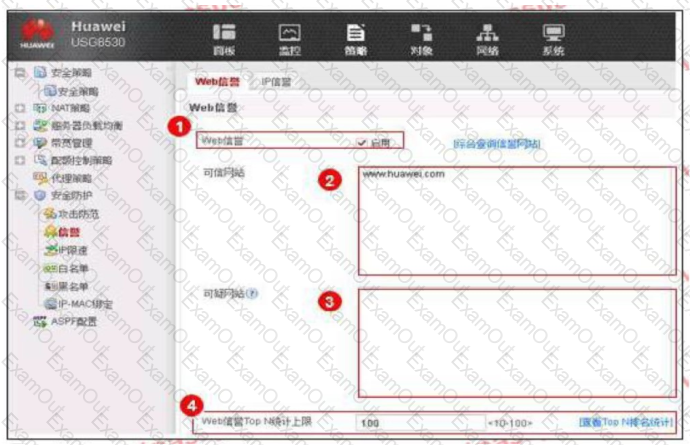
An enterprise administrator configures the Web reputation system as shown in the figure. Regarding the configuration, which of the following statements is correct?
In the Agile Controller-Campus admission control technology framework, regarding the description of RADIUS, which of the following options is correct?
Which of the following options is about SACG The description of the online process is wrong?
Regarding the mail content filtering configuration of Huawei USG6000 products, which of the following statements is wrong?.
File filtering technology can filter files based on the application of the file, the file transfer direction, the file type and the file extension.
The security management system is only optional, and anti-virus software or anti-hacking technology can be a good defense against network threats.
Regarding the statement of the mail protocol, which of the following is correct? (multiple choice)
For special message attacks, which of the following option descriptions is correct?
A Special control packet attack is a potential attack and does not have direct destructive behavior
B. The attacker probes the network structure by sending special control messages to launch a real attack.
C. Special control message attacks do not have the ability to detect the network structure. Only scanning attacks can detect the network.
D. Special control message items can only use ICMP to construct attack messages.
Terminal fault diagnosis tool can diagnose fault, also can collect terminal information.
Which of the following technology, administrators can according to business requirements, to scale to achieve load sharing of business flow?

