How can you achieve remote access and internet availability in an OT network?
Refer to the exhibit.
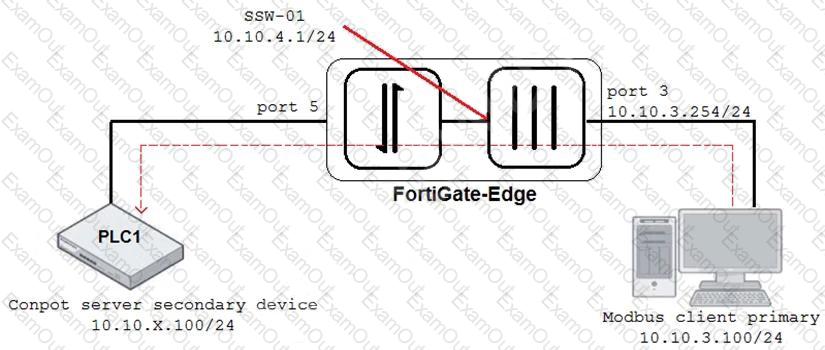
An OT architect has implemented a Modbus TCP with a simulation server Conpot to identify and control the Modus traffic in the OT network. The FortiGate-Edge device is configured with a software switch interface ssw-01.
Based on the topology shown in the exhibit, which two statements about the successful simulation of traffic between client and server are true? (Choose two.)
Refer to the exhibit.
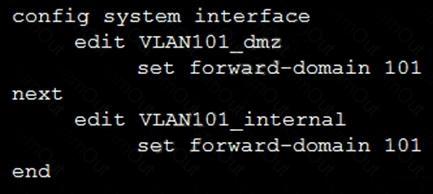
Given the configurations on the FortiGate, which statement is true?
Refer to the exhibits.

Which statement is true about the traffic passing through to PLC-2?
Refer to the exhibit.
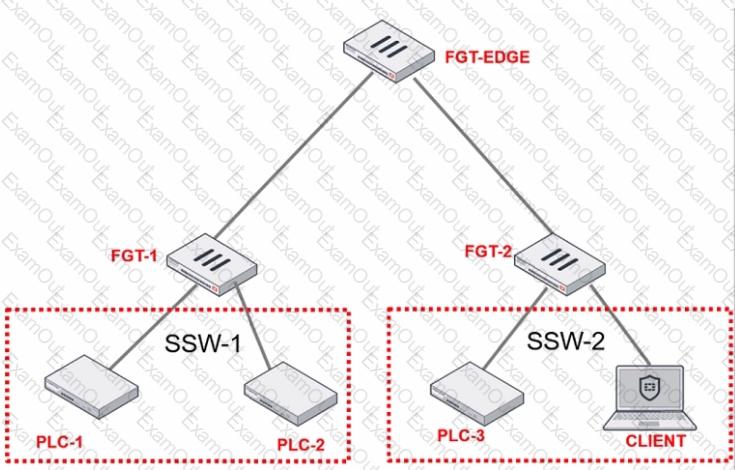
PLC-3 and CLIENT can send traffic to PLC-1 and PLC-2. FGT-2 has only one software switch (SSW-1) connecting both PLC-3 and CLIENT. PLC-3 and CLIENT cannot send traffic to each other.
Which two statements about the traffic between PCL-1 and PLC-2 are true? (Choose two.)
An OT administrator is defining an incident notification policy using FortiSIEM and would like to configure the system with a notification policy. If an incident occurs, the administrator would like to be able to intervene and block an IP address or disable a user in Active Directory from FortiSIEM.
Which step must the administrator take to achieve this task?
An administrator wants to use FortiSoC and SOAR features on a FortiAnalyzer device to detect and block any unauthorized access to FortiGate devices in an OT network.
Which two statements about FortiSoC and SOAR features on FortiAnalyzer are true? (Choose two.)
What are two critical tasks the OT network auditors must perform during OT network risk assessment and management? (Choose two.)
What are two benefits of a Nozomi integration with FortiNAC? (Choose two.)
Refer to the exhibit.
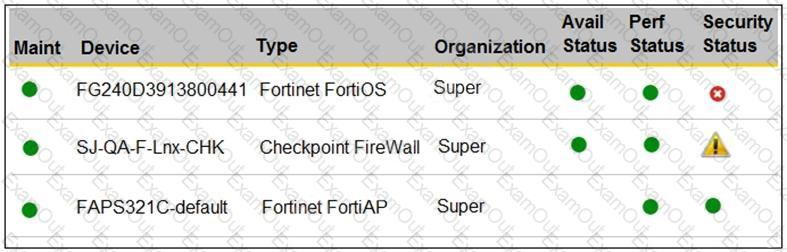
You are navigating through FortiSIEM in an OT network.
How do you view information presented in the exhibit and what does the FortiGate device security status tell you?

