In the CloudFabric solution, which of the following does iMaster NCE-Fabric collect device log information?
When packet loss occurs in a CloudFabric data center network, which of the following operations does the network administrator need to do first?
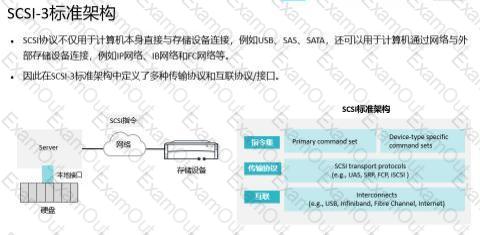
Which of the following interface standards uses SCSI instructions?
Which of the following monitoring log levels does iMaster NCE-FabricInsight support?
Of the basic concepts of computing virtualization technology, which of the following is the operating system running within a VM?
In the Huawei CloudFabric solution, the network controller uses the NETCONF device to deliver configurations. Which of the following encodings does NETCONF information use?
Which of the following features can be used in the Cloudfabric centralized storage NoF+ solution to manage the connected hosts and storage nodes?
Which of the following Linux namespaces implements process IDs that can be duplicated but do not affect each other?
After installing a CloudFabric data center network based on iMasterNCEFabric, the connectivity test is performed in iMasterNCEFabric, and the result is displayed as "FailedWhich of the following features is recommended for further detection?
Which of the following components in Huawei's intelligent lossless network solution architecture for multi-computing scenarios offloads the RDMA input layer and the following protocol stacks to the NIC hardware, so that peripherals can directly access the memory of the remote host?