An internal auditor found the following information while reviewing the monthly financial siatements for a wholesaler of safety
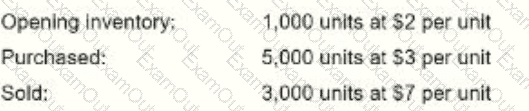
The cost of goods sold was reported at $8,500. Which of the following inventory methods was used to derive this value?
Which of the following is on example of a smart device security control intended to prevent unauthorized users from gaining access to a device's data or applications?
An organization uses the management-by-objectives method whereby employee performance is based on defined goals. Which of the following statements is true regarding this approach?
Which of the following network types should an organization choose if it wants to allow access only to its own personnel?
Management is designing its disaster recovery plan. In the event that there is significant damage to the organization's IT systems this plan should enable the organization to resume operations at a recovery site after some configuration and data restoration. Which of the following is the ideal solution for management in this scenario?
An Internal auditor is using data analytics to focus on high-risk areas during an engagement. The auditor has obtained data and is working to eliminate redundancies in the data. Which of the following statements is true regarding this scenario?
Which of the following statements is true regarding data backup?
According to IIA guidance, which of the following links computers and enables them to -communicate with each other?
Which of the following responsibilities would ordinary fall under the help desk function of an organization?
Which of the following purchasing scenarios would gain the greatest benefit from implementing electronic data interchange (EDI)?
Which of the following application controls is the most dependent on the password owner?
While auditing an organization's customer call center, an internal auditor notices that Key performance indicators show a positive trend, despite the fact that there have been increasing customer complaints over the same period. Which of the following audit recommendations would most likely correct the cause of this inconsistency?
How do data analysis technologies affect internal audit testing?
During which phase of the contracting process are contracts drafted for a proposed business activity?
According to Herzberg’s Two-Factor Theory of Motivation, which of the following factors are mentioned most often by satisfied employees?

