What command will correctly reformat the Unix passwordcopy and shadowcopy Tiles for input to John The Ripper?
Why is it important to have a cheat sheet reference of database system tables when performing SQL Injection?
A client with 7200 employees in 14 cities (all connected via high speed WAN connections) has suffered a major external security breach via a desktop which cost them more than SI 72.000 and the loss of a high profile client. They ask you to perform a desktop vulnerability assessment to identify everything that needs to be patched. Using Nessus you find tens of thousands of vulnerabilities that need to be patched. In the report you find workstations running several Windows OS versions and service pack levels, anti-virus software from multiple vendors several major browser versions and different versions of Acrobat Reader. Which of the following recommendations should you provide with the report?
While scanning a remote system that is running a web server with a UDP scan and monitoring the scan with a sniffer, you notice that the target is responding with ICMP Port Unreachable only once a second What operating system is the target likely running?
When attempting to crack a password using Rainbow Tables, what is the output of the reduction function?
What is the main difference between LAN MAN and NTLMv1 challenge/responses?
Approximately how many packets are usually required to conduct a successful FMS attack onWEP?
You have compromised a Windows workstation using Metasploit and have injected the Meterpreter payload into the smss process. You want to dump the SAM database of the remote system so you can crack it offline. Which Meterpreter module would you need to load in addition to the defaults so that you can accomplish this?
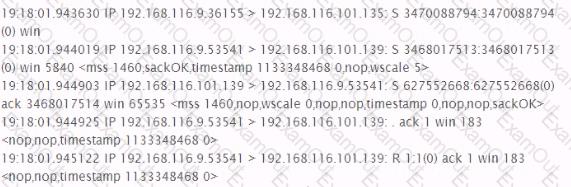
Based on the partial appdefstrig rile listed below, which port scan signature is classified by AMap as harmful?
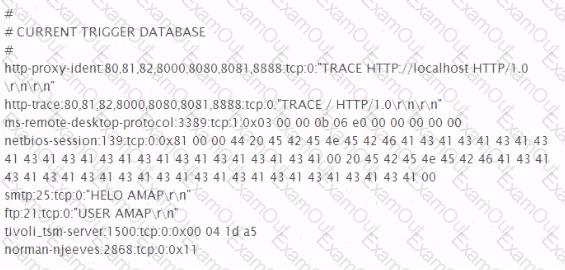
Analyze the excerpt from a packet capture between the hosts 192.168.116.9 and 192.168.116.101. What factual conclusion can the tester draw from this output?