HPE Aruba Networking Central displays an alert about an Infrastructure Attack that was detected. You go to the Security > RAPIDS events and see that the attack
was "Detect adhoc using Valid SSID."
What is one possible next step?
(Note that the HPE Aruba Networking Central interface shown here might look slightly different from what you see in your HPE Aruba Networking Central
interface as versions change; however, similar concepts continue to apply.)
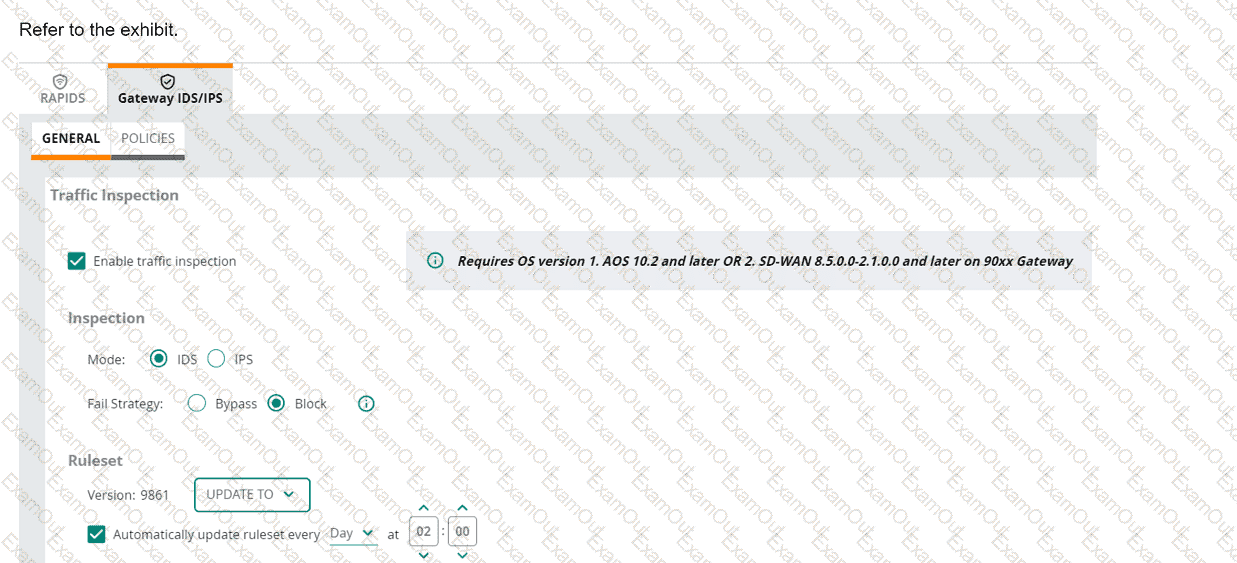
An HPE Aruba Networking 9x00 gateway is part of an HPE Aruba Networking Central group that has the settings shown in the exhibit. What would cause the
gateway to drop traffic as part of its IDPS settings?
A company issues user certificates to domain computers using its Windows CA and the default user certificate template. You have set up HPE Aruba Networking
ClearPass Policy Manager (CPPM) to authenticate 802.1X clients with those certificates. However, during tests, you receive an error that authorization has failed
because the usernames do not exist in the authentication source.
What is one way to fix this issue and enable clients to successfully authenticate with certificates?
Refer to Exhibit:
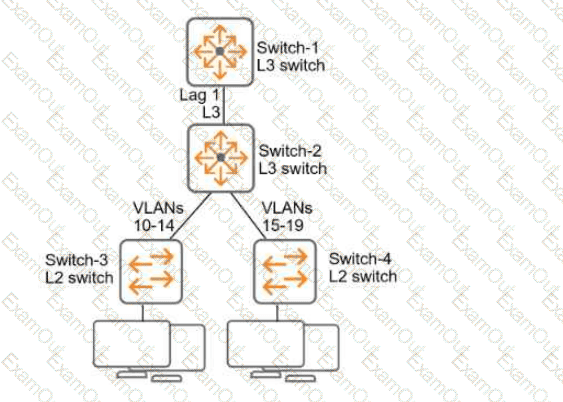
All of the switches in the exhibit are AOS-CX switches.
What is the preferred configuration on Switch-2 for preventing rogue OSPF routers in this network?
A company has Aruba APs that are controlled by Central and that implement WIDS. When you check WIDS events, you see a "detect valid SSID misuse" event. What can you interpret from this event, and what steps should you take?
A company has HPE Aruba Networking APs running AOS-10 that connect to AOS-CX switches. The APs will:
. Authenticate as 802.1X supplicants to HPE Aruba Networking ClearPass Policy Manager (CPPM)
. Be assigned to the "APs" role on the switches
. Have their traffic forwarded locally
What information do you need to help you determine the VLAN settings for the "APs" role?
A company has AOS-CX switches at the access layer, managed by HPE Aruba Networking Central. You have identified suspicious activity on a wired client. You want to analyze the client's traffic with Wireshark, which you have on your management station.
What should you do?
A company has HPE Aruba Networking APs and AOS-CX switches. The APs bridge wireless traffic. They receive DHCP IP addresses on VLAN 18. Wireless users are assigned to VLAN 12.
The company wants the APs to start using 802.1X authentication on their switch ports. You are configuring the port-access role to which the APs are assigned after authentication.
What is one recommended setting for that role?
A company wants to implement Virtual Network based Tunneling (VNBT) on a particular group of users and assign those users to an overlay network with VNI
3000.
Assume that an AOS-CX switch is already set up to:
. Implement 802.1X to HPE Aruba Networking ClearPass Policy Manager (CPPM)
. Participate in an EVPN VXLAN solution that includes VNI 3000
Which setting should you configure in the users' AOS-CX role to apply VNBT to them when they connect?
You are using Wireshark to view packets captured from HPE Aruba Networking infrastructure, but you are not sure that the packets are displaying correctly.
In which circumstance does it make sense to ensure that Wireshark has GRE enabled as one of its analyzed protocols?

