Which of the following statements about VXLAN is false?
Which of the following may be the reason why no data Is displayed on the telemetry management page of IMaster NCE-CampusInsight? (Select All that Apply)
After the HTTP domain name is entered in a browser, the user Is not redirected to the Portal URL. Which of the followings is the possible cause for this failure? (Select All that Apply)
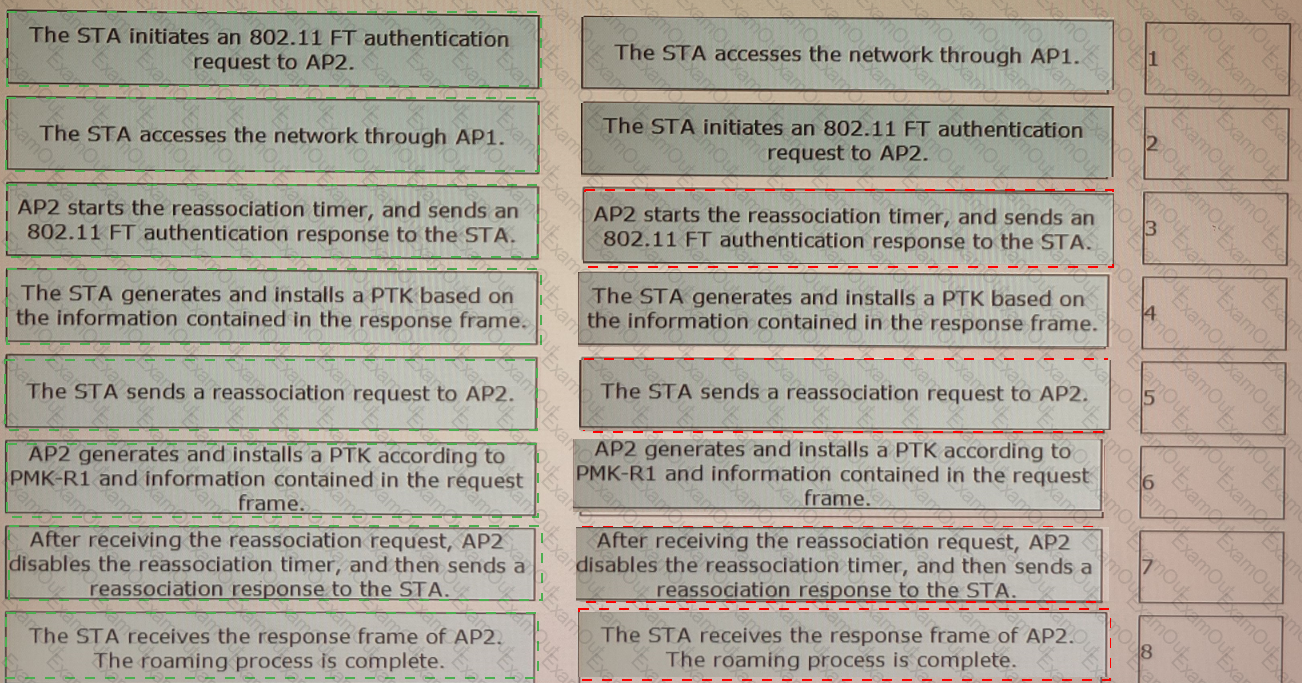
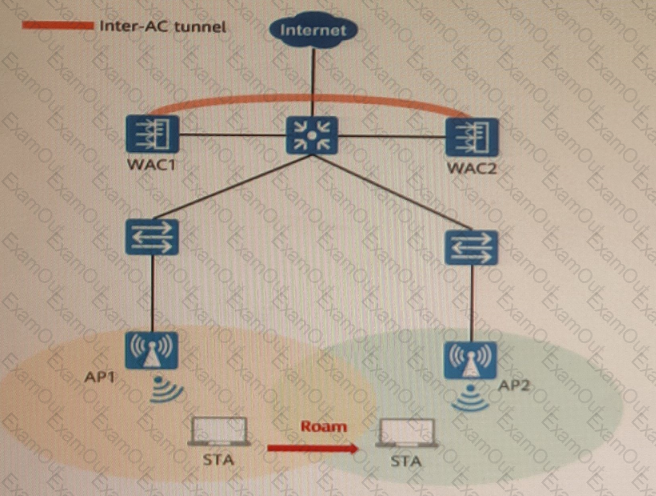
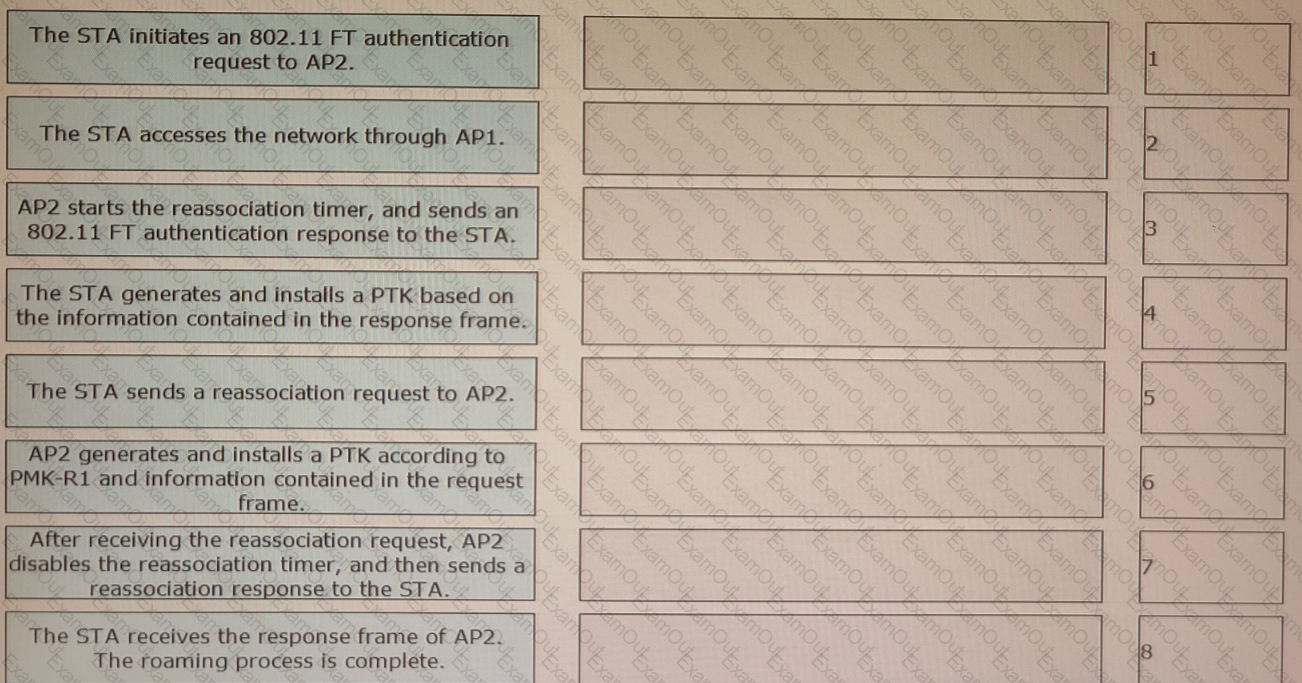
802. 11r fast roaming (over-the-air) is enabled on the WLAN shown in the figure. A STA roams from AP1 to AP2. Sort the steps in chronological order during the 802.11r fast roaming process between WACs.
Which of the following statements about attack defense is true?
Which of the following statements are true about data collection of IMaster NCE-Campuslnslght? (Select All that Apply)
Satellite positioning can achieve high positioning accuracy in both indoor and outdoor scenarios.
Which of the fallowings is not an IPv6 address type?
An AP may preferentially use the BTM mode to steer some STAs. With which of the following protocols are such STAs compliant?
Which of the following key factors is used by the CloudCampus cloud management platform to determine the tenant to which a device belongs?