A customer wants to implement Virtual IP redundancy, such that in case of a ClearPass server outage, 802.1x authentications will not be interrupted. The administrator has enabled a single Virtual IP address on two ClearPass servers.
Which statements accurately describe next steps? (Select two.)
Refer to the exhibit.
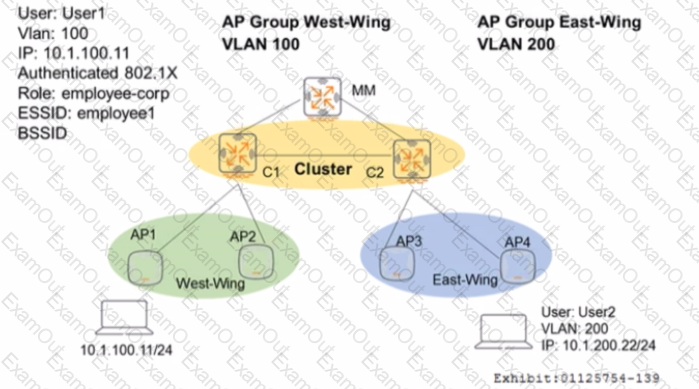
Controllers are configured m a cluster as shown in the exhibit. These are the network details.
• A Mobility Master (MM) manages the cluster.
• The cluster contains two controllers: C l and C2.
• API and AP2 use CI as their Active AP Anchor Controller (A-AAC). with C2 as their Standby AAC (S-AAC).
• AP3 and AP4 use C2 as their A-AAC, with CI as their S-AAC.
User1 establishes a wireless connection via API, where the Active User Anchor Controller (A-UAC) assigned is CI. with C2 as the standby. What happens when User I roams the wireless network and eventually their session is handled by AP3?
Refer to the exhibit.
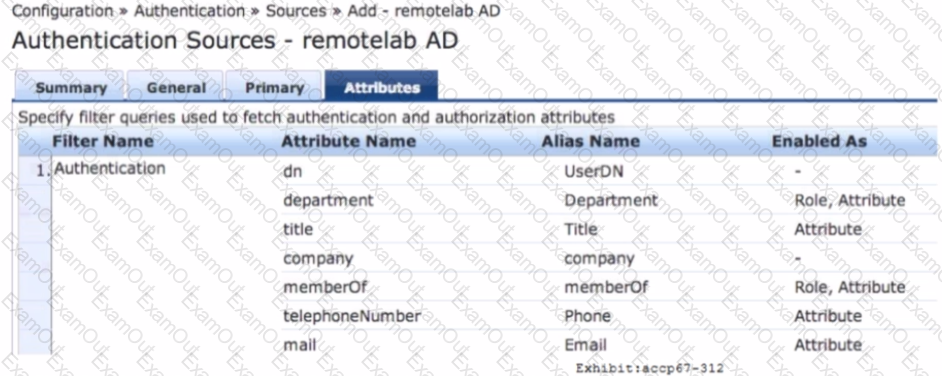
Based on the Attribute configuration shown, which statement accurately describes the status of attribute values?
Refer to the exhibit.
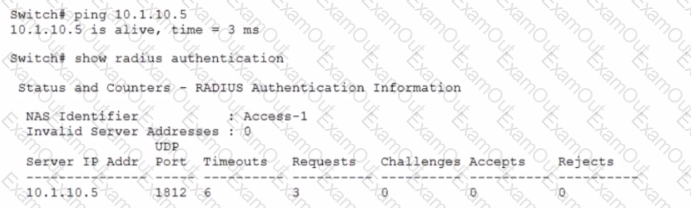
A network administrator sets up 802.1X authentication to a RADIUS server on an AOS-Switch. The RADIUS server and user devices are both set up to use REAP MSCHAPv2. The administrator tests the authentication and sees the output shown in the exhibit. Which issue could cause this output?
Which technologies can prevent split brain in a VSF fabric that includes Aruba 2930F switches?
Which protocol do Mobility Controllers (MCs) use to detect a failed Mobility Master (MM)?
A network administrator can set the OSPF metric-type on an AOS-Switch to Type 1 or Type 2. What is the difference?
Whichstatement is true about the Endpoint Profiler? (Select two.)

