Refer to the exhibit.
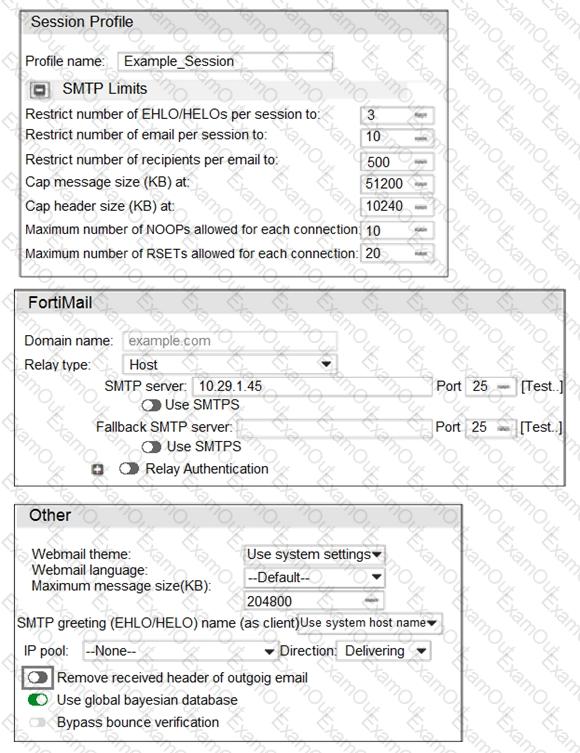
Which message size limit will FortiMail apply to the outbound email?
An organization has different groups of users with different needs in email functionality, such as address book access, mobile device access, email retention periods, and disk quotas.
Which FortiMail feature specific to server mode can be used to accomplish this?
Refer to the exhibit.
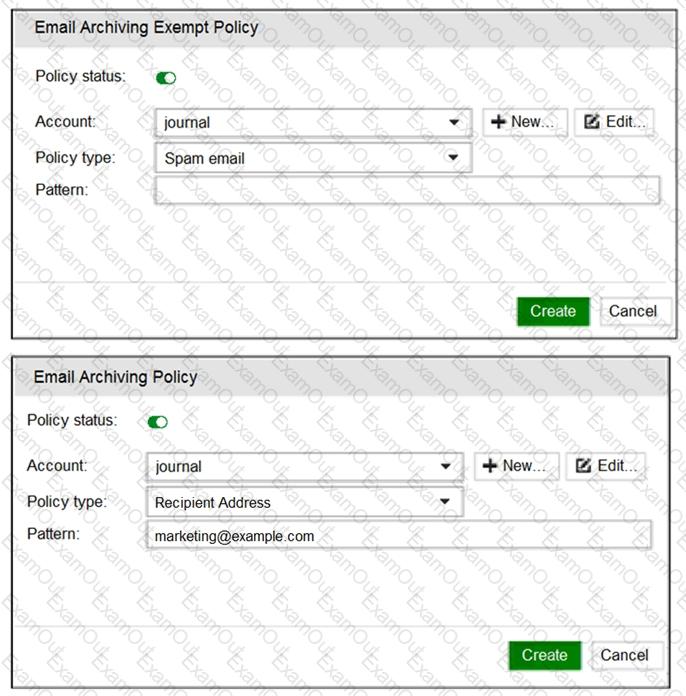
What two archiving actions will FortiMail take when email messages match these archive policies? (Choose two.)
Which statement about how impersonation analysis identifies spoofed email addresses is correct?
A FortiMail administrator is concerned about cyber criminals attempting to get sensitive information from employees using whaling phishing attacks.
What option can the administrator configure to prevent these types of attacks?
Refer to the exhibit.
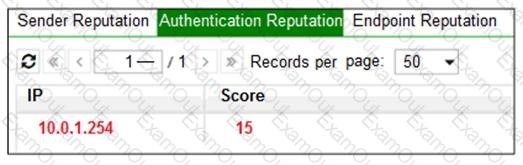
Which configuration change must you make to block an offending IP address temporarily?
Refer to the exhibit.
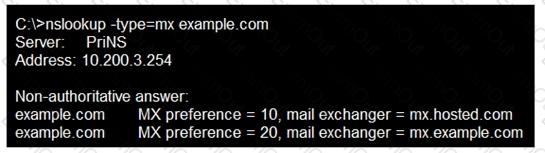
Which two statements about the MTAs of the domain example.com are true? (Choose two.)
Refer to the exhibit.
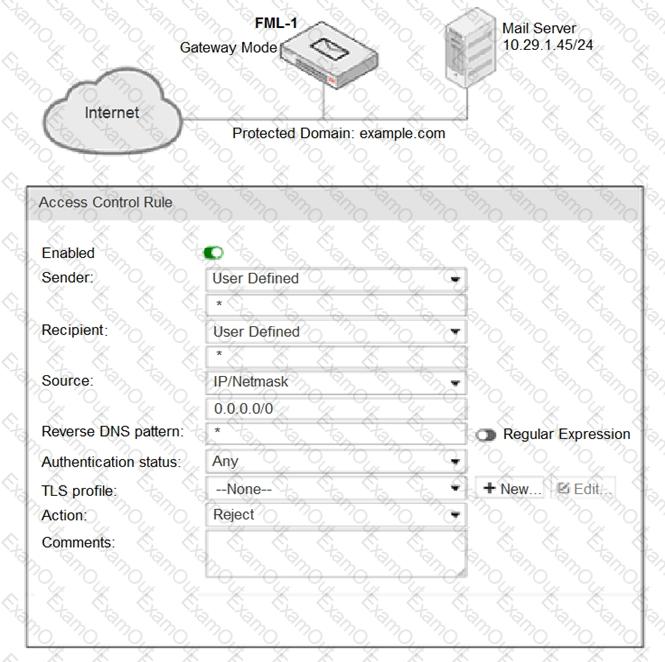
It is recommended that you configure which three access receive settings to allow outbound email from the
example.com domain on FML-1? (Choose three.)
Examine the FortiMail DLP scan rule shown in the exhibit; then answer the question below.
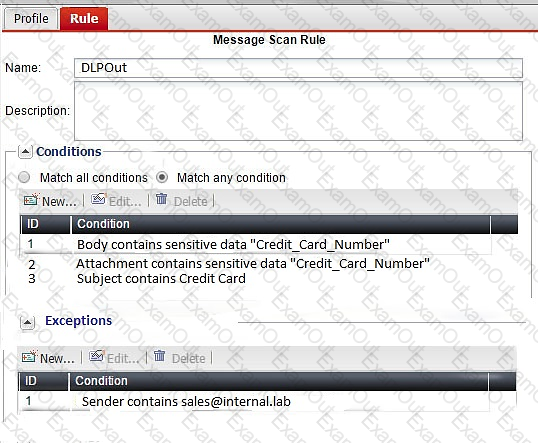
Which of the following statements is true regarding this configuration? (Choose two.)
Examine the nslookup output shown in the exhibit; then answer the question below.
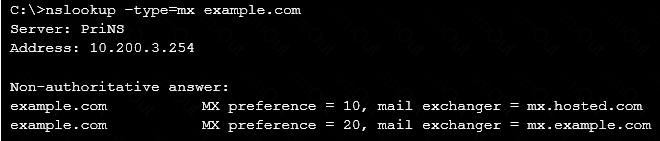
Identify which of the following statements is true regarding the example.com domain’s MTAs. (Choose two.)

