The use of alert thresholding in an IDS can reduce the volume of repeated alerts, but introduces which of the following vulnerabilities?
Which results will be returned with the following Google search query?
site:target.com -site:Marketing.target.com accounting
Which of the following settings enables Nessus to detect when it is sending too many packets and the network pipe is approaching capacity?
At a Windows Server command prompt, which command could be used to list the running services?
Internet Protocol Security IPSec is actually a suite of protocols. Each protocol within the suite provides different functionality. Collective IPSec does everything except.
What network security concept requires multiple layers of security controls to be placed throughout an IT infrastructure, which improves the security posture of an organization to defend against malicious attacks or potential vulnerabilities?
Which protocol is used for setting up secured channels between two devices, typically in VPNs?
Emil uses nmap to scan two hosts using this command.
nmap -sS -T4 -O 192.168.99.1 192.168.99.7
He receives this output:
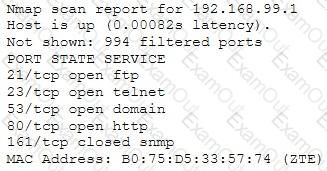
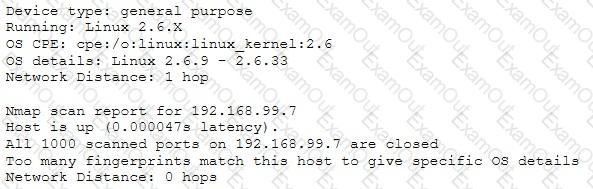
What is his conclusion?
Which tier in the N-tier application architecture is responsible for moving and processing data between the tiers?
Scenario: 1. Victim opens the attacker’s web site.
2. Attacker sets up a web site which contains interesting and attractive content like 'Do you want to make S100 In a day?',
3. Victim clicks to the interesting and attractive content url.
4- Attacker creates a transparent iframe' in front of the url which victim attempt to click, so victim thinks that he/she clicks to the 'Do you want to make $1000 in a day?' url but actually he/sne clicks to the content or url that exists in the transparent iframe' which is setup by the attacker.
What is the name of the attack which is mentioned in the scenario?
To determine if a software program properly handles a wide range of invalid input, a form of automated testing can be used to randomly generate invalid input in an attempt to crash the program.
What term is commonly used when referring to this type of testing?
An Intrusion Detection System (IDS) has alerted the network administrator to a possibly malicious sequence of packets sent to a Web server in the network's external DMZ. The packet traffic was captured by the IDS and saved to a PCAP file.
What type of network tool can be used to determine if these packets are genuinely malicious or simply a false positive?
The "gray box testing" methodology enforces what kind of restriction?
What does a firewall check to prevent particular ports and applications from getting packets into an organization?
An attacker attaches a rogue router in a network. He wants to redirect traffic to a LAN attached to his router as part of a man-in-the-middle attack. What measure on behalf of the legitimate admin can mitigate this attack?

