You are the program manager for your organization. Management has asked that you determine when resources, such as leased equipment, are no longer needed so that you may release the resources to save time, money, and utilization of resources within your program. What program management process is management asking you to perform?
You are taking over the security of an existing network. You discover a machine that is not being used as such, but has software on it that emulates the activity of a sensitive database server. What is this?
Which of the following are countermeasures to prevent unauthorized database access attacks?
Each correct answer represents a complete solution. Choose all that apply.
Consider the following diagram:
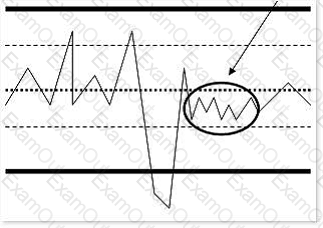
What is the highlighted area of the diagram known as?
Maria works as a professional Ethical Hacker. She has been assigned the project of testing the security of www.gentech.com. She is using dumpster diving to gather information about Gentech Inc. In which of the following steps of malicious hacking does dumpster diving come under?

