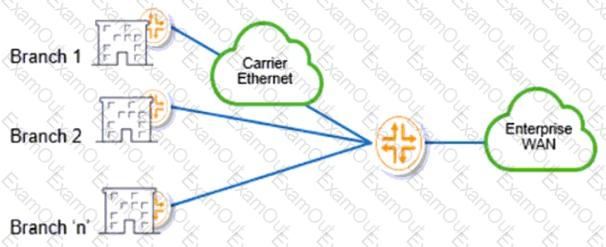
Which two WAN functions are shown in the exhibit? (Choose two.)
Where are path selections made for an SD-WAN router?
Which two technologies would be used to encapsulate frames to provide Layer 2 reachability across an IP fabric data center? (Choose two.)
You are asked to design a backup schedule using existing tools and incurring no additional expense.
Which two protocols would you consider to accomplish this task? (Choose two.)
You are considering changing an IBGP-based IP fabric design to one that is EBGP-based.
In this scenario, which two statements are correct about an EBGP-based design? (Choose two.)
SD-WAN routes security-sensitive data across MPLS, VPNs, and _______________.

