Security Levels (SLs) are broken down into which three types?
Which NIST Special Publication focuses specifically on securing Industrial Control Systems (ICS)?
An industrial facility wants to ensure that only authorized systems reach its PLCs while minimizing disruption to time-sensitive control processes. Which type of firewall would BEST suit this need?
What does IACS stand for?
Which standard is applied during the Assess phase for risk assessment?
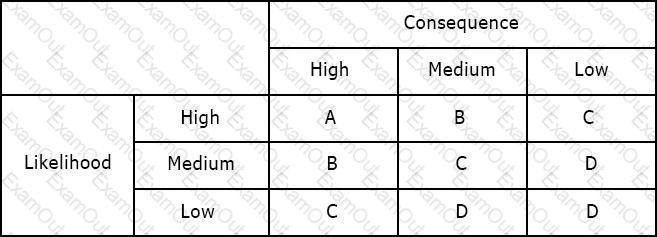
Using the risk matrix below, what is the risk of a medium likelihood event with high consequence?
Which part of the standard provides a list of possible Foundational Requirements to address assessed risks?
What is TRUE regarding safety systems?
What is the primary goal of the Assess phase in the IACS Cybersecurity Lifecycle?
Which type of cryptographic algorithms requires more than one key?
Available Choices (select all choices that are correct)

