Which two ports must be open between FortiSOAR HA nodes'* (Choose two.)
A security analyst has reported unauthorized access to System Configuration. You must review the user's current level of access, and then restrict their access according to your organization's requirements. As part of your auditing process, which two actions should you perform? (Choose two.)
Refer to the exhibit.
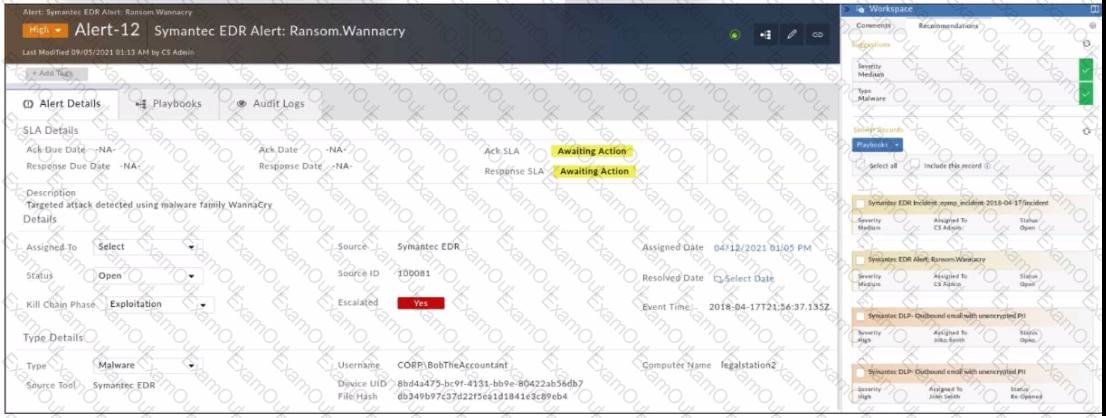
Which two statements about the recommendation engine are true? (Choose two.)

