An administrator configured the following command on FortiGate
config router ospf
sec reszart-mode graceful-restart
Which two statements correctly describe the result of the above command? (Choose two.)
Exhibit.
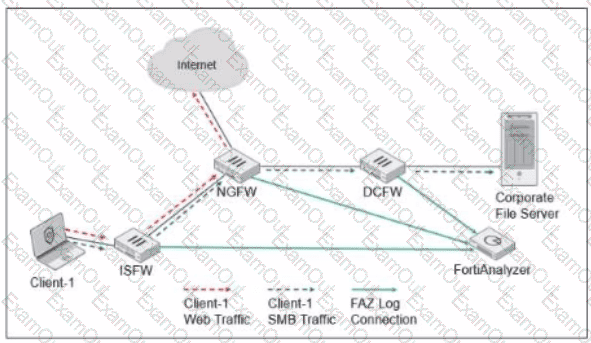
ISFW is installed in the access layer NGFW is performing SNAT and web tittering DCFW is running IPS Which two statements are true regarding the Security Fabric logging? (Choose two.)
Exhibit.
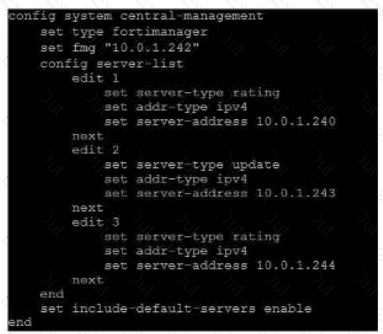
Refer to exhibit, which shows a central management configuration
Which server will FortiGate choose for web filler rating requests if 10.0.1.240 is experiencing an outage?
Which two statements about the Security Fabric are true? (Choose two.)
Refer to the exhibit, which shows device registration on FortiManager.

What can you conclude about the Spoke-1 and Spoke-2 configurations with respect to the information cond: Modified (recent auto-updated)?
How would £=c-ingress and fec-sgress IPsec configuration affect an IPsec tunnel?
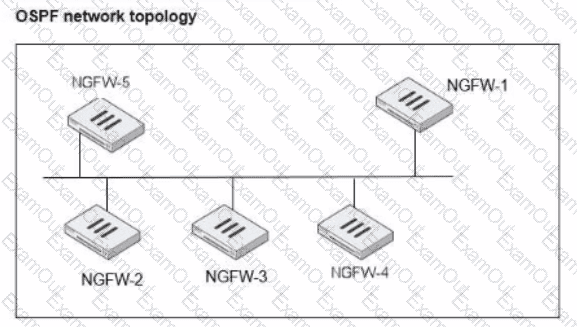
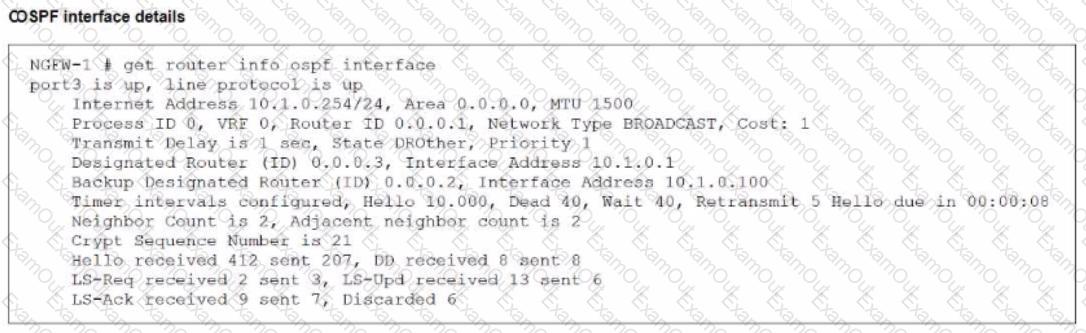
Refer to the exhibit, which shows information about an OSPF interface
What two conclusions can you draw from this command output? (Choose two.)
You want to improve reliability over a lossy IPSec tunnel.
Which combination of IPSec phase 1 parameters should you configure?
Refer to the exhibit, which shows the output of a BGP summary.
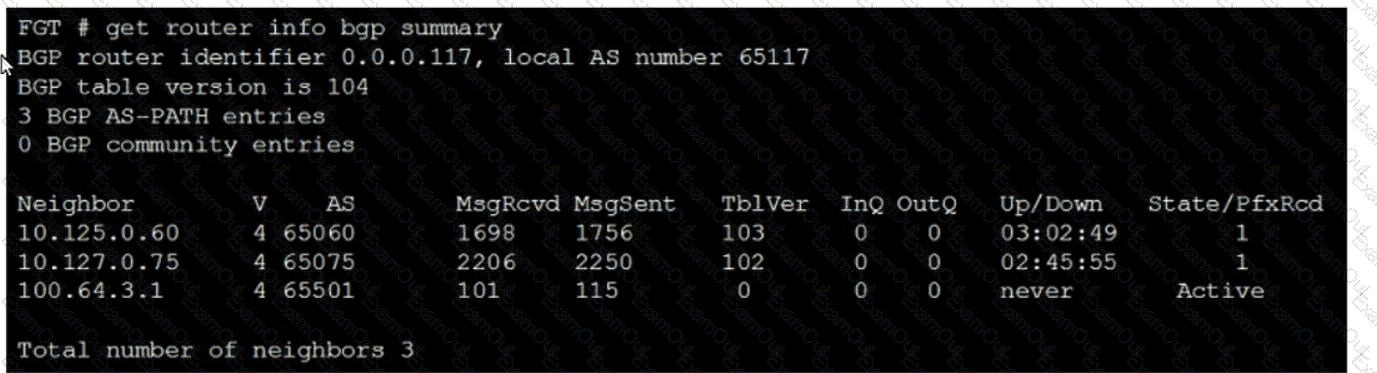
What two conclusions can you draw from this BGP summary? (Choose two.)
Which two statements about the Security fabric are true? (Choose two.)

