Exhibit.
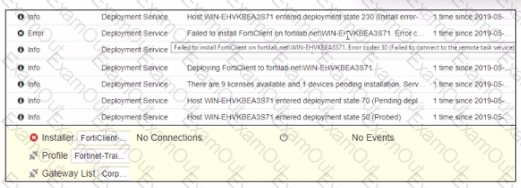
Based on the logs shown in the exhibit, why did FortiClient EMS tail to install FortiClient on the endpoint?
Refer to the exhibits.
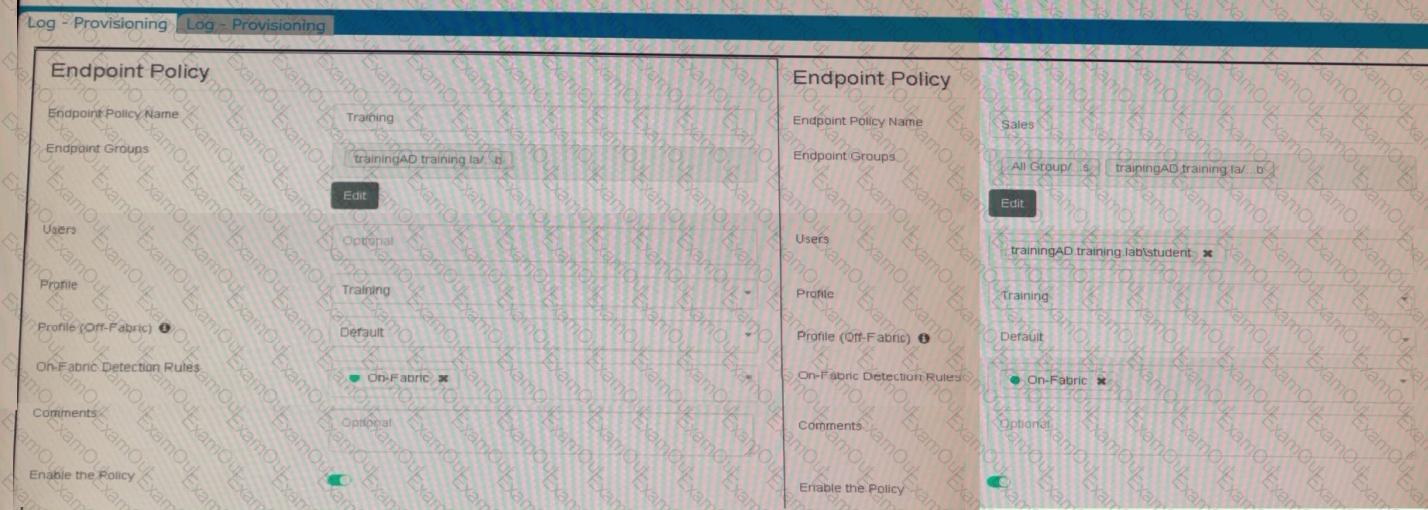
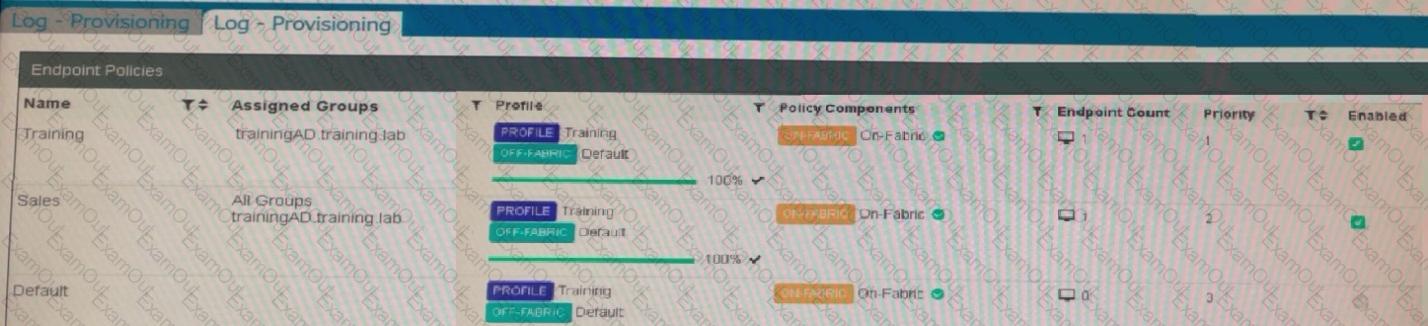
Which shows the configuration of endpoint policies.
Based on the configuration, what will happen when someone logs in with the user account student on an endpoint in the trainingAD domain?
Refer to the exhibits.
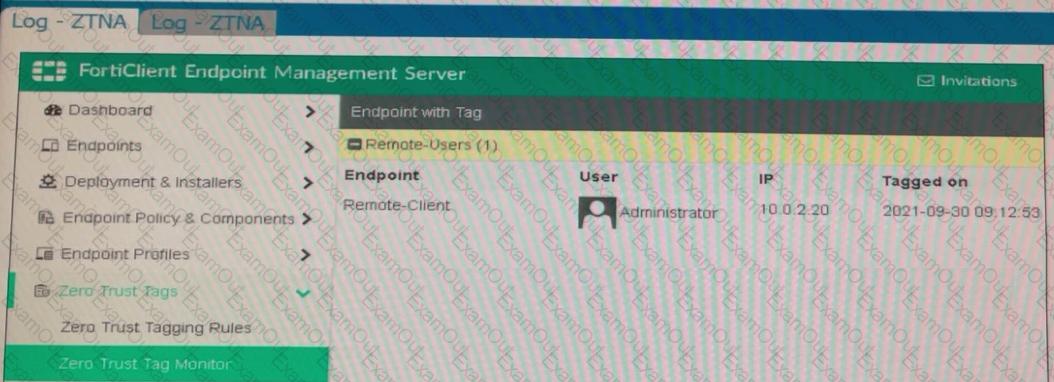
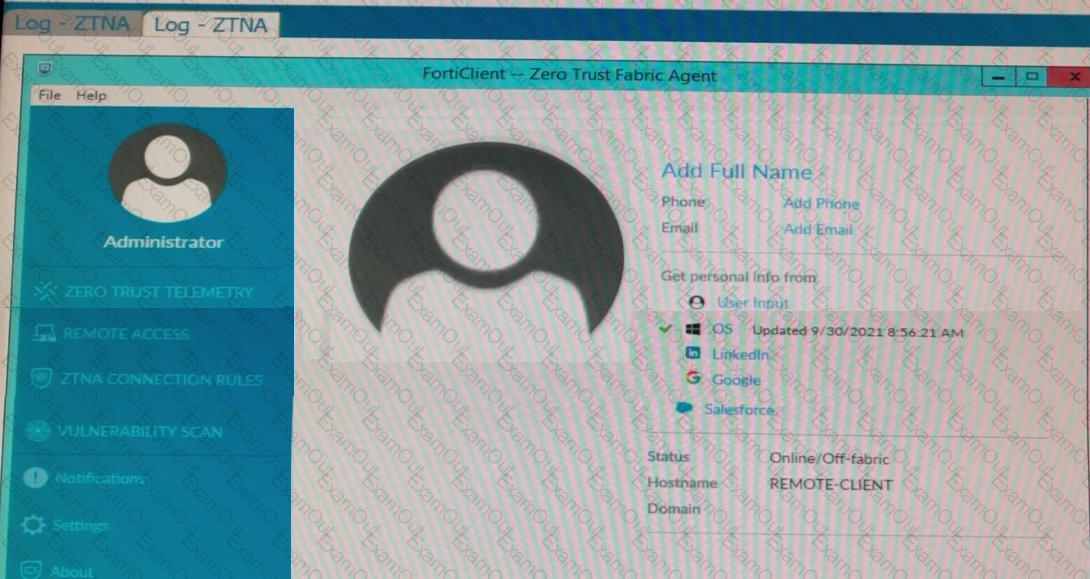
Which show the Zero Trust Tag Monitor and the FortiClient GUI status.
Remote-Client is tagged as Remote-Users on the FortiClient EMS Zero Trust Tag Monitor.
What must an administrator do to show the tag on the FortiClient GUI?
An administrator wants to simplify remote access without asking users to provide user credentials Which access control method provides this solution?
Which two are benefits of using multi-tenancy mode on FortiClient EMS? (Choose two.)
An administrator must add an authentication server on FortiClient EMS in a different security zone that cannot allow a direct connection.
Which solution can provide secure access between FortiClient EMS and the Active Directory server?
Refer to the exhibit.
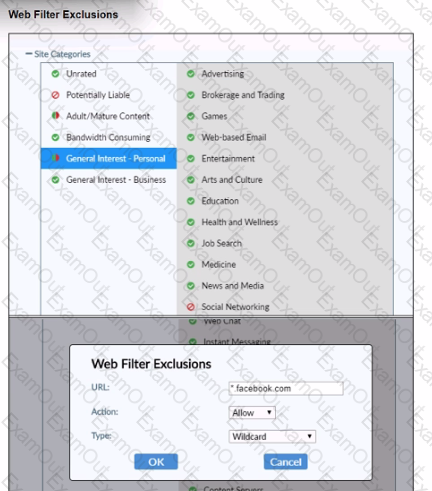
Based on the settings shown in the exhibit, which action will FortiClient take when users try to access www facebook com?
When site categories are disabled in FortiClient web filter, which feature can be used to protect the endpoint from malicious web access?
Which two statements are true about the ZTNA rule? (Choose two.)
Which statement about FortiClient comprehensive endpoint protection is true?

