Which of the following is not a process for remote users to access intranet resources through SSL VPN?
When Eth-Trunk is deployed for the heartbeat links between firewalls, the Eth-Trunk interface can be configured as a Layer 2 interface as long as the total bandwidth of active links on the Eth-Trunk is greater than 30% of the bandwidth required by service traffic.
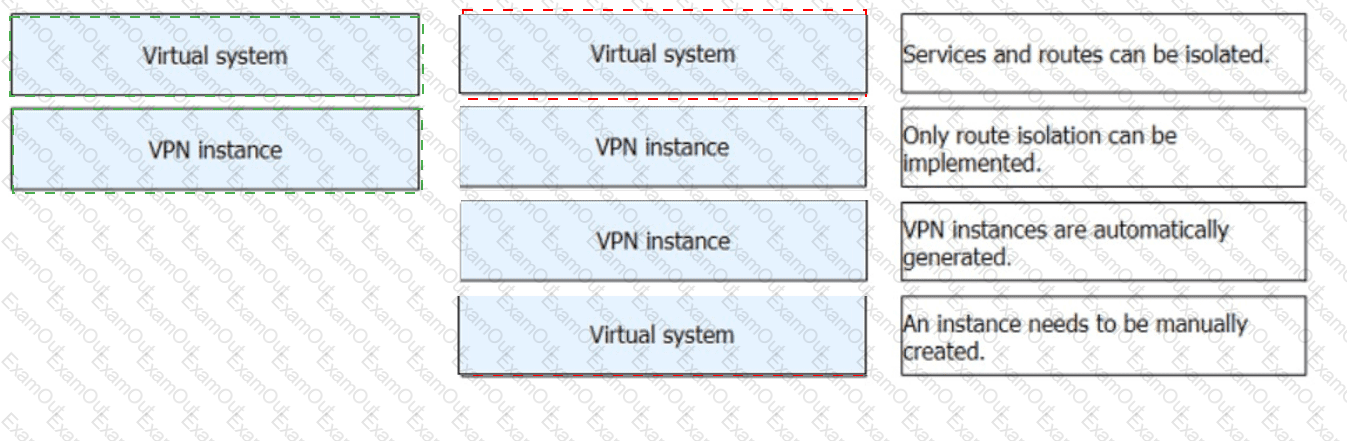
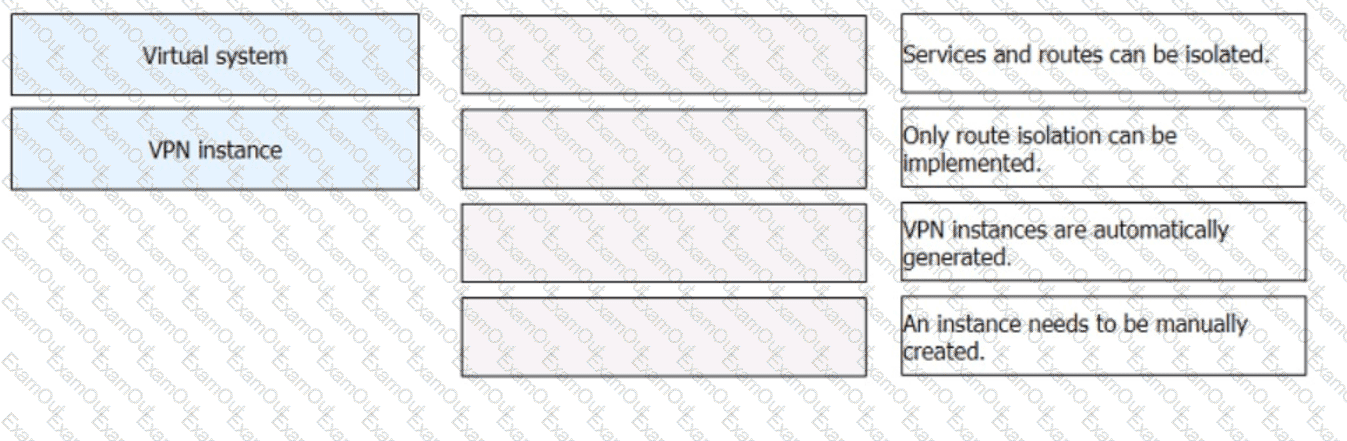
: 51 DRAG DROP
Match the description about virtual systems and VPN instances.
The difference between DoS attacks and DDoS attacks is that DoS attacks are usually directly initiated by attackers, whereas DDoS attacks are usually initiated by attackers controlling multiple zombies.
Which of the following are components of Huawei's anti-DDoS solution?(Select All that Apply)
Which of the following statements is false about the restrictions on configuring bandwidth profiles in parent and child policies on a firewall?
Which of the following statements are true about SYN scanning attacks?(Select All that Apply)
Which of the following statements is false about HTTP behavior?