Which of the following would be the best reason for sending a single SMTP message to an address that does not exist within the target company?
What ICMP message types are used by the ping command?
Which Windows system tool checks integrity of critical files that has been digitally signed by Microsoft?
What does an ICMP (Code 13) message normally indicates?
A XYZ security System Administrator is reviewing the network system log files.
He notes the following:
Network log files are at 5 MB at 12:00 noon.
At 14:00 hours, the log files at 3 MB.
What should he assume has happened and what should he do about the situation?
What are the two basic types of attacks? (Choose two.
What is "Hacktivism"?
Which type of Nmap scan is the most reliable, but also the most visible, and likely to be picked up by and IDS?
You have initiated an active operating system fingerprinting attempt with nmap against a target system:

What operating system is the target host running based on the open ports shown above?
A very useful resource for passively gathering information about a target company is:
Bob is acknowledged as a hacker of repute and is popular among visitors of “underground” sites. Bob is willing to share his knowledge with those who are willing to learn, and many have expressed their interest in learning from him. However, this knowledge has a risk associated with it, as it can be used for malevolent attacks as well.
In this context, what would be the most affective method to bridge the knowledge gap between the “black” hats or crackers and the “white” hats or computer security professionals? (Choose the test answer)
John has scanned the web server with NMAP. However, he could not gather enough information to help him identify the operating system running on the remote host accurately.
What would you suggest to John to help identify the OS that is being used on the remote web server?
What port scanning method is the most reliable but also the most detectable?
At a Windows Server command prompt, which command could be used to list the running services?
Which of the following is considered an acceptable option when managing a risk?
The following excerpt is taken from a honeyput log. The log captures activities across three days. There are several intrusion attempts; however, a few are successful. Study the log given below and answer the following question:
(Note: The objective of this questions is to test whether the student has learnt about passive OS fingerprinting (which should tell them the OS from log captures): can they tell a SQL injection attack signature; can they infer if a user ID has been created by an attacker and whether they can read plain source – destination entries from log entries.)
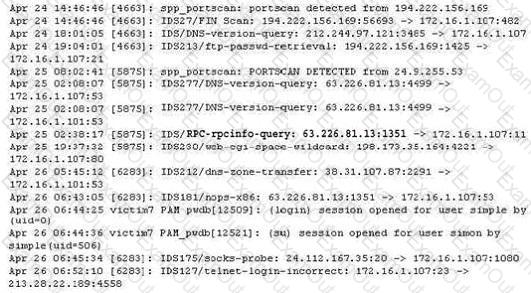
What can you infer from the above log?
Why would an attacker want to perform a scan on port 137?
Which of the following is an automated vulnerability assessment tool?
Exhibit
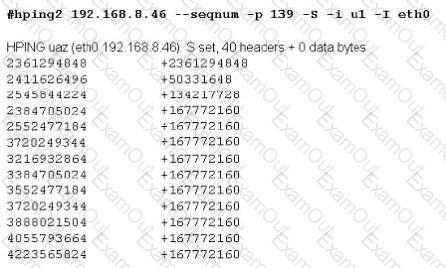
Joe Hacker runs the hping2 hacking tool to predict the target host’s sequence numbers in one of the hacking session.
What does the first and second column mean? Select two.
_________ is one of the programs used to wardial.

