Which of the following lists are valid data-gathering activities associated with a risk assessment?
Which property ensures that a hash function will not produce the same hashed value for two different messages?
In order to show improvement of security over time, what must be developed?
A developer for a company is tasked with creating a program that will allow customers to update their billing and shipping information. The billing address field used is limited to 50 characters. What pseudo code would the developer use to avoid a buffer overflow attack on the billing address field?
A company has five different subnets: 192.168.1.0, 192.168.2.0, 192.168.3.0, 192.168.4.0 and 192.168.5.0. How can NMAP be used to scan these adjacent Class C networks?
A pentester is using Metasploit to exploit an FTP server and pivot to a LAN. How will the pentester pivot using Metasploit?
The following is part of a log file taken from the machine on the network with the IP address of 192.168.1.106:
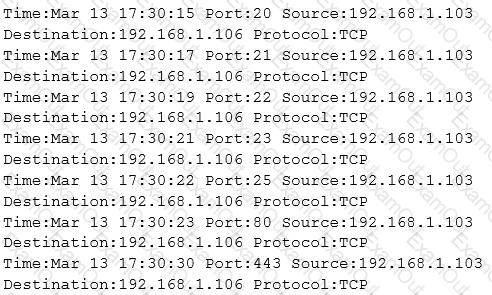
What type of activity has been logged?
To send a PGP encrypted message, which piece of information from the recipient must the sender have before encrypting the message?
A person approaches a network administrator and wants advice on how to send encrypted email from home. The end user does not want to have to pay for any license fees or manage server services. Which of the following is the most secure encryption protocol that the network administrator should recommend?
Smart cards use which protocol to transfer the certificate in a secure manner?
A company firewall engineer has configured a new DMZ to allow public systems to be located away from the internal network. The engineer has three security zones set:
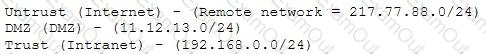
The engineer wants to configure remote desktop access from a fixed IP on the remote network to a remote desktop server in the DMZ. Which rule would best fit this requirement?
A newly discovered flaw in a software application would be considered which kind of security vulnerability?
Which tool can be used to silently copy files from USB devices?
Least privilege is a security concept that requires that a user is
What is the name of the international standard that establishes a baseline level of confidence in the security functionality of IT products by providing a set of requirements for evaluation?

