Which two methods can be used to gather a list of installed applications and application details from a host? (Choose two.)
Where do you look to determine when and why the FortiNAC made an automated network access change?
Refer to the exhibit.
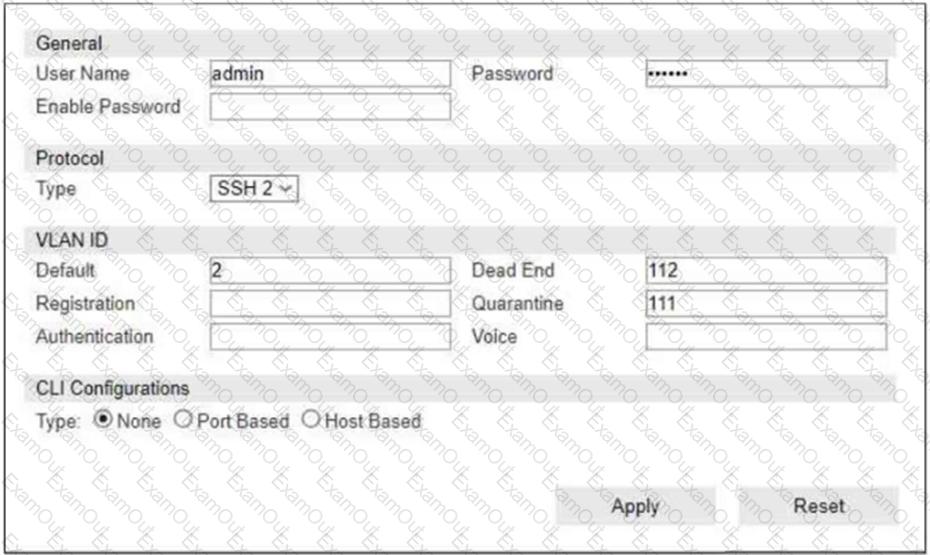
If you are forcing the registration of unknown (rogue) hosts, and an unknown (rogue) host connects to a port on the switch, what occurs?
Which three circumstances trigger Layer 2 polling of infrastructure devices? (Choose three.)
Refer to the exhibit, and then answer the question below.
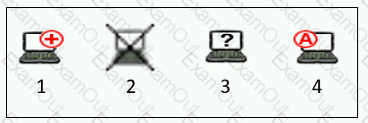
Which host is rogue?
Where do you look to determine which network access policy, if any is being applied to a particular host?
When FortiNAC is managing VPN clients connecting through FortiGate. why must the clients run a FortiNAC agent?
What would happen if a port was placed in both the Forced Registration and the Forced Remediation port groups?
Refer to the exhibit.
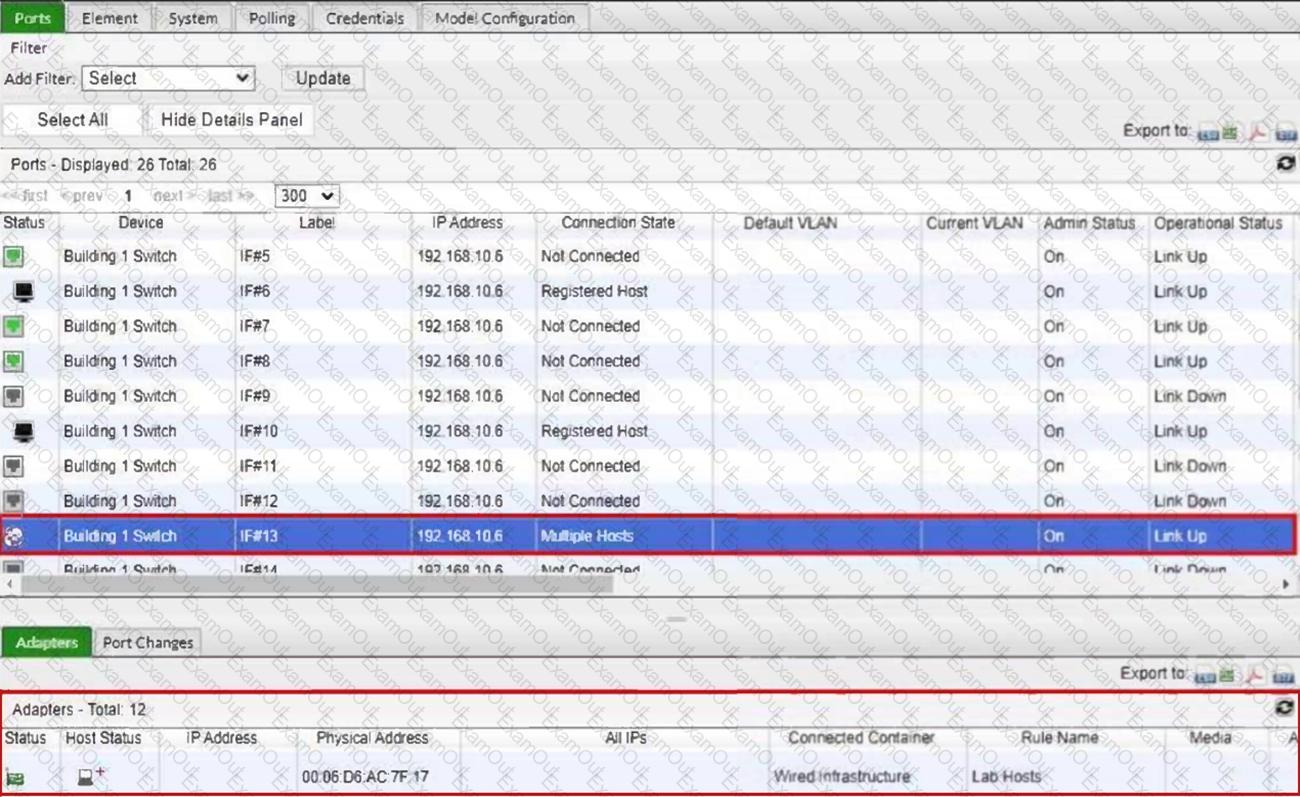
What would happen if the highlighted port with connected hosts was placed in both the Forced Registration and Forced Remediation port groups?
Which system group will force at-risk hosts into the quarantine network, based on point of connection?

