What are the modes of Data Ingestion on FortiSOAR? (Choose three.)
Refer to the exhibit.
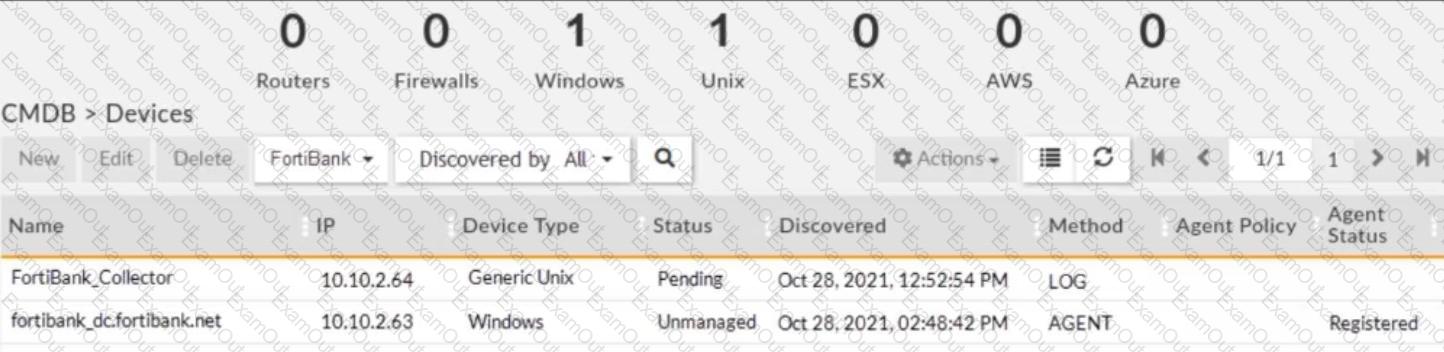
Is the Windows agent delivering event logs correctly?
Refer to the exhibit.
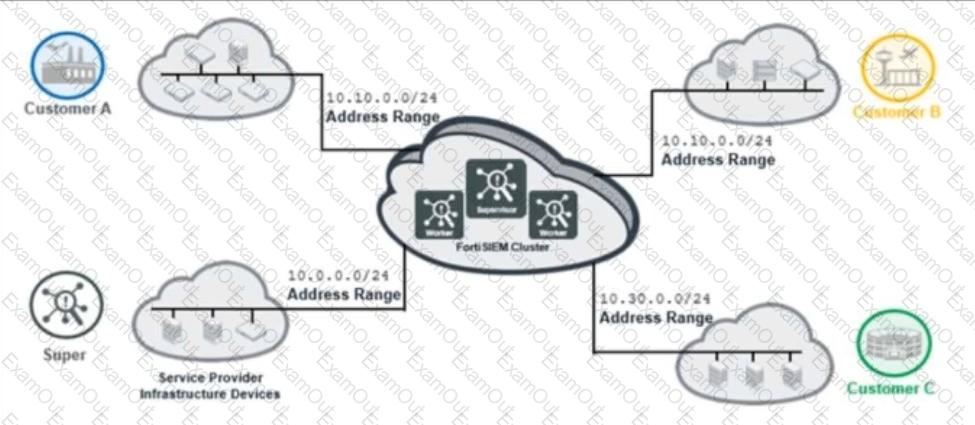
The service provider deployed FortiSIEM without a collector and added three customers on the supervisor.
What mistake did the administrator make?
Which three statements about phRuleMaster are true? (Choose three.)
Refer to the exhibit.
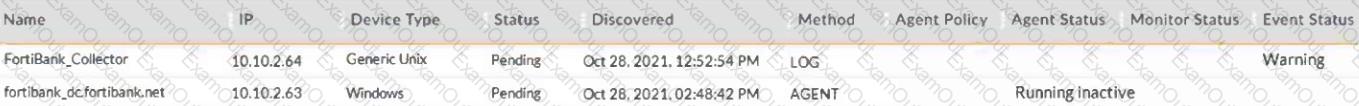
What are three possible reasons why theAgent StatusdisplaysRunning Inactive? (Choose three.)
Refer to the exhibit.
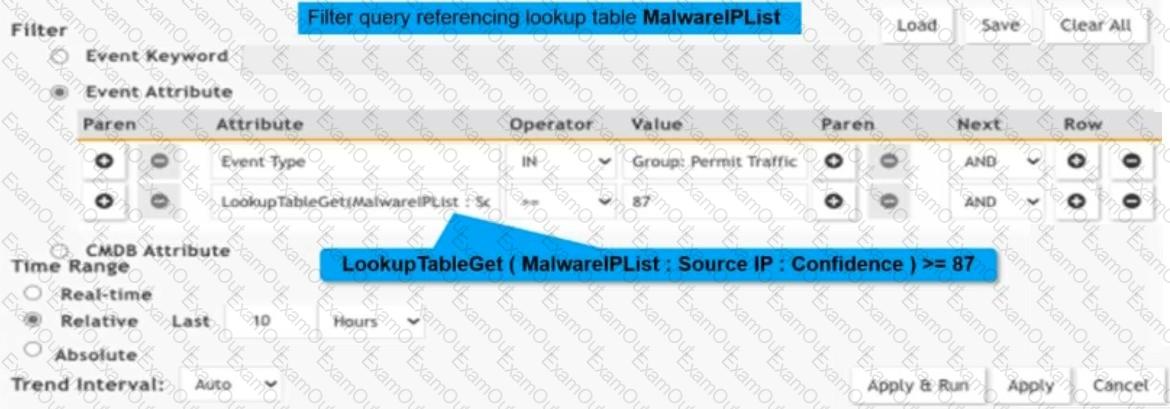
Consider a custom lookup tableMalwareIPList. An analyst constructed an analytic query to reference theMalwareIPListlookup table.
What is the outcome of the analytic query?
Refer to the exhibit.
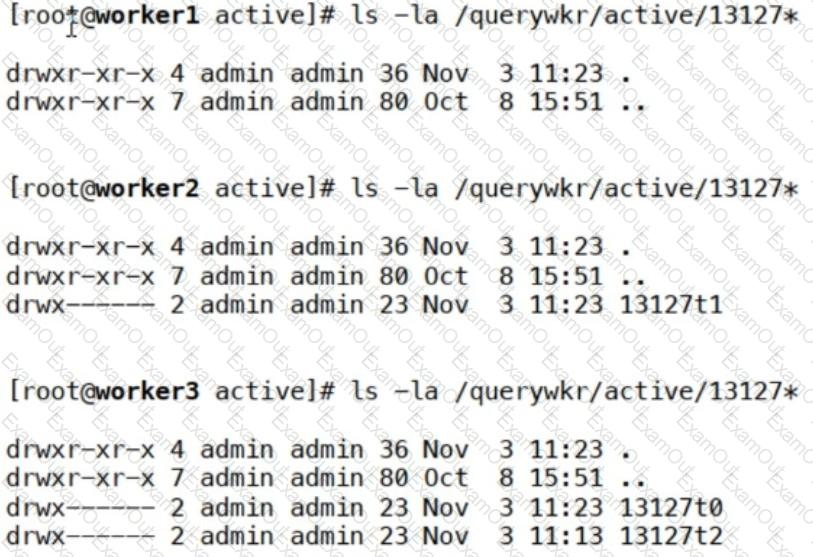
Which workers are assigned tasks for the query ID13127? (Choose two.)
Why do collectors communicate with the Supervisor after registration? (Choose two.)
Refer to the exhibit.
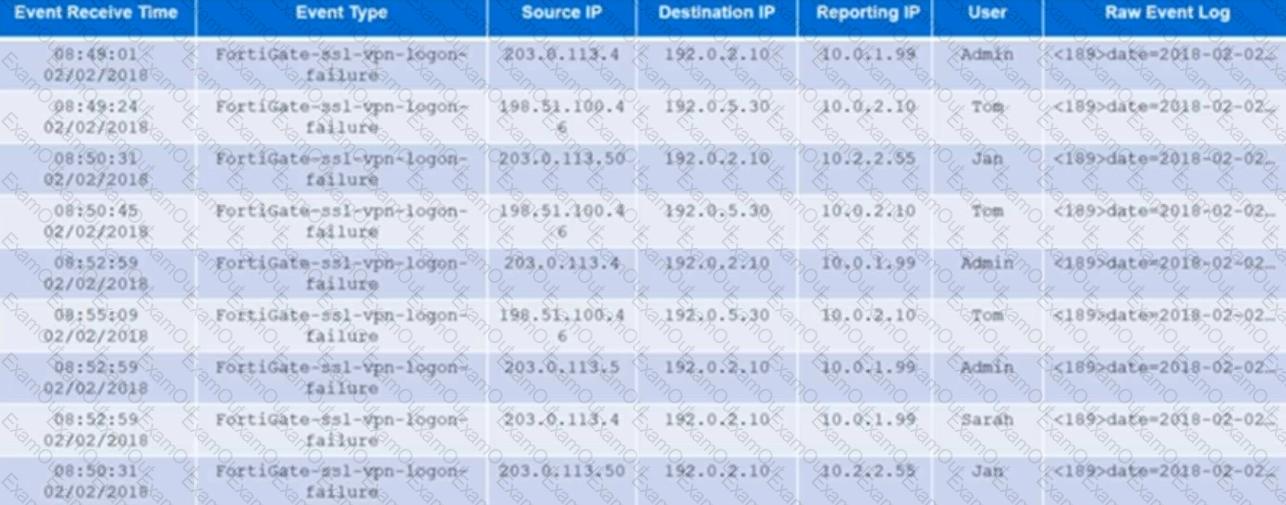
An administrator runs an analytic search for all FortiGate SSL VPN logon failures. The results are grouped by source IP, reporting IP, and user. The administrator wants to restrict the results to only those rows where the COUNT >=3.
Which user would meet that condition?
How can you customize the AI model on FortiSIEM?

 FortiSOAR ingests data when specific rules are triggered based on defined conditions.
FortiSOAR ingests data when specific rules are triggered based on defined conditions. This enables automation and intelligence-driven event ingestion.
This enables automation and intelligence-driven event ingestion. External applications canpushdata into FortiSOAR usingAPIs and integrations.
External applications canpushdata into FortiSOAR usingAPIs and integrations. This is useful forreal-time ingestionfrom external tools like SIEMs, ticketing systems, and threat intelligence platforms.
This is useful forreal-time ingestionfrom external tools like SIEMs, ticketing systems, and threat intelligence platforms. Data is ingested based onpredefined schedules.
Data is ingested based onpredefined schedules. This is useful for periodic polling of external systems, fetching logs, and running automated tasks at set intervals.
This is useful for periodic polling of external systems, fetching logs, and running automated tasks at set intervals. The output doesnotshow any subdirectories or task files (13127t0,13127t1, etc.), meaningWorker1 is not assigned any tasks.
The output doesnotshow any subdirectories or task files (13127t0,13127t1, etc.), meaningWorker1 is not assigned any tasks. The output showsone task (13127t1)under/querywkr/active/13127*.
The output showsone task (13127t1)under/querywkr/active/13127*. The workerhas only one assigned task, not two, so optionsC and D are incorrect.
The workerhas only one assigned task, not two, so optionsC and D are incorrect. The output showstwo tasks (13127t0and13127t1), indicating that Worker3 is processingtwo tasksfor query ID 13127.
The output showstwo tasks (13127t0and13127t1), indicating that Worker3 is processingtwo tasksfor query ID 13127. If aworker node fails, thecollector can temporarily store event logsand then forward them to the Supervisor.
If aworker node fails, thecollector can temporarily store event logsand then forward them to the Supervisor. This ensuresevent continuityeven during infrastructure issues.
This ensuresevent continuityeven during infrastructure issues. Thecollector sends health reportsto theSupervisor, including resource usage, connectivity status, and operational logs.
Thecollector sends health reportsto theSupervisor, including resource usage, connectivity status, and operational logs. This helps FortiSIEM trackcollector uptime and performance.
This helps FortiSIEM trackcollector uptime and performance.