A remote user tries to login to a secure network using Telnet, but accidently types in an invalid user name or password. Which responses would NOT be preferred by an experienced Security Manager? (multiple answer)
In the context of password security, a simple dictionary attack involves loading a dictionary file (a text file full of dictionary words) into a cracking application such as L0phtCrack or John the Ripper, and running it against user accounts located by the application. The larger the word and word fragment selection, the more effective the dictionary attack is. The brute force method is the most inclusive, although slow. It usually tries every possible letter and number combination in its automated exploration.
If you would use both brute force and dictionary methods combined together to have variation of words, what would you call such an attack?
Global deployment of RFC 2827 would help mitigate what classification of attack?
Sniffing is considered an active attack.
Which of the following are well know password-cracking programs?(Choose all that apply.
Which of the following Exclusive OR transforms bits is NOT correct?
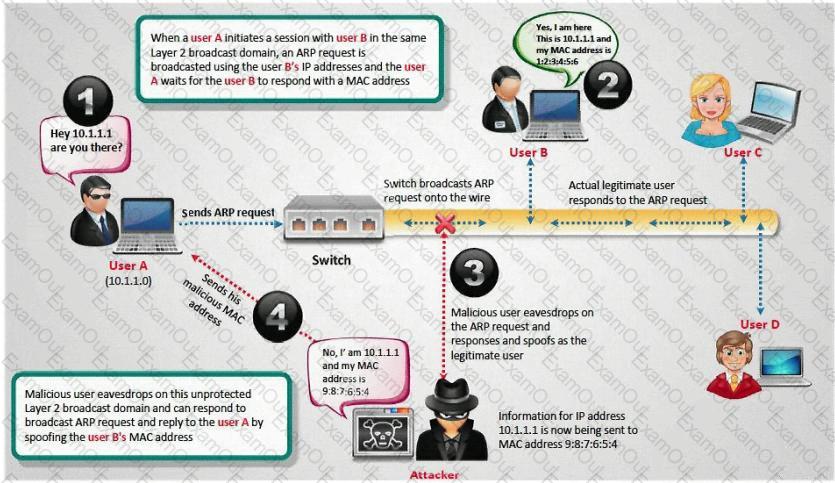
How do you defend against ARP Poisoning attack? (Select 2 answers)
In the software security development life cyle process, threat modeling occurs in which phase?
SSL has been seen as the solution to a lot of common security problems. Administrator will often time make use of SSL to encrypt communications from points A to point B. Why do you think this could be a bad idea if there is an Intrusion Detection System deployed to monitor the traffic between point A and B?
What do you call a pre-computed hash?
What type of port scan is represented here.

SOAP services use which technology to format information?
WWW wanderers or spiders are programs that traverse many pages in the World Wide Web by recursively retrieving linked pages. Search engines like Google, frequently spider web pages for indexing. How will you stop web spiders from crawling certain directories on your website?
You are writing security policy that hardens and prevents Footprinting attempt by Hackers. Which of the following countermeasures will NOT be effective against this attack?
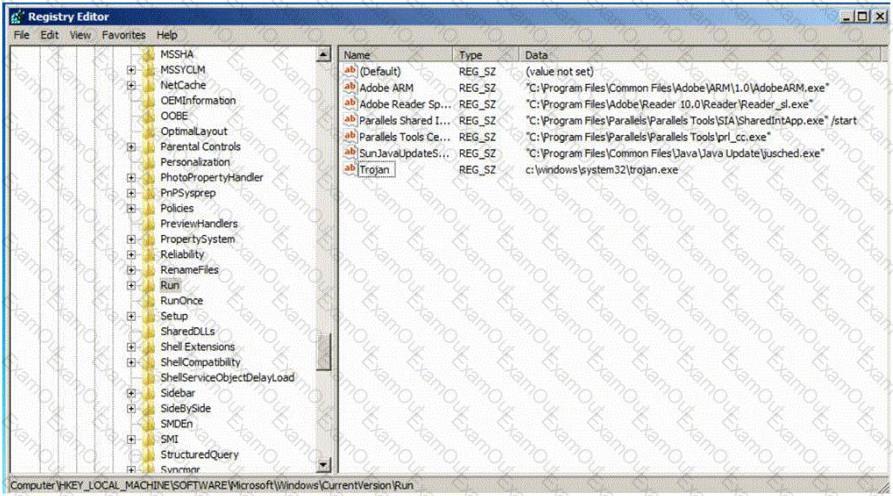
Which of the following Registry location does a Trojan add entries to make it persistent on Windows 7? (Select 2 answers)
What is the broadcast address for the subnet 190.86.168.0/22?
Blane is a security analyst for a law firm. One of the lawyers needs to send out an email to a client but he wants to know if the email is forwarded on to any other recipients. The client is explicitly asked not to re-send the email since that would be a violation of the lawyer's and client's agreement for this particular case. What can Blane use to accomplish this?
An attacker sniffs encrypted traffic from the network and is subsequently able to decrypt it. The attacker can now use which cryptanalytic technique to attempt to discover the encryption key?
One way to defeat a multi-level security solution is to leak data via
Low humidity in a data center can cause which of the following problems?

