To complete their day-to-day operations, remote users require access to a TCP-based application that is hosted on a private web server. Which FortiSASE deployment use case provides the most efficient and secure method for meeting the remote users' requirements?
Refer to the exhibits.
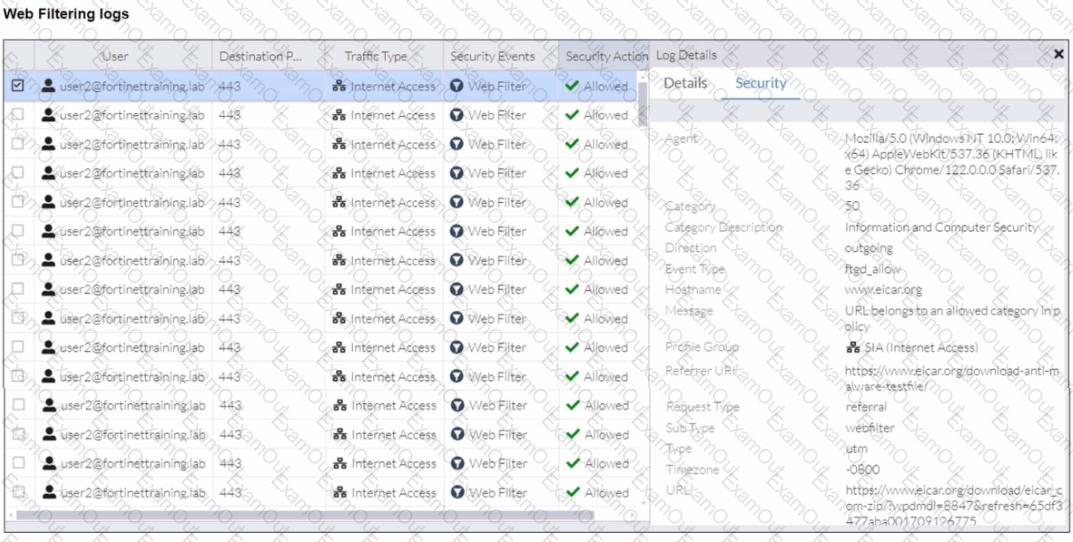
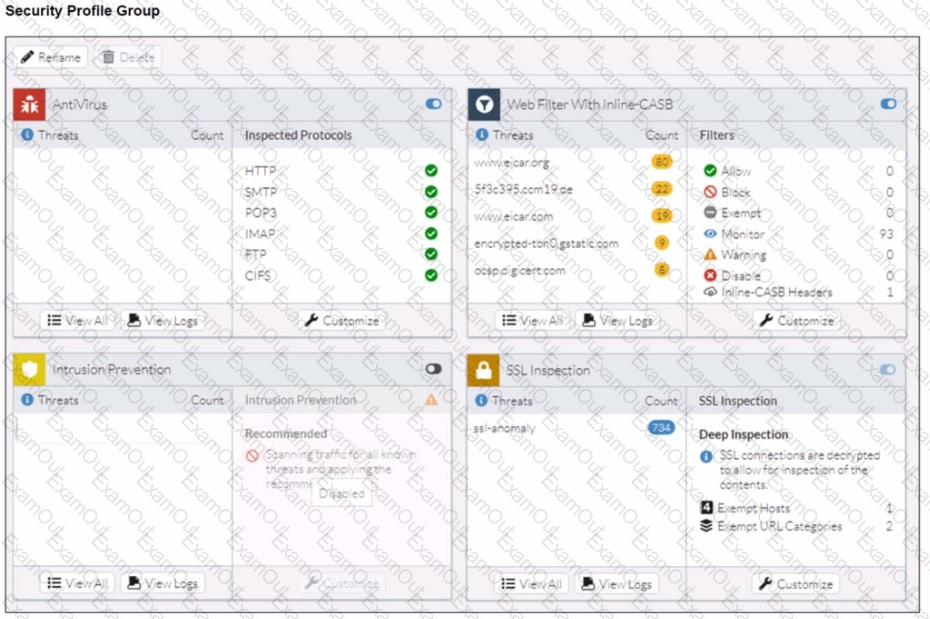
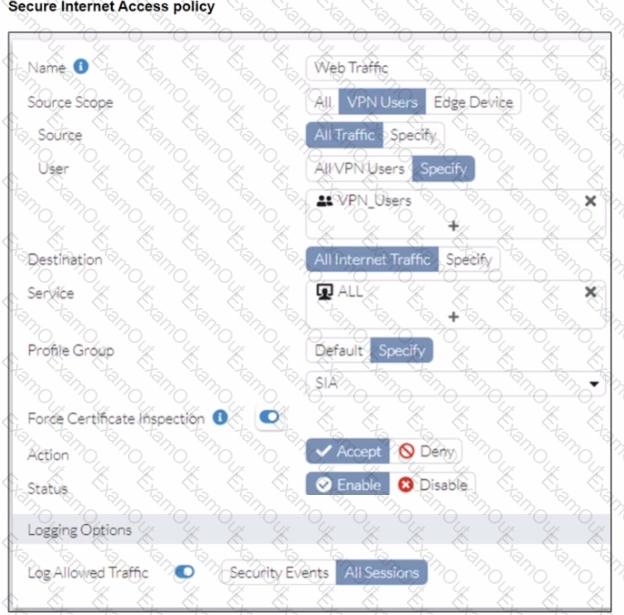
A FortiSASE administrator has configured an antivirus profile in the security profile group and applied it to the internet access policy. Remote users are still able to download the eicar.com-zip file from https://eicar.org. Traffic logs show traffic is allowed by the policy.
Which configuration on FortiSASE is allowing users to perform the download?
During FortiSASE provisioning, how many security points of presence (POPs) need to be configured by the FortiSASE administrator?
A customer wants to upgrade their legacy on-premises proxy to a could-based proxy for a hybrid network. Which FortiSASE features would help the customer to achieve this outcome?
Which two statements describe a zero trust network access (ZTNA) private access use case? (Choose two.)
In which three ways does FortiSASE help organizations ensure secure access for remote workers? (Choose three.)
An organization wants to block all video and audio application traffic but grant access to videos from CNN Which application override action must you configure in the Application Control with Inline-CASB?
Which two components are part of onboarding a secure web gateway (SWG) endpoint? (Choose two)
Which two deployment methods are used to connect a FortiExtender as a FortiSASE LAN extension? (Choose two.)
Refer to the exhibit.
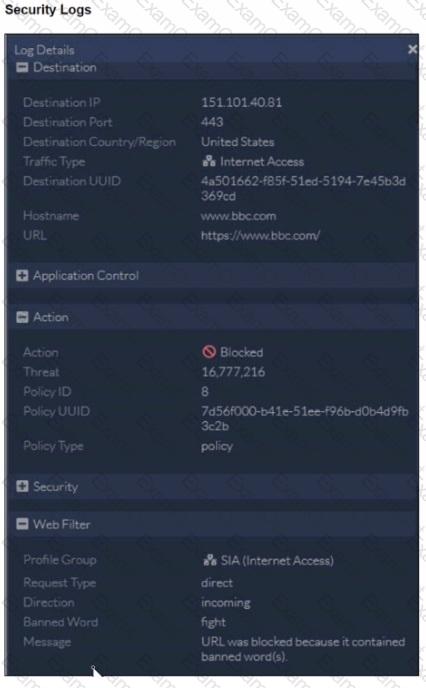
To allow access, which web tiller configuration must you change on FortiSASE?

