What is a guideline for managing local certificates on AOS-CX switches?
Understand that the switch must use the same certificate for all usages, such as its HTTPS server and RadSec client.
Create a self-signed certificate online on the switch because AOS-CX switches do not support CA-signed certificates.
Before installing the local certificate, create a trust anchor (TA) profile with the root CA certificate for the certificate that you will install.
Install an Online Certificate Status Protocol (OCSP) certificate to simplify the process of enrolling and re-enrolling for certificates.
The Answer Is:
CExplanation:
AOS-CX switches use certificates for various purposes, such as securing HTTPS access to the switch’s web interface, authenticating the switch as a RadSec client, or securing other communications. Managing local certificates on AOS-CX switches involves ensuring that the switch trusts the certificate authority (CA) that issued the certificate, which is critical for proper operation.
Option C, "Before installing the local certificate, create a trust anchor (TA) profile with the root CA certificate for the certificate that you will install," is correct. A trust anchor (TA) profile on AOS-CX switches contains the root CA certificate (or intermediate CA certificate) that issued the local certificate. This TA profile allows the switch to validate the certificate chain when the local certificate is installed. For example, if you install a CA-signed certificate for the HTTPS server, the switch needs the root CA certificate in a TA profile to trust the certificate. This is a standard guideline for certificate management on AOS-CX switches to ensure secure and proper operation.
Option A, "Understand that the switch must use the same certificate for all usages, such as its HTTPS server and RadSec client," is incorrect. AOS-CX switches support using different certificates for different purposes. For example, you can have one certificate for the HTTPS server and another for RadSec client authentication, as long as each certificate is associated with the appropriate service and trusted by the switch.
Option B, "Create a self-signed certificate online on the switch because AOS-CX switches do not support CA-signed certificates," is incorrect. AOS-CX switches fully support CA-signed certificates, and using CA-signed certificates is recommended for production environments to ensure trust and security. Self-signed certificates can be used for testing but are not a guideline for general certificate management.
Option D, "Install an Online Certificate Status Protocol (OCSP) certificate to simplify the process of enrolling and re-enrolling for certificates," is incorrect. OCSP is a protocol used to check the revocation status of certificates, not to simplify certificate enrollment. AOS-CX switches support OCSP for certificate validation, but installing an "OCSP certificate" is not a concept in certificate management, and it’s not a guideline for managing local certificates.
The HPE Aruba Networking AOS-CX 10.12 Security Guide states:
"Before installing a CA-signed local certificate on the switch, you must create a trust anchor (TA) profile that includes the root CA certificate (or intermediate CA certificate) that issued the local certificate. This ensures that the switch can validate the certificate chain. For example, to install a CA-signed certificate for the HTTPS server, use the command crypto pki ta-profile
Additionally, the guide notes:
"AOS-CX switches support both self-signed and CA-signed certificates. For production environments, it is recommended to use CA-signed certificates and ensure that the appropriate trust anchor profiles are configured to validate the certificate chain." (Page 202, Best Practices Section)
What is a use case for implementing RadSec instead of RADIUS?
A university wants to protect communications between the students' devices and the network access server.
A corporation wants to implement EAP-TLS to authenticate wireless users at their main office.
A school district wants to protect messages sent between RADIUS clients and servers over an untrusted network.
A organization wants to strengthen the encryption used to protect RADIUS communications without increasing complexity.
The Answer Is:
CExplanation:
RadSec (RADIUS over TLS) is a protocol for transporting RADIUS messages over TLS-encrypted TCP/IP networks. The primary use case for implementing RadSec instead of traditional RADIUS is to protect RADIUS communications, particularly when those messages must travel across an untrusted network, such as the internet. RadSec provides confidentiality, integrity, and authentication for RADIUS traffic between clients and servers which may not be within a single secure network. In the case of a school district that wants to ensure the security of messages sent between RADIUS clients and servers over potentially insecure networks, RadSec would be the appropriate choice.
You have a network with AOS-CX switches for which HPE Aruba Networking ClearPass Policy Manager (CPPM) acts as the TACACS+ server. When an admin authenticates, CPPM sends a response with:
Aruba-Priv-Admin-User = 1
TACACS+ privilege level = 15What happens to the user?
The user receives auditors access.
The user receives no access.
The user receives administrators access.
The user receives operators access.
The Answer Is:
CExplanation:
HPE Aruba Networking AOS-CX switches support TACACS+ for administrative authentication, where ClearPass Policy Manager (CPPM) can act as the TACACS+ server. When an admin authenticates, CPPM sends a TACACS+ response that includes attributes such as the TACACS+ privilege level and vendor-specific attributes (VSAs) like Aruba-Priv-Admin-User.
In this scenario, CPPM sends:
TACACS+ privilege level = 15: In TACACS+, privilege level 15 is the highest level and typically grants full administrative access (equivalent to a superuser or administrator role).
Aruba-Priv-Admin-User = 1: This Aruba-specific VSA indicates that the user should be granted the highest level of administrative access on the switch.
On AOS-CX switches, the privilege level 15 maps to the administrator role, which provides full read-write access to all switch functions. The Aruba-Priv-Admin-User = 1 attribute reinforces this by explicitly assigning the admin role, ensuring the user has unrestricted access.
Option A, "The user receives auditors access," is incorrect because auditors typically have read-only access, which corresponds to a lower privilege level (e.g., 1 or 3) on AOS-CX switches.
Option B, "The user receives no access," is incorrect because the authentication was successful, and CPPM sent a response granting access with privilege level 15.
Option D, "The user receives operators access," is incorrect because operators typically have a lower privilege level (e.g., 5 or 7), which provides limited access compared to an administrator.
The HPE Aruba Networking AOS-CX 10.12 Security Guide states:
"When using TACACS+ for administrative authentication, the switch interprets the privilege level returned by the TACACS+ server. A privilege level of 15 maps to the administrator role, granting full read-write access to all switch functions. The Aruba-Priv-Admin-User VSA, when set to 1, explicitly assigns the admin role, ensuring the user has unrestricted access." (Page 189, TACACS+ Authentication Section)
Additionally, the HPE Aruba Networking ClearPass Policy Manager 6.11 User Guide notes:
"ClearPass can send the Aruba-Priv-Admin-User VSA in a TACACS+ response to specify the administrative role on Aruba devices. A value of 1 indicates the admin role, which provides full administrative privileges." (Page 312, TACACS+ Enforcement Section)
Which is an accurate description of a type of malware?
Worms are usually delivered in spear-phishing attacks and require users to open and run a file.
Rootkits can help hackers gain elevated access to a system and often actively conceal themselves from detection.
A Trojan is any type of malware that replicates itself and spreads to other systems automatically.
Malvertising can only infect a system if the user encounters the malware on an untrustworthy site.
The Answer Is:
BExplanation:
Malware (malicious software) is a broad category of software designed to harm or exploit systems. HPE Aruba Networking documentation often discusses malware in the context of network security threats and mitigation strategies, such as those detected by the Wireless Intrusion Prevention (WIP) system.
Option A, "Worms are usually delivered in spear-phishing attacks and require users to open and run a file," is incorrect. Worms are a type of malware that replicate and spread automatically across networks without user interaction (e.g., by exploiting vulnerabilities). They are not typically delivered via spear-phishing, which is more associated with Trojans or ransomware. Worms do not require users to open and run a file; that behavior is characteristic of Trojans.
Option B, "Rootkits can help hackers gain elevated access to a system and often actively conceal themselves from detection," is correct. A rootkit is a type of malware that provides hackers with privileged (elevated) access to a system, often by modifying the operating system or kernel. Rootkits are designed to hide their presence (e.g., by concealing processes, files, or network connections) to evade detection by antivirus software or system administrators, making them a stealthy and dangerous type of malware.
Option C, "A Trojan is any type of malware that replicates itself and spreads to other systems automatically," is incorrect. A Trojan is a type of malware that disguises itself as legitimate software to trick users into installing it. Unlike worms, Trojans do not replicate or spread automatically; they require user interaction (e.g., downloading and running a file) to infect a system.
Option D, "Malvertising can only infect a system if the user encounters the malware on an untrustworthy site," is incorrect. Malvertising (malicious advertising) involves embedding malware in online ads, which can appear on both trustworthy and untrustworthy sites. For example, a legitimate website might unknowingly serve a malicious ad that exploits a browser vulnerability to infect the user’s system, even without the user clicking the ad.
The HPE Aruba Networking Security Guide states:
"Rootkits are a type of malware that can help hackers gain elevated access to a system by modifying the operating system or kernel. They often actively conceal themselves from detection by hiding processes, files, or network connections, making them difficult to detect and remove. Rootkits are commonly used to maintain persistent access to a compromised system." (Page 22, Malware Types Section)
Additionally, the HPE Aruba Networking AOS-8 8.11 User Guide notes:
"The Wireless Intrusion Prevention (WIP) system can detect various types of malware. Rootkits, for example, are designed to provide hackers with elevated access and often conceal themselves to evade detection, allowing the hacker to maintain control over the infected system for extended periods." (Page 421, Malware Threats Section)
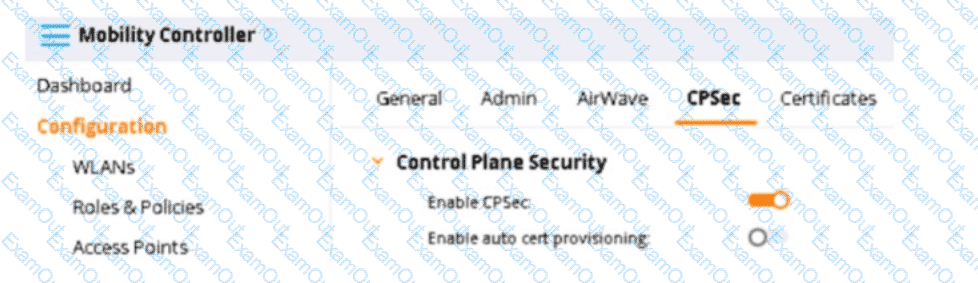
Refer to the exhibit, which shows the settings on the company's MCs.
You have deployed about 100 new HPE Aruba Networking 335 APs. What is required for the APs to become managed?
Installing CA-signed certificates on the APs
Approving the APs as authorized APs on the AP whitelist
Installing self-signed certificates on the APs
Configuring a PAPI key that matches on the APs and MCs
The Answer Is:
BExplanation:
The scenario involves an AOS-8 Mobility Controller (MC) with Control Plane Security (CPSec) enabled and auto certificate provisioning disabled. CPSec is a feature that secures the control plane communication between the MC and APs using certificates. When CPSec is enabled, APs must be authorized and trusted by the MC to become managed.
CPSec Enabled, Auto Cert Provisioning Disabled: When CPSec is enabled, APs must have a valid certificate to establish a secure control plane connection with the MC. If auto certificate provisioning is disabled (as shown in the exhibit), the MC does not automatically provision certificates to the APs. Instead, the APs must already have a factory-installed certificate (or a manually installed certificate), and the MC must trust the AP’s certificate by having the issuing CA in its trust list. Additionally, the AP must be on the MC’s AP whitelist to be authorized.
AP Whitelist: The AP whitelist is a list of authorized APs maintained on the MC (or Mobility Master, MM, if present). For an AP to become managed, its MAC address must be in the whitelist, especially when CPSec is enabled and auto provisioning is disabled. This ensures that only authorized APs can connect to the MC.
Option A, "Installing CA-signed certificates on the APs," is incorrect because HPE Aruba Networking APs, such as the 335 series, come with factory-installed certificates signed by Aruba’s CA. These certificates are sufficient for CPSec, provided the MC trusts the Aruba CA (which is typically preconfigured). Manually installing CA-signed certificates is not required unless the factory certificates are not used or trusted.
Option B, "Approving the APs as authorized APs on the AP whitelist," is correct. With CPSec enabled and auto cert provisioning disabled, the APs must be explicitly authorized by adding their MAC addresses to the AP whitelist on the MC. This step ensures that the MC accepts the AP’s certificate and allows it to become managed.
Option C, "Installing self-signed certificates on the APs," is incorrect because self-signed certificates are not typically used for CPSec. APs use factory-installed certificates, and the MC must trust the issuing CA. Self-signed certificates would require manual trust configuration on the MC, which is not a standard practice.
Option D, "Configuring a PAPI key that matches on the APs and MCs," is incorrect. PAPI (Protocol for AP Provisioning and Information) keys are used for securing communication between APs and the MC in non-CPSec environments or for specific configurations (e.g., when CPSec is disabled). When CPSec is enabled, certificate-based authentication replaces the need for a PAPI key.
The HPE Aruba Networking AOS-8 8.11 User Guide states:
"When Control Plane Security (CPSec) is enabled and auto certificate provisioning is disabled, APs must be authorized by adding their MAC addresses to the AP whitelist on the Mobility Controller (or Mobility Master). The AP uses its factory-installed certificate to establish a secure control plane connection with the MC. The MC must trust the CA that issued the AP’s certificate (e.g., Aruba’s CA), and the AP must be in the whitelist to become managed. To add an AP to the whitelist, navigate to Configuration > Access Points > AP Whitelist in the MC UI and add the AP’s MAC address." (Page 395, CPSec Configuration Section)
Additionally, the HPE Aruba Networking CPSec Deployment Guide notes:
"If auto cert provisioning is disabled, the AP whitelist becomes mandatory for CPSec. Each AP must be explicitly approved by adding its MAC address to the whitelist, ensuring that only authorized APs can connect to the MC. The AP’s factory certificate is used for authentication, and no manual certificate installation is required on the AP." (Page 12, CPSec with Manual Provisioning Section)
Refer to the exhibit.
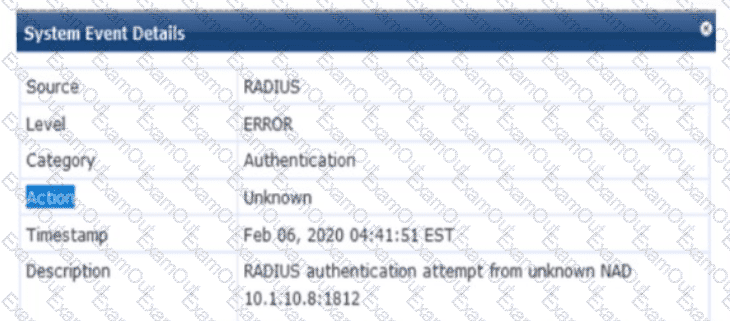
You are deploying a new HPE Aruba Networking Mobility Controller (MC), which is enforcing authentication to HPE Aruba Networking ClearPass Policy Manager (CPPM). The authentication is not working correctly, and you find the error shown in the exhibit in the CPPM Event Viewer.
What should you check?
That the IP address that the MC is using to reach CPPM matches the one defined for the device on CPPM
That the MC has valid admin credentials configured on it for logging into the CPPM
That the MC has been added as a domain machine on the Active Directory domain with which CPPM is synchronized
That the shared secret configured for the CPPM authentication server matches the one defined for the device on CPPM
The Answer Is:
AExplanation:
The exhibit shows an error in the CPPM Event Viewer: "RADIUS authentication attempt from unknown NAD 10.1.10.8:1812." This indicates that a new HPE Aruba Networking Mobility Controller (MC) is attempting to send RADIUS authentication requests to HPE Aruba Networking ClearPass Policy Manager (CPPM), but CPPM does not recognize the MC as a Network Access Device (NAD), resulting in the authentication failure.
Unknown NAD Error: In CPPM, a NAD is a device (e.g., an MC, switch, or AP) that sends RADIUS requests to CPPM for authentication. Each NAD must be configured in CPPM with its IP address and a shared secret. The error "unknown NAD 10.1.10.8:1812" means that the IP address 10.1.10.8 (the source IP of the MC’s RADIUS request) is not listed as a NAD in CPPM’s configuration, so CPPM rejects the request.
Option A, "That the IP address that the MC is using to reach CPPM matches the one defined for the device on CPPM," is correct. You need to check that the MC’s IP address (10.1.10.8) is correctly configured as a NAD in CPPM. In CPPM, go to Configuration > Network > Devices, and verify that a NAD entry exists for 10.1.10.8. If the IP address does not match (e.g., due to NAT, a different interface, or a misconfiguration), CPPM will reject the request as coming from an unknown NAD.
Option B, "That the MC has valid admin credentials configured on it for logging into the CPPM," is incorrect. Admin credentials on the MC are used for management access (e.g., SSH, web UI), not for RADIUS authentication. RADIUS communication between the MC and CPPM uses a shared secret, not admin credentials.
Option C, "That the MC has been added as a domain machine on the Active Directory domain with which CPPM is synchronized," is incorrect. Adding the MC as a domain machine in Active Directory (AD) is relevant only if the MC itself is authenticating users against AD (e.g., for machine authentication), but this is not required for the MC to act as a NAD sending RADIUS requests to CPPM.
Option D, "That the shared secret configured for the CPPM authentication server matches the one defined for the device on CPPM," is incorrect in this context. While a shared secret mismatch would cause authentication failures, it would not result in an "unknown NAD" error. The "unknown NAD" error occurs before the shared secret is checked, as CPPM does not recognize the IP address as a valid NAD.
The HPE Aruba Networking ClearPass Policy Manager 6.11 User Guide states:
"The error ‘RADIUS authentication attempt from unknown NAD
Additionally, the HPE Aruba Networking AOS-8 8.11 User Guide notes:
"When configuring a Mobility Controller to use ClearPass as a RADIUS server, ensure that the MC’s IP address is added as a NAD in ClearPass. If ClearPass logs an ‘unknown NAD’ error, verify that the IP address the MC uses to send RADIUS requests (e.g., the source IP of the request) matches the IP address configured in ClearPass under Configuration > Network > Devices." (Page 498, Configuring RADIUS Authentication Section)
What is a correct use case for using the specified certificate file format?
using a PKCS7 file to install a certificate plus and its private key on a device
using a PKCS12 file to install a certificate plus its private key on a device
using a PEM file to install a binary encoded certificate on a device
using a PKCS7 file to install a binary encoded private key on a device
The Answer Is:
BExplanation:
The correct use case for using the specified certificate file format is option B, using a PKCS12 file to install a certificate along with its private key on a device. PKCS12 is a binary format for storing a certificate chain and private key in a single encrypted file. PEM files are Base64 encoded certificate files and are typically used for storing certificates, not private keys, and PKCS7 is used for certificate chains without the private key.
These answers are based on general networking and security practices, specifically within the context of Aruba network device configurations. If you have questions specific to Oracle Database 12c SQL, please provide the relevant details or ask separate questions related to that topic.
Refer to the exhibit.
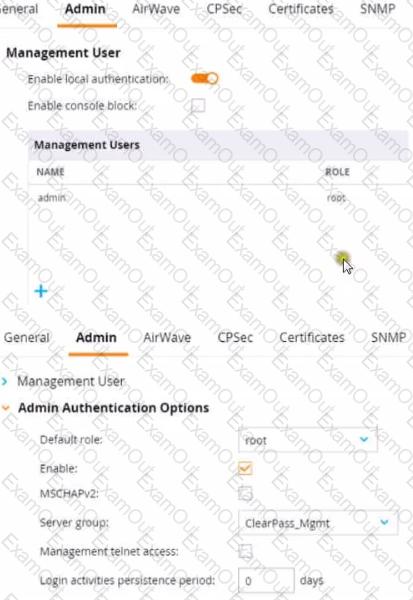
This Aruba Mobility Controller (MC) should authenticate managers who access the Web Ul to ClearPass Policy Manager (CPPM) ClearPass admins have asked you to use RADIUS and explained that the MC should accept managers' roles in Aruba-Admin-Role VSAs
Which setting should you change to follow Aruba best security practices?
Change the local user role to read-only
Clear the MSCHAP check box
Disable local authentication
Change the default role to "guest-provisioning"
The Answer Is:
CExplanation:
For following Aruba best security practices, the setting you should change is to disable local authentication. When integrating with an external RADIUS server like ClearPass Policy Manager (CPPM) for authenticating administrative access to the Mobility Controller (MC), it is a best practice to rely on the external server rather than the local user database. This practice not only centralizes the management of user roles and access but also enhances security by leveraging CPPM's advanced authentication mechanisms.
What does the NIST model for digital forensics define?
how to define access control policies that will properly protect a company's most sensitive data and digital resources
how to properly collect, examine, and analyze logs and other data, in order to use it as evidence in a security investigation
which types of architecture and security policies are best equipped to help companies establish a Zero Trust Network (ZTN)
which data encryption and authentication algorithms are suitable for enterprise networks in a world that is moving toward quantum computing
The Answer Is:
BExplanation:
The National Institute of Standards and Technology (NIST) provides guidelines on digital forensics, which include methodologies for properly collecting, examining, and analyzing digital evidence. This framework helps ensure that digital evidence is handled in a manner that preserves its integrity and maintains its admissibility in legal proceedings:
Digital Forensics Process: This process involves steps to ensure that data collected from digital sources can be used reliably in investigations and court cases, addressing chain-of-custody issues, proper evidence handling, and detailed documentation of forensic procedures.
Which is a correct description of a stage in the Lockheed Martin kill chain?
In the delivery stage, malware collects valuable data and delivers or exfilltrated it to the hacker.
In the reconnaissance stage, the hacker assesses the impact of the attack and how much information was exfilltrated.
In the weaponization stage, which occurs after malware has been delivered to a system, the malware executes Its function.
In the exploitation and installation phases, malware creates a backdoor into the infected system for the hacker.
The Answer Is:
DExplanation:
The Lockheed Martin Cyber Kill Chain model describes the stages of a cyber attack. In the exploitation phase, the attacker uses vulnerabilities to gain access to the system. Following this, in the installation phase, the attacker installs a backdoor or other malicious software to ensure persistent access to the compromised system. This backdoor can then be used to control the system, steal data, or execute additional attacks.

