Which statement about FortiClient enterprise management server is true?
An administrator installs FortiClient on Windows Server.
What is the default behavior of real-time protection control?
Which two third-party tools can an administrator use to deploy FortiClient? (Choose two.)
Refer to the exhibit, which shows the Zero Trust Tagging Rule Set configuration.
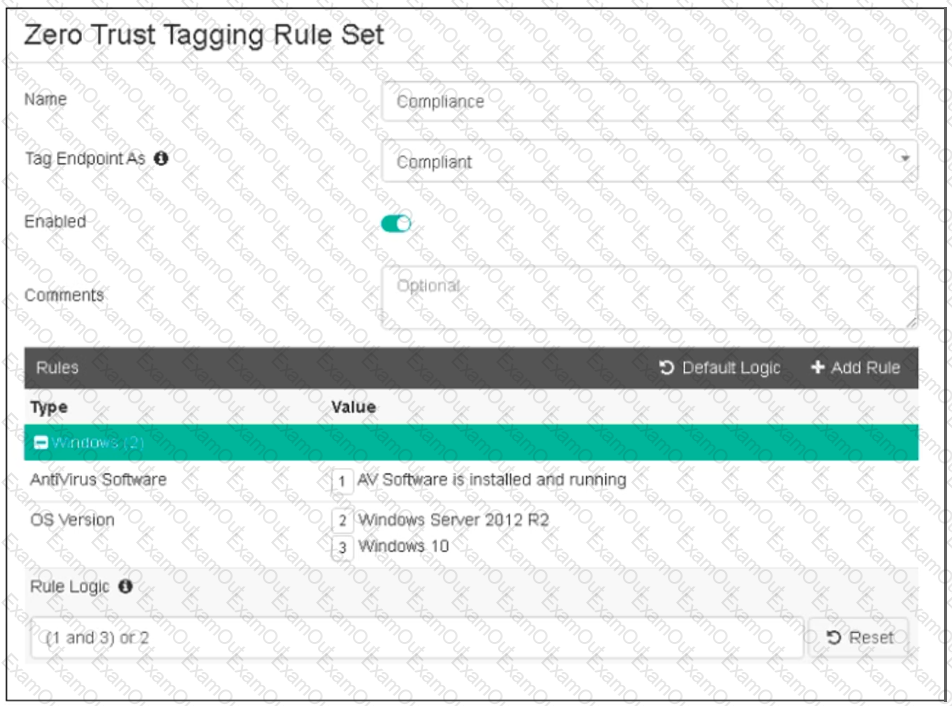
Which two statements about the rule set are true? (Choose two.)
Why does FortiGate need the root CA certificate of FortiClient EMS?
Which three features does FortiClient endpoint security include? (Choose three.)
Refer to the exhibit.
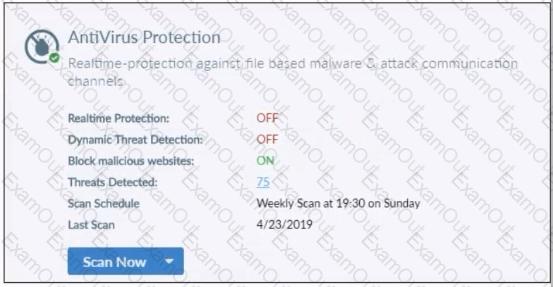
Based on the settings shown in the exhibit what action will FortiClient take when it detects that a user is trying to download an infected file?
An administrator is required to maintain a software inventory on the endpoints. without showing the feature on the FortiClient dashboard What must the administrator do to achieve this requirement?
An administrator has a requirement to add user authentication to the ZTNA access for remote or off-fabric users Which FortiGate feature is required m addition to ZTNA?
In a FortiSandbox integration, what does the remediation option do?

