Refer to the exhibit.

What is the purpose of this section of an Azure Bicep file?
A Network security administrator is searching for a solution to secure traffic going in and out of the container infrastructure.
In which two ways can Fortinet container security help secure container infrastructures? (Choose two.)
Refer to the exhibit.

You are troubleshooting a Microsoft Azure SDN connector issue on your FortiGate VM in Azure.
Which command can you use to examine details about API calls sent by the connector?
Your DevOps team is evaluating different Infrastructure as Code (IaC) solutions for deploying complex Azure environments.
What is an advantage of choosing Azure Bicep over other IaC tools available?
An AWS administrator must ensure that each member of the cloud deployment team has the correct permissions to deploy and manage resources using CloudFormation. The administrator is researching which tasks must be executed with CloudFormation and therefore require CloudFormation permissions.
Which task is run using CloudFormation?
As part of your organization's monitoring plan, you have been tasked with obtaining and analyzing detailed information about the traffic sourced at one of your FortiGate EC2 instances.
What can you do to achieve this goal?
Your monitoring team reports performance issues with a web application hosted in Azure. You suspect that the bottleneck might be due to unexpected inbound traffic spikes.
Which method should you use to identify and analyze the traffic pattern?
Refer to the exhibit.
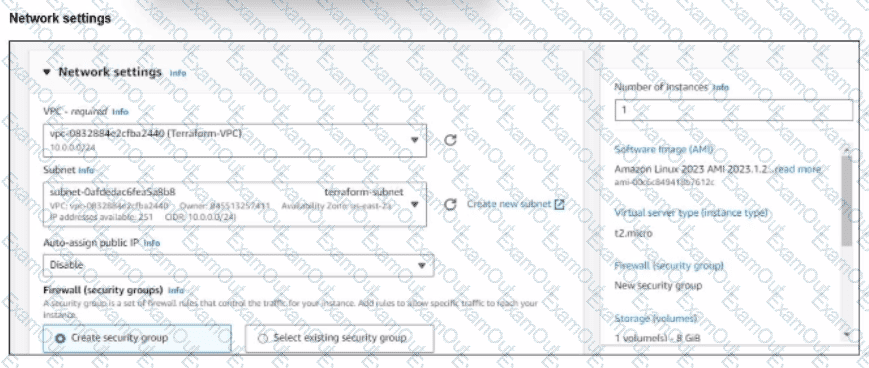
You have deployed a Linux EC2 instance in Amazon Web Services (AWS) with the settings shown on the exhibit.
What next step must the administrator take to access this instance from the internet?
Refer to the exhibit.

A senior administrator in a multinational organization needs to include a comment in the template shown in the exhibit to ensure that administrators from other regions change the Amazon Machine Image (AMI) ID to one that is valid in their location.
How can the administrator add the required comment in that section of the file?
An administrator decides to use the Use managed identity option on the FortiGate SDN connector with Microsoft Azure. However, the SDN connector is failing on the connection.
What must the administrator do to correct this issue?

