Which of the following is an outcome of the initial triage during incident response?
The matrix in the screen shot below would be created during which process?

Which of the following is an SNMPv3 security feature that was not provided by earlier versions of the protocol?
An incident response team is handling a worm infection among their user workstations. They created an IPS signature to detect and block worm activity on the border IPS, then removed the worm’s artifacts or workstations triggering the rule. Despite this action, worm activity continued for days after. Where did the incident response team fail?
Although the packet listed below contained malware, it freely passed through a layer 3 switch. Why didn’t the switch detect the malware in this packet?

Why would the pass action be used in a Snort configuration file?
Why would a Cisco network device with the latest updates and patches have the service config setting enabled, making the device vulnerable to the TFTP Server Attack?
The security team wants to detect connections that can compromise credentials by sending them in plaintext across the wire. Which of the following rules should they enable on their IDS sensor?
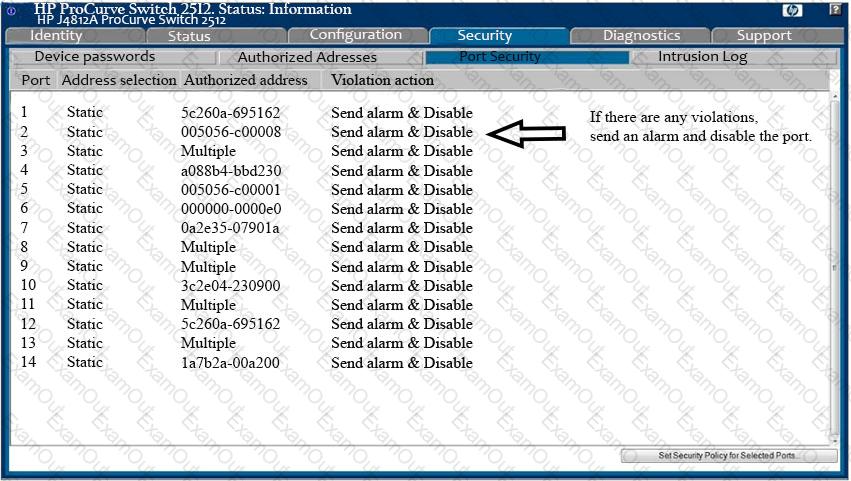
Analyze the screenshot below. Which of the following attacks can be mitigated by these configuration settings?
A company estimates a loss of $2,374 per hour in sales if their website goes down. Their webserver hosting site’s documented downtime was 7 hours each quarter over the last two years. Using the information, what can the analyst determine?

