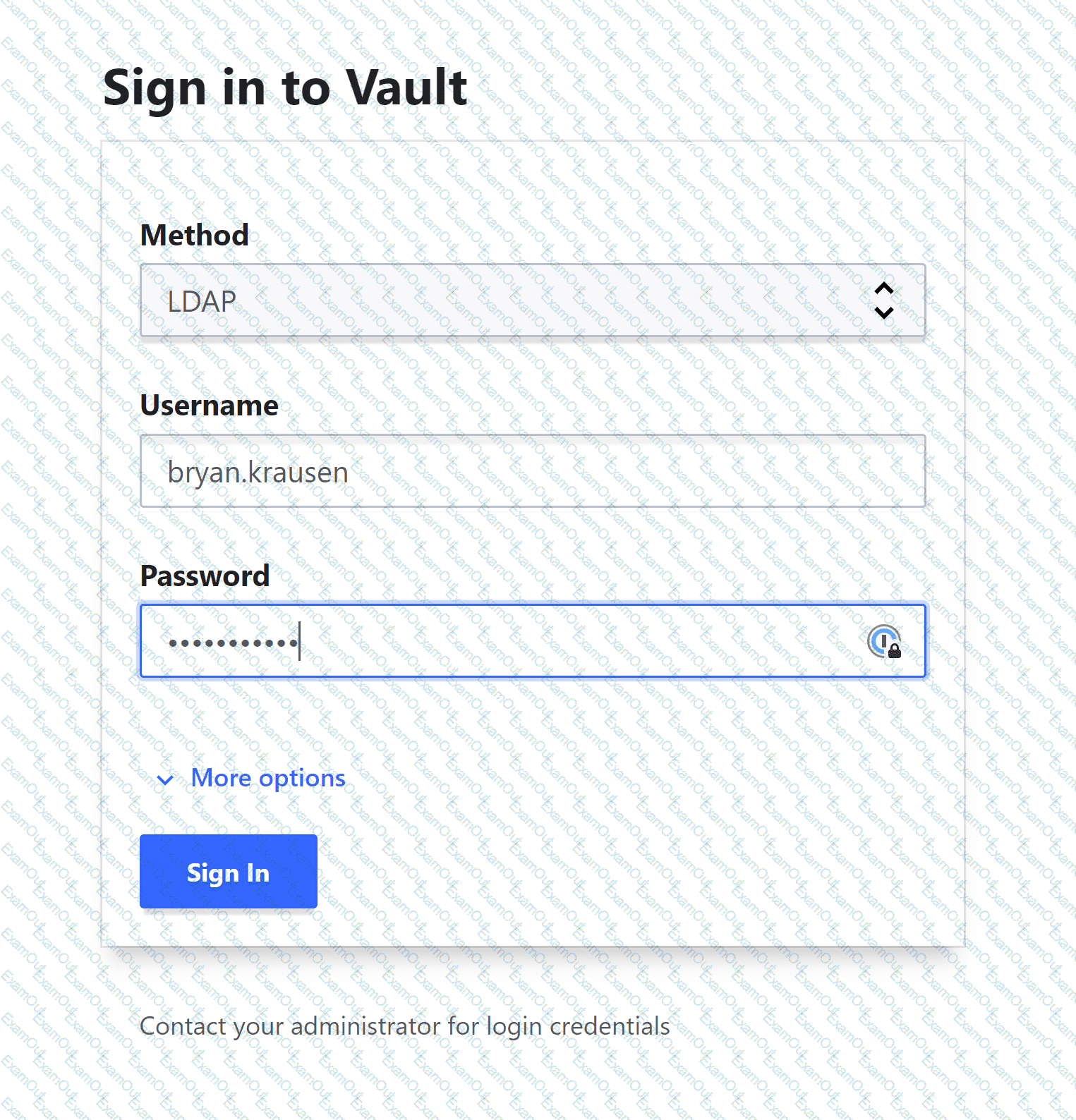
Your organization has enabled the LDAP auth method on the path of corp-auth/. When you access the Vault UI, you cannot log in despite providing the correct credentials. Based on the screenshot below, what action should you take to log in?
Your organization recently suffered a security breach on a specific application, and the security response team believes that MySQL database credentials were likely obtained during the event. The application generated the credentials using the database secrets engine in Vault mounted at the path database/. How can you quickly revoke all of the secrets generated by this secrets engine?
A developer team requests integration of their legacy application with Vault to encrypt and decrypt data for a backend database. They cannot modify the application for Vault authentication. What is the best way to achieve this integration?
Your supervisor has requested that you log into Vault and update a policy for one of the development teams. You successfully authenticated to Vault via OIDC but do not see a way to manage the Vault policies. Why are you unable to manage policies in the Vault UI?
All Vault instances, or clusters, include two built-in policies that are created automatically. Choose the two policies below and the correct information regarding each policy. (Select two)
Your organization runs workloads on both AWS and Azure for production applications. The security team has requested that a single Vault authentication mechanism be enabled to support applications on both public cloud platforms. Which of the following would be a valid auth method you can use?
Why are short-lived, dynamic secrets in Vault more secure than long-lived, static credentials?
You are configuring your application to retrieve a new PKI certificate upon provisioning. The Vault admins have given you an AppRole role-id and secret-id to inject into the CI/CD pipeline job that provisions your app. The application uses the credentials to successfully authenticate to Vault using the API. Which of the following is true about the step next required after authenticating to Vault?
What are orphan tokens?
Which of the following statements describe the CLI command below?
S vault login -method-1dap username-mitche11h

