True or False? Once you authenticate to Vault using the API, subsequent requests will automatically be permitted without further interaction.
A security architect is designing a solution to address the "Secret Zero" problem for a Kubernetes-based application that needs to authenticate to HashiCorp Vault. Which approach correctly leverages Vault features to solve this challenge?
Your organization is integrating its legacy application with Vault to improve its security. However, you have discovered that the application has issues when the token changes for authentication during testing. What type of token could be used to help alleviate this issue without compromising security?
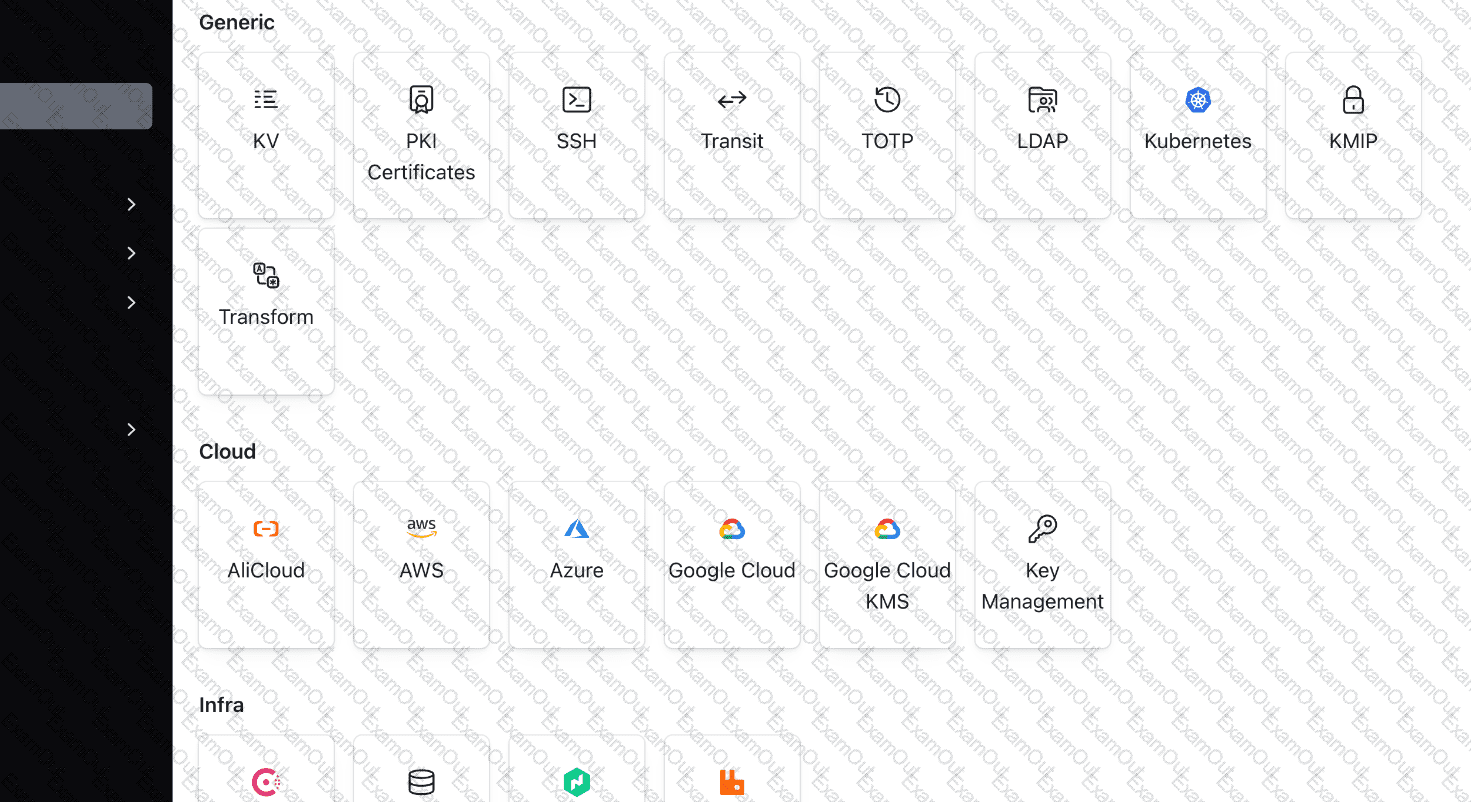
You have logged into the Vault UI and see this screen. What Vault component is being enabled in the screenshot below?
You need to write a new policy for Vault for a group of users on the automation team. The requirements stipulate that each user (and all future users) get access to their own private section of a KV secrets engine at the path kv/team/ and be able to manage their own secrets. Which policy below meets these requirements while minimizing the administrative effort and following the principle of least privilege?
Before data is written to the storage backend, the data is encrypted by which Vault feature?
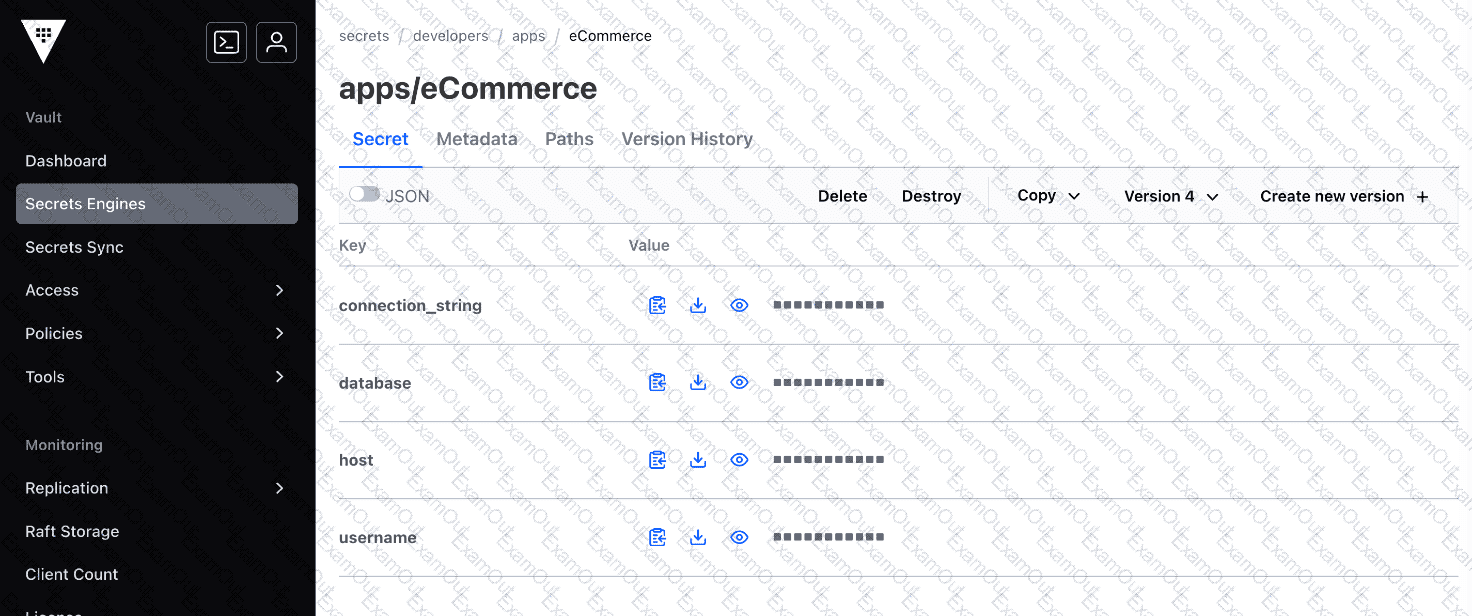
You are working on a new project and need to retrieve a secret from Vault. You log into the Vault UI and browse to the path where the secret is stored. Based on the screenshot below, what is true about the secrets stored in this path? (Select four)
You are planning the deployment of your first Vault cluster and have decided to use Integrated Storage as the storage backend. Where do you configure the storage backend to be used by Vault?
Your co-worker has asked you to perform certain operations in Vault and has provided you with a token accessor (not the token itself). What Vault operations would you be allowed to perform using only the provided accessor? (Select three)
How does the instance updates feature work when using the Vault Secrets Operator?

