Refer to the exhibit.

A company has an HPE Aruba Networking Instant AP cluster. A Windows 10 client is attempting to connect to a WLAN that enforces WPA3-Enterprise with authentication to HPE Aruba Networking ClearPass Policy Manager (CPPM). CPPM is configured to require EAP-TLS. The client authentication fails. In the record for this client's authentication attempt on CPPM, you see this alert.
What is one thing that you check to resolve this issue?
An MC has a WLAN that enforces WPA3-Enterprise with authentication to HPE Aruba Networking ClearPass Policy Manager (CPPM). The WLAN's default role is set to guest. A Mobility Controller (MC) has these roles configured on it:
authenticated
denyall
guest
general-access
guest-logon
logon
stateful-dot1x
switch-logon
voiceA client authenticates. CPPM returns an Access-Accept with an Aruba-User-Role VSA set to general_access. What role does the client receive?
How can ARP be used to launch attacks?
You have been asked to send RADIUS debug messages from an AOS-CX switch to a central SIEM server at 10.5.15.6. The server is already defined on the switch with this command:
logging 10.5.15.6
You enter this command:
debug radius all
What is the correct debug destination?
A company has HPE Aruba Networking Mobility Controllers (MCs), HPE Aruba Networking campus APs, and AOS-CX switches. The company plans to use HPE Aruba Networking ClearPass Policy Manager (CPPM) to classify endpoints by type. The company is contemplating the use of ClearPass's TCP fingerprinting capabilities.
What is a consideration for using those capabilities?
You are checking the Security Dashboard in the Web Ul for your ArubaOS solution and see that Wireless Intrusion Prevention (WIP) has discovered a rogue radio operating in ad hoc mode with open security. What correctly describes a threat that the radio could pose?
What is one way that Control Plane Security (CPsec) enhances security for me network?
Refer to the exhibit.
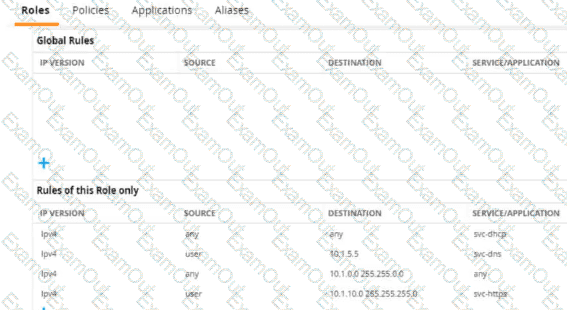
A diem is connected to an ArubaOS Mobility Controller. The exhibit snows all Tour firewall rules that apply to this diem
What correctly describes how the controller treats HTTPS packets to these two IP addresses, both of which are on the other side of the firewall
10.1 10.10
203.0.13.5
What is a Key feature of me ArubaOS firewall?
You have been asked to send RADIUS debug messages from an ArubaOS-CX switch to a central SIEM server at 10.5.15.6. The server is already defined on the switch with this command: logging 10.5.6.12
You enter this command: debug radius all
What is the correct debug destination?

