Refer to the exhibit.
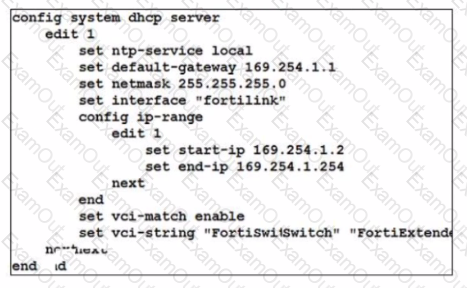
By default FortiOS creates the following DHCP server scope for the FortiLink interface as shown in the exhibit
What is the objective of the vci-string setting?
You are investigating a report of poor wireless performance in a network that you manage. The issue is related to an AP interface in the 5 GHz range You are monitoring the channel utilization over time.
What is the recommended maximum utilization value that an interface should not exceed?
Refer to the exhibits showing AP monitoring information.
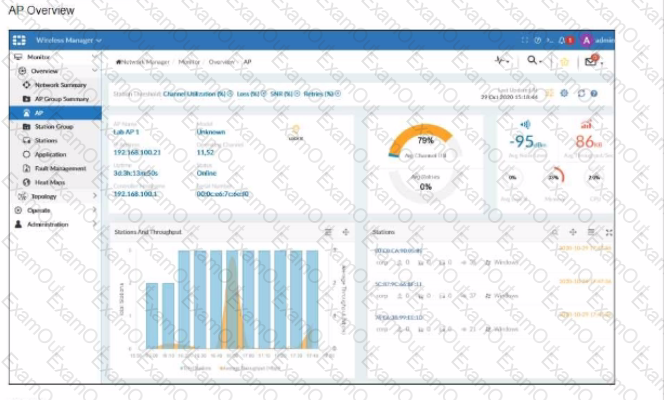
The exhibits show the status of an AP in a small office building. The building is located at the edge of a campus, and users are reporting issues with wireless network performance.
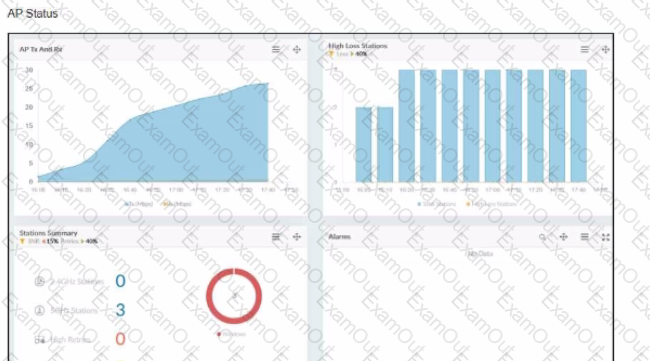
Which configuration change would best improve the wireless network performance?
Which CLI command should an administrator use to view the certificate verification process in real time?
Which CLI command should an administrator use on FortiGate to view the RSSO authentication process in real time?
Which two statements about the use of digital certificates are true? (Choose two.)
Which two statements about FortiSwitch trunks are true? (Choose two.)
Refer to the exhibit.
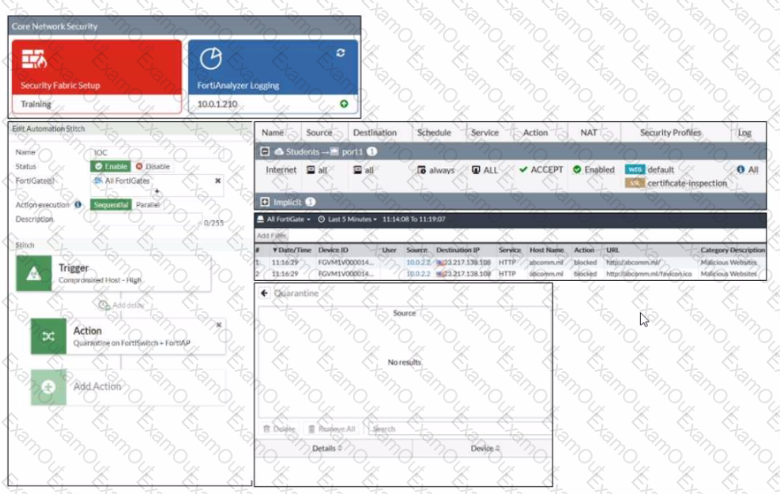
Examine the FortiGate configuration FortiAnalyzer logs and FortiGate widget shown in the exhibit
An administrator is testing the Security Fabric quarantine automation The administrator added FortiAnalyzer to the Security Fabric and configured an automation stitch to automatically quarantine compromised devices The test device (::.:.:.!) s connected to a managed Fort Switch dev :e
After trying to access a malicious website from the test device, the administrator verifies that FortiAnalyzer has a log (or the test connection However the device is not getting quarantined by FortiGate as shown in the quarantine widget
Which two scenarios are likely to cause this issue? (Choose two)

