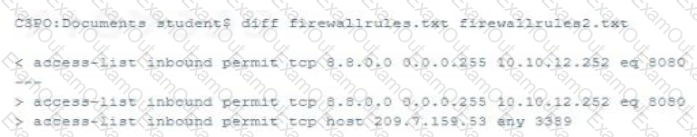
Which of the following actions produced the output seen below?
A security incident investigation identified the following modified version of a legitimate system file on a compromised client:
C:\Windows\System32\winxml.dll Addition Jan. 16, 2014 4:53:11 PM
The infection vector was determined to be a vulnerable browser plug-in installed by the user. Which of the organization’s CIS Controls failed?
An auditor is validating the policies and procedures for an organization with respect to a control for Data Recovery. The organization’s control states they will completely back up critical servers weekly, with incremental backups every four hours. Which action will best verify success of the policy?
Executive management approved the storage of sensitive data on smartphones and tablets as long as they were encrypted. Later a vulnerability was announced at an information security conference that allowed attackers to bypass the device’s authentication process, making the data accessible. The smartphone manufacturer said it would take six months for the vulnerability to be fixed and distributed through the cellular carriers. Four months after the vulnerability was announced, an employee lost his tablet and the sensitive information became public.
What was the failure that led to the information being lost?
What documentation should be gathered and reviewed for evaluating an Incident Response program?
Janice is auditing the perimeter of the network at Sugar Water InC. According to documentation, external SMTP traffic is only allowed to and from 10.10.10.25. Which of the following actions would demonstrate the rules are configured incorrectly?
An organization is implementing a control for the Limitation and Control of Network Ports, Protocols, and Services CIS Control. Which action should they take when they discover that an application running on a web server is no longer needed?
Which of the following should be measured and analyzed regularly when implementing the Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers CIS Control?
Which of the following is used to prevent spoofing of e-mail addresses?
An administrator looking at a web application’s log file found login attempts by the same host over several seconds. Each user ID was attempted with three different passwords. The event took place over 5 seconds.
ROOT
TEST
ADMIN
SQL
USER
NAGIOSGUEST
What is the most likely source of this event?

