You have compromised a Windows XP system and Injected the Meterpreter payload into the lsass process. While looking over the system you notice that there is a popular password management program on the system. When you attempt to access the file that contains the password you find it is locked. Further investigation reveals that it is locked by the passmgr process. How can you use the Meterpreter to get access to this file?
What is the purpose of the following command?
C:\>wmic /node:[target IP] /user:[admin-user]
/password:[password] process call create [command]
You are conducting a penetration test for a private contractor located in Singapore. The scope extends to all internal hosts controlled by the company, you have gathered necessary hold-harmless and nondisclosure agreements. Which action by your group can incur criminal liability under Chapter 50a, Computer Misuse Act?
Analyze the command output below, what action is being performed by the tester?
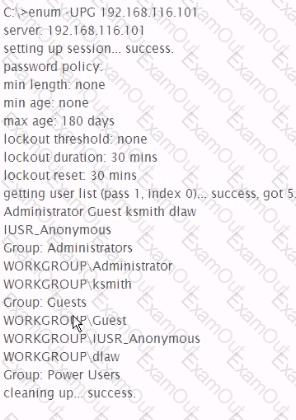
A penetration tester wishes to stop the Windows Firewall process on a remote host running Windows Vista She issues the following commands:
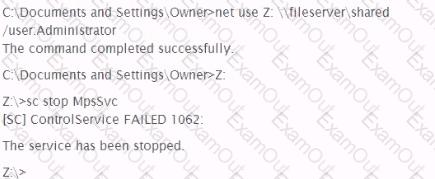
A check of the remote host indicates that Windows Firewall is still running. Why did the command fail?
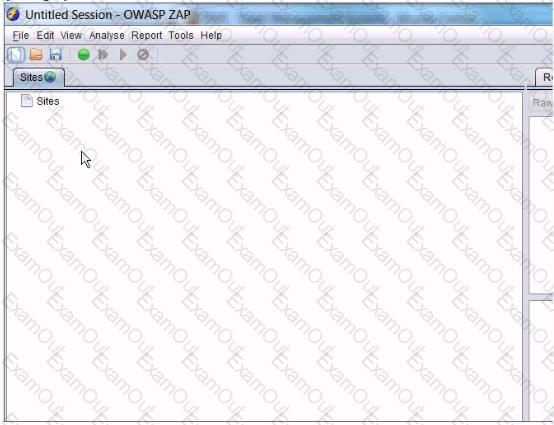
In the screen shot below, which selections would you need click in order to intercept and alter all http traffic passing through OWASP ZAP?
Analyze the screenshot below. What event is depicted?
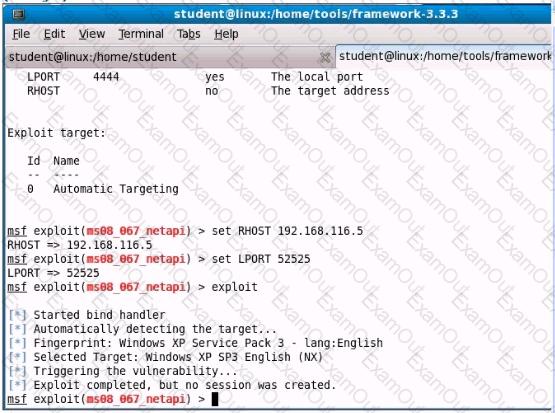
A penetration tester used a client-side browser exploit from metasploit to get an unprivileged shell prompt on the target Windows desktop. The penetration tester then tried using the getsystem command to perform a local privilege escalation which failed. Which of the following could resolve the problem?
Which of the following is the number of bits of encryption that 64-bit Wired Equivalent Privacy (WEP) effectively provides?
You are pen testing a system and want to use Metasploit 3.X to open a listening port on the system so you can access it via a netcat shell. Which stager would you use to have the system listen on TCP port 50000?

