Refer to the exhibit.
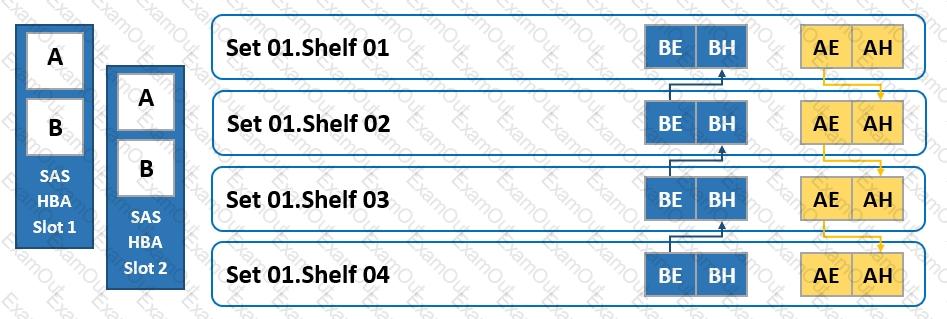
To which shelf and port should SAS HBA slot 1 port B be connected?
What is the preferred method to ensure backups are protected against deletion or corrupt?
A PowerProtect DD appliance with two expansion shelves is being installed in a customer-provided rack. When cabling the controller to the shelves, what is connected to the host port on the last shelf in the chain?
A technician is upgrading a DD9400 with a DS60 expansion shelf with 60 drives. In the GUI interface, only 30 drives are accessible.
What is causing these drives to be inaccessible?
What are some possible network bottlenecks for a PowerProtect DD?
Which component of PowerProtect DD is Data Invulnerability Architecture a feature of?

