Under what conditions does a secondary name server request a zone transfer from a primary name server?
A zone file consists of which of the following Resource Records (RRs)?
One of your junior administrator is concerned with Windows LM hashes and password cracking. In your discussion with them, which of the following are true statements that you would point out?
Select the best answers.
Susan has attached to her company’s network. She has managed to synchronize her boss’s sessions with that of the file server. She then intercepted his traffic destined for the server, changed it the way she wanted to and then placed it on the server in his home directory. What kind of attack is Susan carrying on?
What is the proper response for a NULL scan if the port is open?
Fingerprinting an Operating System helps a cracker because:
How can you determine if an LM hash you extracted contains a password that is less than 8 characters long?
Assuring two systems that are using IPSec to protect traffic over the internet, what type of general attack could compromise the data?
Which of the following keyloggers cannot be detected by anti-virus or anti-spyware products?
A network admin contacts you. He is concerned that ARP spoofing or poisoning might occur on his network. What are some things he can do to prevent it?
Select the best answers.
Eve is spending her day scanning the library computers. She notices that Alice is using a computer whose port 445 is active and listening. Eve uses the ENUM tool to enumerate Alice machine. From the command prompt, she types the following command.
For /f "tokens=1 %%a in (hackfile.txt) do net use * \\10.1.2.3\c$ /user:"Administrator" %%a
What is Eve trying to do?
Exhibit:
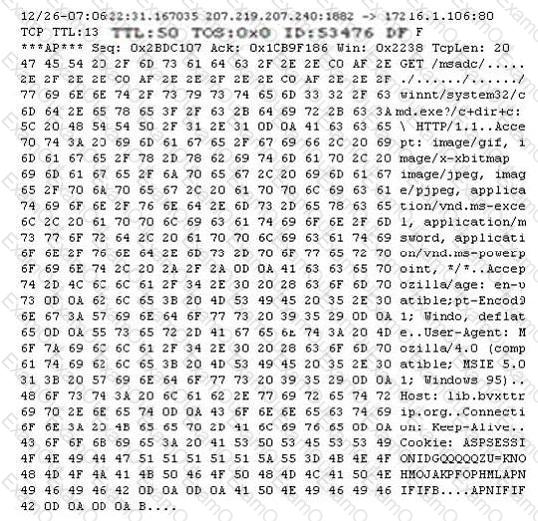
Study the following log extract and identify the attack.
Bob wants to prevent attackers from sniffing his passwords on the wired network. Which of the following lists the best options?
You are a Administrator of Windows server. You want to find the port number for POP3. What file would you find the information in and where?
Select the best answer.
Which of the following is not considered to be a part of active sniffing?
Which tool/utility can help you extract the application layer data from each TCP connection from a log file into separate files?
Ethereal works best on ____________.
You have the SOA presented below in your Zone. Your secondary servers have not been able to contact your primary server to synchronize information. How long will the secondary servers attempt to contact the primary server before it considers that zone is dead and stops responding to queries?
collegae.edu.SOA, cikkye.edu ipad.college.edu. (200302028 3600 3600 604800 3600)
Windows LAN Manager (LM) hashes are known to be weak. Which of the following are known weaknesses of LM? (Choose three)
What is GINA?

