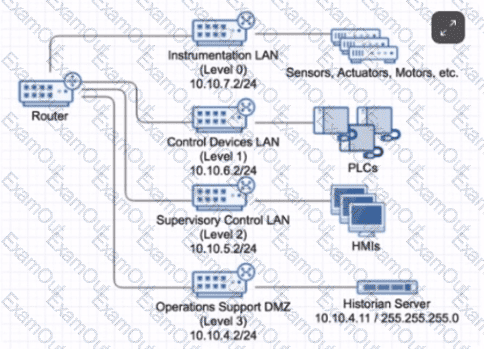
What can be configured on the router so that it can most effectively implement and enforce zones for the shown subnets?
What mechanism could help defeat an attacker's attempt to hide evidence of his/her actions on the target system?
What is a benefit of log aggregation?
An administrator wants to script the deployment of a security policy, over the network, to a group of workstations not managed by Active Directory. What tool could be used to accomplish this task?
Which of the following is a containment task within the six step incident handling process?
Which of the following is a facilitated tabletop exercise that is run in odd years and provides an overall public Lessons Learned report each year it is run?
Which resource includes a standardized categorization of common software vulnerabilities?
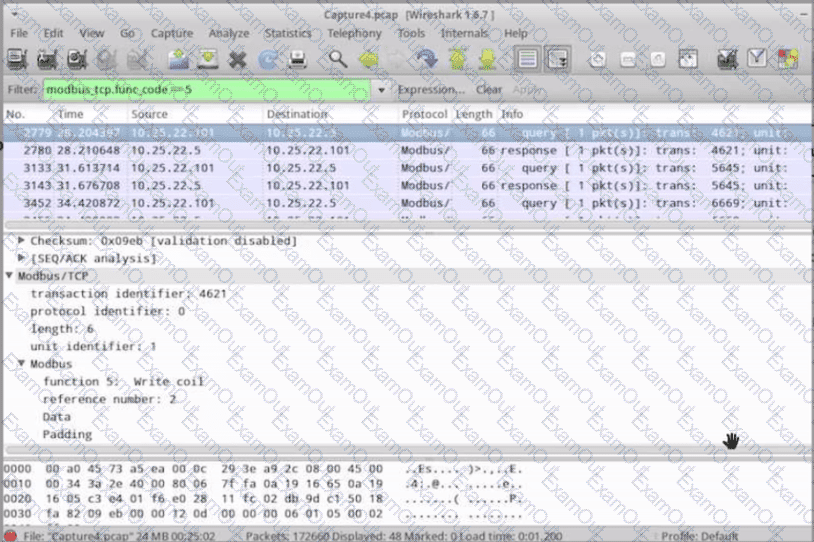
What is the purpose of the traffic shown in the screenshot?
For a SQL injection login authentication bypass to work on a website, it will contain a username comparison that the database finds to be true. What else is required for the bypass to work?
An administrator relaxes the password policy during disaster recovery operations. What is the result of this action?

