You work as a Network Administrator for XYZ CORP. The company has a TCP/IP-based network environment. The network contains Cisco switches and a Cisco router. A user is unable to access the Internet from Host B. You also verify that Host B is not able to connect to other resources on the network. The IP configuration of Host B is shown below:
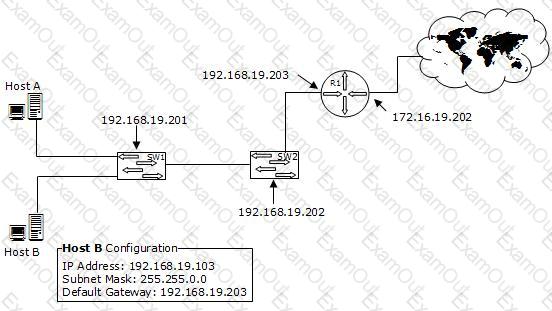
Which of the following is the most likely cause of the issue?
Mike works as a Network Engineer for XYZ CORP. The company has a multi-platform network. Recently, the company faced lots of blended threat issues that lead to several drastic attacks. Mike has been assigned a project to manage the resources and services of the company through both Intranet and Internet to protect the company from these attacks. Mike needs a system that provides auto-discovering and network topology building features to allow him to keep an intuitive view of the IT infrastructure. What will Mike use to meet the requirement of the project?
Victor wants to use Wireless Zero Configuration (WZC) to establish a wireless network connection using his computer running on Windows XP operating system. Which of the following are the most likely threats to his computer? (Choose two)
Which of the following protocols are used to provide secure communication between a client and a server over the Internet? (Choose two)
Which of the following tools can be used by a user to hide his identity?
You work as a Network Administrator for Tech Perfect Inc. The company has a Windows Active Directory-based single domain single forest network. The functional level of the forest is Windows Server 2003. The company has recently provided laptops to its sales team members. You have configured access points in the network to enable a wireless network. The company's security policy states that all users using laptops must use smart cards for authentication. Which of the following authentication techniques will you use to implement the security policy of the company?
You are concerned about rootkits on your network communicating with attackers outside your network. Without using an IDS how can you detect this sort of activity?
Choose the benefits of deploying switches over hubs in your infrastructure. (Choose two)
Sam works as a Network Administrator for XYZ CORP. The computers in the company run Windows Vista operating system, and they are continuously connected to the Internet. This makes the network of the company susceptible to attacks from unauthorized users. Which of the following will Sam choose to protect the network of the company from such attacks?
Which of the following statements about Secure Sockets Layer (SSL) are true? (Choose two)

