When unsealing Vault, each Shamir unseal key should be entered:
When using Integrated Storage, which of the following should you do to recover from possible data loss?
To give a role the ability to display or output all of the end points under the /secrets/apps/* end point it would need to have which capability set?
The key/value v2 secrets engine is enabled at secret/ See the following policy:
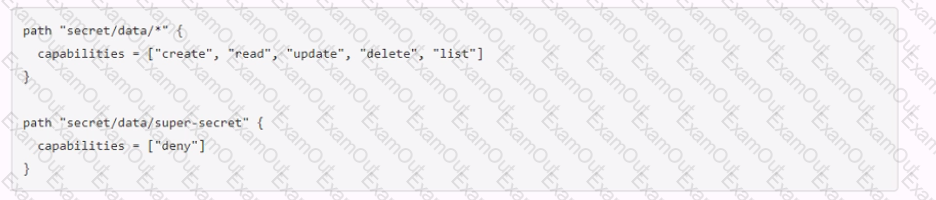
Which of the following operations are permitted by this policy? Choose two correct answers.
To make an authenticated request via the Vault HTTP API, which header would you use?
A web application uses Vault's transit secrets engine to encrypt data in-transit. If an attacker intercepts the data in transit which of the following statements are true? Choose two correct answers.
Your DevOps team would like to provision VMs in GCP via a CICD pipeline. They would like to integrate Vault to protect the credentials used by the tool. Which secrets engine would you recommend?
As a best practice, the root token should be stored in which of the following ways?
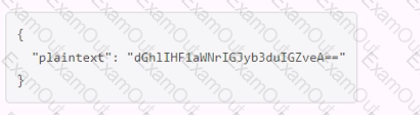
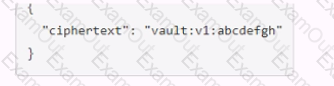
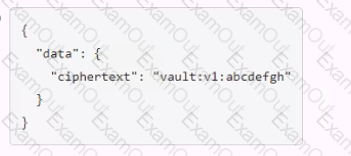
A user issues the following cURL command to encrypt data using the transit engine and the Vault AP:
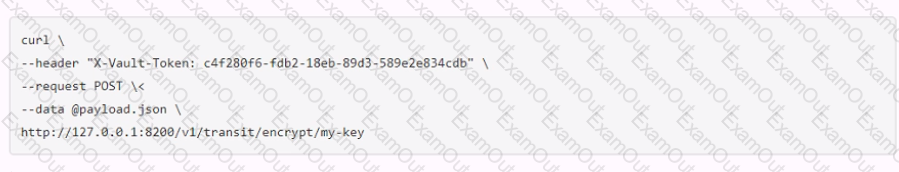
Which payload.json file has the correct contents?
Which of these are a benefit of using the Vault Agent?